As applications become distributed across clouds, data centers, SaaS, and to the edge, enterprises need to enable secure access to these applications for their workforce from anywhere. Implementing Secure Access Service Edge (SASE) is a preferred method for enabling secure access to distributed applications by a hybrid workforce and the growing number of IoT devices.
Zero trust is one of the most common starting points for enterprises that are embarking on their SASE journey. Many enterprises are either in the process of adopting zero trust or have already adopted it. The initial transition was primarily driven by a large number of remote workers as a result of the pandemic. However, many enterprises are now transitioning to hybrid environments with the workforce distributed from campuses to branches to home offices.
This hybrid work environment, along with increasing reliance on distributed cloud and SaaS applications, requires a network architecture that provides scalable and distributed zero-trust security enforcement close to endpoints and people using them. This maximizes bandwidth utilization of the WAN link while ensuring that there is no central choke point where all the traffic needs to be redirected. In addition, in order to thwart real-time threats, IT needs the network to continuously monitor and assess the security posture of devices after application access is granted.
The latest enhancements in the SD-WAN security architecture are designed to support this new paradigm of distributed applications and hybrid workforces. Now, the tight integration between Cisco SD-WAN and Cisco Identity Services Engine (ISE) enables IT to employ zero trust security functions for the traffic that goes through an SD-WAN fabric.
Cisco ISE Configures Security Posture in SD-WAN Fabric for Zero Trust
Delivering a Zero Trust methodology for SD-WAN traffic requires four key functionalities: application access policies based on the desired security posture (who can access what); security controls for admitted traffic; continuous enforcement; and immediate adaptation to security posture changes—all enforced with a consistent model for on-prem, mobile, and remote devices and workforce.
Cisco ISE supports the configuration of security posture policies in SD-WAN fabric. When a person’s device or an IoT endpoint connects to the network, the posture of the device is evaluated based on the configured policy, and an authorization decision is made based on that outcome. For example, an outcome of a device posture evaluation can be compliant, non-compliant, or unknown. This outcome of device posture evaluation determines an authorization policy, which can include the assignment of a Security Group Tag (SGT) and other authorization attributes to the device and owner. Details about how this is configured in Cisco ISE are captured in this technical article and video.
In addition, Cisco ISE shares the security group tags and session attributes with the Cisco SD-WAN ecosystem. This information can be leveraged by IT to create identity groups and associate security policies in Cisco vManage to enable access by specific user groups to applications over the SD-WAN fabric all the way to the edge.
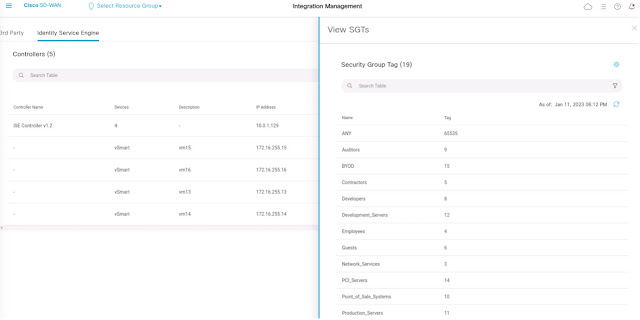
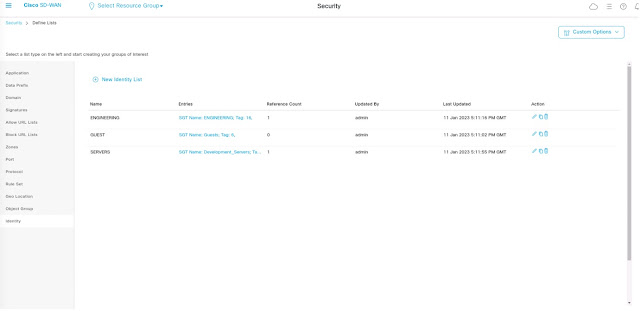
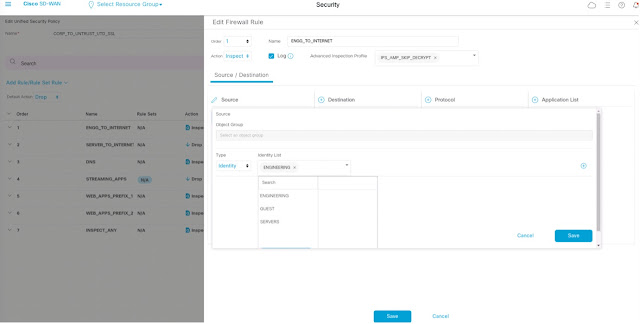
The images of Cisco vManage console in Figures 1 – 3 illustrate the process of how Cisco vManage learns a set of security group tags from ISE.
Figure 1: Identity groups pulled from ISE and shown in Cisco SD-WAN vManage
Figure 2: Creation of identity lists which includes a group of security groups – identity lists are used in the security policy configuration
Figure 3: Security policy configuration based on identity lists
Monitoring of Security Posture Guards Against Attacks
Cisco ISE also supports a periodic reassessment of device posture. Any change in the posture will cause a change of authorization which results in a different security policy being implemented in the SD-WAN edge. This enables the network and endpoints to work in unison to enable zero trust capabilities. Following are three use cases to illustrate what is possible with the deep integration of Cisco ISE and SD-WAN solutions.
◉ IT can configure a posture policy that requires an Anti-Malware Protection (AMP) agent running on endpoints to identify malicious files. When the owner of a device connects to the network, the posture is evaluated and determined to be compliant with a running AMP agent. The compliant status results in a specific SGT being assigned to the traffic and associated authorization access. As an added benefit in this case, SD-WAN router will not execute the network AMP functionality when it is being run on the endpoint. However, if the AMP process on an endpoint is terminated either voluntarily or involuntarily, ISE will detect this through periodic posture assessment. The endpoint’s non-compliant status will result in a more restrictive SGT being assigned. On the SD-WAN router, a policy for non-compliant traffic will result in the execution of the network-based AMP function for the traffic originating from that endpoint. As a result the network and end-point work in unison to ensure that the right policies continue to execute properly.
◉ IT can configure posture policy that prevents the insertion of a USB device in an end-point. When a device connects to the network without a USB attached, the posture is evaluated by ISE as compliant, and therefore traffic from the device is allowed to pass through the network. If a USB is connected to the device, ISE will immediately detect the non-compliant status and do a change of authorization, assigning a different SGT which can be used by the SD-WAN edge to block all traffic from the device as long as the USB is attached.
◉ With Software-Defined Remote Access (SDRA), another key technology of Cisco SD-WAN, the traffic from remote workers and their devices is processed by the SD-WAN edge as well as subjected to ISE posture evaluation. This means that all the functions for accessing applications based on posture are applicable and available to both on-prem and remote endpoints.
Start the Journey to SASE with Zero Trust-Enabled Cisco SD-WAN
Cisco SD-WAN connects the workforce and IoT devices to any application using integrated capabilities for multicloud, security, and application optimization—all on a SASE-enabled architecture. Zero trust is a key capability of SASE, along with SD-WAN, enterprise firewalls, a cloud access security broker, secure web gateways, malware protection, intrusion prevention system, URL filtering, and DNS-layer protection.
As organizations make progress on their journey to SASE, Cisco SD-WAN’s rich security capabilities enable Zero Trust functions across SD-WAN traffic to secure the network and devices in a scalable, optimal, and cost-effective way.
Source: cisco.com