If you’re reading this blog, I’m betting you’re a technology enthusiast and that you’ve heard of all the hottest innovations in wireless today. Whether it be the gargantuan increase in throughput-efficiency with Wi-Fi 6, the exciting new possibilities enabled by the Internet-of-Things (IoT), or the powerful yet easy-to-setup wireless home office solutions, they’ve all become a reality and are deployment-ready today!
This begs the question, what is the right wireless platform that will benefit us from these innovations?
Assuming you’ve caught up on the news, you’ve probably heard the commotion from the different wireless companies boasting about their flagship access points (AP), lined up with insane hardware specifications. Something on the lines of having 8×8 radios to support the densest of the client environments, being armed with some state-of-the-art chip that provides users with full visibility into the RF, and integration with their ultra-modern software application for complete network control. You might be thinking, soon enough, well, even some built-in AI software that will predict your future!
Jokes aside, what a time to be alive; all this incredible innovation, and it’s just a matter of time before they’re adopted by enterprises all over the world. However, are these flagship APs right for everyday people like us in our current situation?
It’s not news that most of us are working from home, so if your corporate adopts these new APs, we won’t be able to experience it for days to come. In addition to having a high price point, with standard smartphones and most laptops maxing out with just 2×2 radios, all that fancy hardware specifications on these APs are unfortunately overkill for a simple household anyways.
So, what platform should we use to support our remote working situation?
Introducing the Catalyst 9105
Well, I’m proud to present to you our newest and cutest AP in Cisco’s Wi-Fi 6 portfolio, the Catalyst 9105AXI (Infra model), and 9105AXW (Wall Plate Model). With robust 2×2 radios capable of performing Wi-Fi 6, state-of-the-art software supporting Cisco’s IoT solution, and an efficiently designed internal hardware enabling its small form-factor design, the Catalyst 9105 is not only the perfect AP for small to mid-size offices but also your home.
Figure 1. Catalyst 9105AXW (left) and 9105AXI (right)
With the Catalyst 9105AXI and 9105AXW having dimensions of just 5.9″ x 5.9″ x 1.2″ and 6.3″ x 3.5″ x 1.3″ respectively, these two APs are by far the smallest members of the Catalyst 9100 family. However, when we hear the word small, we automatically assume less powerful, but let me assure you; this platform is far from weak, so why don’t we speak a language that deters any skepticism. Let’s talk numbers.
Wi-Fi 6 with 2×2 Radios
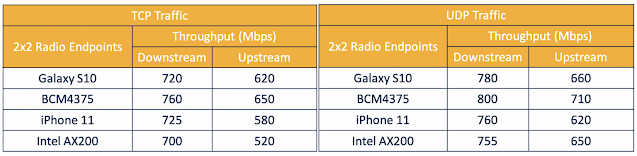
Before we get into the specific features of Wi-Fi 6, I’d like to set the stage by directly presenting to you the raw speeds the Catalyst 9105 can execute with single 2×2 Wi-Fi 6 endpoints associated with its 80 MHz channel. From the tables below, you can see that regardless of the endpoint’s model, each can achieve between 700 to 800 Mbps downstream and 500 to 700 Mbps upstream. For an access point smaller than an average book, these numbers are incredible.
Figure 2. Cisco internal Catalyst 9105 throughput test results
To bring it up a notch, let me ask you this. What is the first thing we think of when the topic of Wi-Fi 6 comes up? Faster speeds? Lower latency? Higher security? Less interference? How about all of the above, enabled by Wi-Fi 6 specific features such as OFDMA, BSS Coloring, Target Wake Time, WPA3, and 1024 QAM. Quite the list of innovations, and while both Catalyst 9105 models support each of these features, let’s focus on the most exciting one, OFDMA!
To my experienced wireless readers, why OFDMA is under constant spotlight comes as no surprise. However, for those who are new to wireless, OFDMA stands for Orthogonal Frequency-Division Multiple Access and, when enabled, significantly improves the wireless network’s efficiency in serving multiple clients at a time. Before OFDMA, we had OFDM, where a single wireless frame would take up an entire channel’s width for a certain period, essentially forcing each packet regardless of size to wait in a queue. With the introduction of OFDMA, the channel can now be shared by multiple packets simultaneously, enhancing the network’s ability to serve multiple endpoints in parallel.

