Nothing in the world is as it once was. Things we used to take for granted—such as dining out, going to the movies, or throwing birthday parties for four-year olds—are forever changed. However, as personal as those changes are, nothing compares to the tectonic shift that has occurred in work. Prior to the pandemic, the percentage of people working remotely was in the single digits. Today, it’s more than 60% in some industries. And, in a recent study, 70% of employees said they would quit their jobs if they couldn’t work from home at least a few days a week.
For knowledge workers, the benefits are many—from no commute to learning to bake bread. But companies benefit as well. Productivity and morale have gone up, and facilities costs have gone down.
Without the cloud, this overnight shift would have been impossible. The cloud makes it easier for users to access their applications and information from anywhere—just click and go. But, for IT departments, it’s not so simple. More clouds, more users, more locations and more applications—often built with application mesh—lead to more complexity. And complexity is rarely easy to master.
This is where Cisco can help.
Due to the breadth of our portfolio, we’re uniquely positioned to help you harness the power of your clouds. Cisco solutions align with the way you actually use the cloud to deliver a consistent experience to all users, connect multiple clouds, support the future of work, secure your cloud workloads and simplify cloud operations.
In this blog, the third in a series of five, we’ll take a look at how companies using the cloud need to think about work differently. We’ll talk about what that looks like, the challenges involved and how Cisco can help.
Over the next few weeks, we’ll roll out more blogs to highlight other ways you use the cloud.
An Unplanned Social Experiment
The “work from home” question has been quietly argued for more than a decade. While technology made it possible, there was a wide range of sentiment on whether it was more or less productive. Then COVID. During this forced social experiment, the question stopped being a question. Employees had to immediately pull up stakes and decamp for home.
Nearly two years later, as offices slowly start to open, we’re starting to rethink the future of work. This won’t be a simple question about working from the home or the office, because the future of work is hybrid. Where some will work full-time on site. Others full-time off site. And still others will work in a mixed mode – moving between locations on any given day or time. And it all cases, working better.
H-m-m. Kind of sounds like something the cloud is good at making possible.
The cloud, by its very nature, supports both the agility and the location-independent needs of hybrid work, which requires a set of capabilities optimized for secure, consistent delivery—regardless of location. That’s why cloud has played such a huge role in the business response to the pandemic. Let’s take a look at what that means for a hybrid work future.
Home at the Office
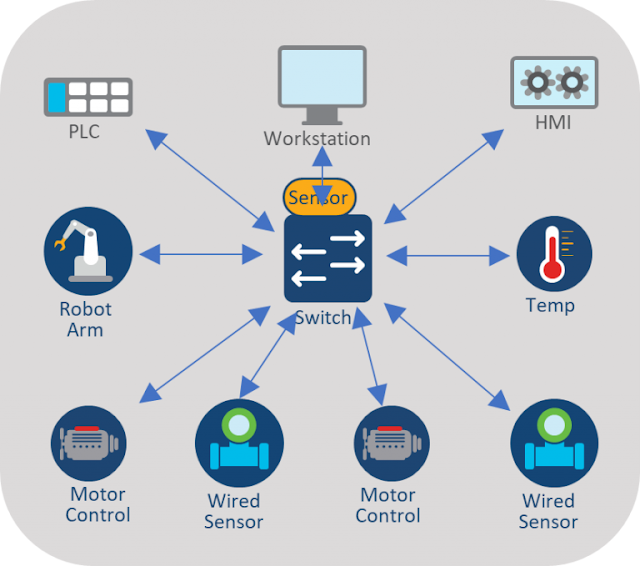
Perhaps the best way to think about hybrid work is to re-think what an office is. Companies used to think of campus and branch offices. Simple enough. Now add hundreds or thousands of home offices. Not so simple. Every home office is effectively a branch office for one person—with the same demands for application performance and secure access but with substantially fewer IT resources.
Let’s start with secure access. As mentioned in an earlier blog, security and access are often at odds. The employee wants access that’s easy to use. If it’s difficult to connect, the employee may become frustrated and work around the security measure, actually increasing risk.
The company and its IT department understand the need for easy access but their larger concern is security. And easy access can imply it’s easy for anyone to get onto the network—including bad actors.
I outlined the key elements for secure access in my last blog, including policy, segmentation, zero trust framework and malware detection.
Application Experience
Application experience is critical as employees work from home. The employee is going to expect the same application experience they’ve come to know when they’re in the office. Anything less will negatively impact productivity and employee satisfaction.
Quality application experience doesn’t just happen. It demands new levels of visibility as applications become more distributed. This visibility starts with application components in the service mesh where developers need to see where each component of the application resides and how they connect at the user to deliver the application. You need to be able to see this journey from cluster to user to see where any potential application component performance issue may reside.
These distributed applications often connect over the internet via infrastructure that the company doesn’t own or manage. Each hop in that journey can negatively impact the overall application experience. As a result, you need to have visibility that follows the application through the infrastructure. More importantly, you need to augment that visibility with artificial intelligence that can turn simple visibility into actionable insights. Cisco ThousandEyes, AppDynamics and Intersight moves you beyond domain monitoring into end-to-end visibility, insights, and actions. They transform siloed data into actionable insights to help IT teams optimize for cost and performance, maximize digital business revenue, and deliver exceptional digital experiences—anywhere on the cloud.
Office Intrigue
As more employees head back to the office, companies have an important decision to make. Do they opt for the short term fix and simply do what they’ve always done. Or do they invest in the long term and build out the office of the future. And, in the long term, cloud is a key consideration.
As companies plan for the future, many have indicated that employees will work from home two or three days per week and in the corporate office the rest of the week. Those days in the office won’t be a replay of the past. This will impact how facilities are managed and applications are delivered.
The number of employees on-site and the hours they work will vary widely. As a result, corporate facilities will have to be able to cost-effectively support a hybrid workforce. The office will need to be able to accommodate this ebb and flow of employees—both in space and in network capacity.
The variability of used space is an important consideration for smart buildings and IoT devices to improve energy efficiency based on occupancy. There is some cloud component of this. However, the bigger cloud element may be IT capacity. As companies move to the cloud, they may rethink how to provision the workspace infrastructure. Rather than build out their network for a full complement of employees, they may consider a smaller investment and use the cloud to support their peak occupancy.
The workload in the corporate offices will also change. With a hybrid work environment, 60 percent or more of the participants in a meeting will be working off site. As a result, the cloud-based, distributed applications used from the home office need to seamlessly connect with the applications in the office. Essentially, hybrid cloud connectivity.
The bottom line, there will be more demand for distributed applications and collaboration even with the return to office. The applications themselves must promote better collaboration for a hybrid workforce. And the application performance—as discussed above—must be comparable between the on-site and off-site participants. Solutions such as Cisco Intersight or Cisco Nexus dashboard which can help manage your cloud network operations are essential for a seamless end user experience for any workload across any infrastructure whether on prem, multi cloud or edge.
Will every company look like this? Doubtful. No two companies have ever looked the same. As with everything surrounding this pandemic, no one really knows the shape of the final solution. And every company will determine their path forward. However, we do see trends coalescing around a hybrid work model. And that will only accelerate the demand for effective cloud solutions such as those available from Cisco.
Source: cisco.com