Figure 3. OFDM vs Wi-Fi 6’s OFDMA
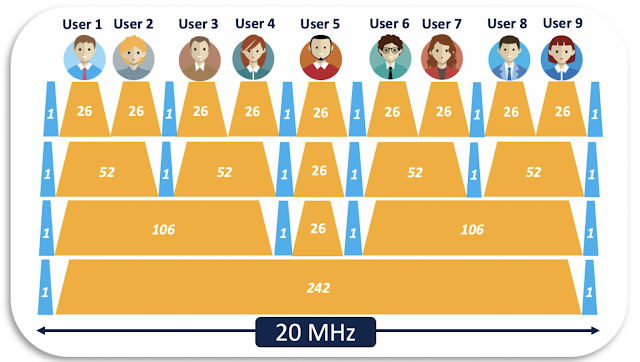
For a more technical explanation, let takes a 20 MHz channel, for example. When using OFDM, a 20 MHz channel has only a single subcarrier (consisting of 242 resource units). As an analogy, this can be interpreted as a one-lane highway, only capable of processing a single packet at a time. When it comes to OFDMA, the 20 MHz channel can be divided into a maximum of 9 subcarriers (consisting of just 26 resource units). The highway’s overall width that we’ve mentioned earlier remains the same but can be divided into multiple narrower lanes and are adjusted based on the incoming packets’ sizes. This means that an AP that supports the full capability of OFDMA can serve nine endpoints at the same time. Since the Catalyst 9105 is intended for less dense environments, it’s designed to support four endpoints in parallel, which is not only incredible, it’s revolutionary for an AP of this size.
Figure 4. A 20MHz channel divided into resources units with OFDMA
To prove what I said is not just colorful marketing, let’s talk numbers. We’ve had Miercom, the well-known third-party network testing firm, run performance tests with Cisco’s 9105, Aruba’s AP505, and Ruckus’s R550 with OFDMA enabled to compare performance. During the test, the APs were first loaded with ten endpoints and gradually up to eighty endpoints passing traffic in parallel. You’ll observe that Cisco’s 9105 maintained a significantly superior throughput lead from the graph below than the other two vendor’s APs. In fact, you’ll observe that even with 80 endpoints associated, Cisco’s 9105 can provide almost the same throughput experience as the other vendor’s APs with just ten endpoints associated. The takeaway is obvious, while the Catalyst 9105 is small in size, it is mighty!
Figure 5. Miercom’s scaled multi-vendor OFDMA TCP performance test
Innovation within the Internet of things
But apart from the raw ability to execute Wi-Fi exceptionally, the Catalyst 9105 will also seamlessly fit into any business’s IoT solution. For readers unfamiliar with the Internet of Things, it’s the ability to leverage a wireless network to monitor and transfer data through smart devices, allowing the user to accomplish tasks in an efficient and often automated manner. Many of you probably have IoT devices in your home right now, such as a Google Home, Amazon Alexa, or a Nest thermostat. These devices being both user-friendly and practical in function, have naturally become an integral part of our day-to-day lives. This seamless enhancement is precisely what the Catalyst 9105 can accomplish but, on an enterprise-level, creating powerful yet fiscally efficient IoT solutions.
So, why do we need this? What problem are we solving?
As you can imagine, for an IoT solution to operate on an enterprise level, it requires an intricate control network that provides full visibility into every corner of the solution to ensure security. However, given that all enterprises will already have a pre-existing network, building a separate one for dedicated IoT usage is costly, complicated, and redundant.
This is where Cisco’s Application Hosting on the Catalyst Access Point feature solves these problems. Customers can now acquire custom Dockerized IoT applications from Cisco’s Solution Partner Marketplace, load them into the built-in containers on the Catalyst 9105 through Cisco DNA Center, and use them as IoT gateways to begin communicating with surrounding IoT devices.
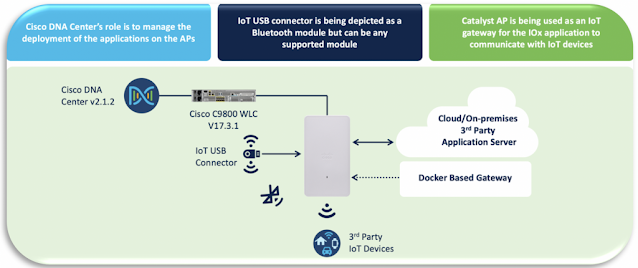
Figure 6. The Catalyst 9105AXW integrated with Cisco’s Application Hosting IoT Solution
By allowing users to utilize their existing low-cost Catalyst 9105 network for IoT, it eliminates the looming pain of building a second network for IoT management. Integrating this solution with Cisco DNA Center, users now have an application life cycle manager that provides them full visibility into the deployment status of each IoT application. In fact, Cisco DNA Center allows users to deploy different applications to different areas of their Catalyst 9105 network, providing the ability to support multiple IoT solutions on a single network!
When it comes to real-life IoT use cases, the possibilities are endless. They can range from retail optimization with electronic shelf labels to motion sensors or cameras for building management systems and even medical wearables for health care solutions. The best part of all this is that it can be automated, creating a genuinely self-sufficient IoT solution.
Wireless Home Office Solution
Up to this point, we’ve reviewed the Catalyst 9105’s Wi-Fi 6 and IoT capabilities; however, the caveat is that most of us are still working remotely, so how can we benefit from these innovations?
As hinted earlier, the Catalyst 9105 can be deployed directly in your home. With Cisco’s remote worker solution, simply connect your Catalyst 9105 to your home network, and it will automatically associate with your company’s corporate Wireless LAN Controller (WLC) and begin broadcasting your corporate’s SSID in Wi-Fi 6.
Can it really be this easy?
Absolutely, and the solution is simple, we use Cisco’s day-0 provisioning solution, Plug-n-Play (PnP). Before shipping the AP to the end-user, the network administrator managing this solution simply needs to create a profile for this AP on Cisco’s PnP Connect cloud portal, then point it to the IP address of the company’s WLC. When the AP receives an IP address, it’ll automatically know to reach out to Cisco’s PnPConnect server through its built-in PnP agent code and will get re-directed to and join the WLC. The fact is, only step one in the diagram below is executed by the end-user; the remaining steps are completely black-boxed, making the workflow incredibly simple.

Figure 7. Remote worker solution’s three-step onboarding process
It’s no doubt convenient, but is it secure?
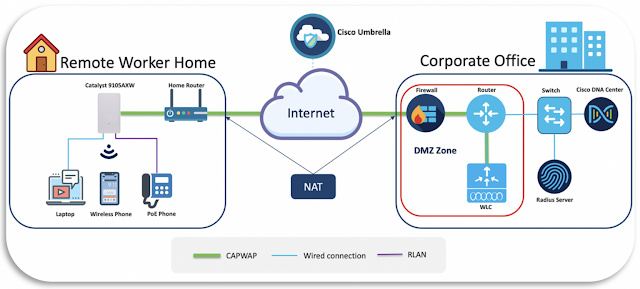
It’s a resounding yes, and to explain, let’s refer to the architectural diagram below. The left side of the diagram depicts a user’s home network, and you’ll observe the deployed Catalyst 9105 can associate to the corporate office’s WLC (sitting in a public DMZ) through NAT. This connection is not only secured by Cisco Umbrella but also DTLS encrypted, meaning it has the highest level of security segmentation possible.
After the Catalyst 9105 joins the WLC, it can now utilize all its back-end infrastructure, such as the radius server for corporate 802.1x network access, and even Cisco DNA Center. With Cisco DNA Center, the network administrator managing the remote worker networks can leverage features such as Network Assurance and Intelligent Capture to monitor and troubleshoot any issues in the case that they occur, ensuring a phenomenal end-user wireless experience.
Figure 8. Remote worker solution architecture
By combining this wireless trifecta of Wi-Fi 6, Internet-of-Things, and remote worker solution, the Catalyst 9105 is not only a powerful and versatile small form-factor AP, but a multipurpose networking hub, and indeed a force to be reckoned with.