From work style to vehicle choice, hybrid has become the new norm. In fact, we are surrounded by use cases that need a hybrid approach to problem solving. And as we all know, networks are evolving. Today, networks need to be ready for new and growing applications such as artificial intelligence (AI), augmented and virtual reality (AR/VR), edge clouds, online gaming, connected cars, and video streaming. As a result, communication service providers (CSPs) are considering more options in redesigning networks.
For example, network operators need to cater to their customers by delivering services from anywhere between 1G to 100G speeds, while having the ability to aggregate into 400G networks. Operators need a platform that allows them to bridge this gap from 1G to 400G.
Platform design choices
Typically, there have been two types of form factors for routing platforms: fixed and distributed systems.
Fixed systems can contain a single forwarding chip and single route processor (RP) with fixed interfaces (see Figure 1). Fixed systems typically come in a “pizza box” form factor that is often used in network architectures that are more predictable and simpler, where using a system with fixed interfaces is suitable for anticipated network traffic patterns.
Figure 1. Fixed system
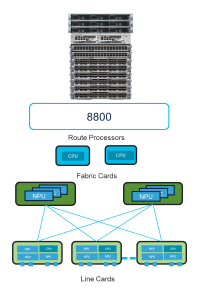
Distributed systems use a different architecture (see Figure 2), where the packet-forwarding decisions and actions take place on the network processor units (NPUs)/forwarding engines located on the individual line cards. Each card maintains a copy of the forwarding information base (FIB) that is distributed by the RP in the control plane. Large distributed systems have traditionally been designed to provide higher total system bandwidth and port densities, field-replaceable line cards, interface diversity, and redundancy.
These requirements have far exceeded what could be accomplished with a single NPU on a fixed system, which is why every line card has multiple NPUs participating in the forwarding decisions. This architecture helps deliver favorable customer outcomes with increased reliability and flexibility.
Figure 2. Distributed system
New hybrid choice with centralized architecture
With the evolution of the network and emergence of more localized and metro-driven traffic patterns, there is a need for network operators to deploy a solution that meets the needs of both fixed and distributed systems. Cisco 8000 Series Routers address this customer problem and market need by delivering a platform that is uniquely positioned to support the reliability and flexibility offered by distributed solutions, while also delivering value with the customer investments.
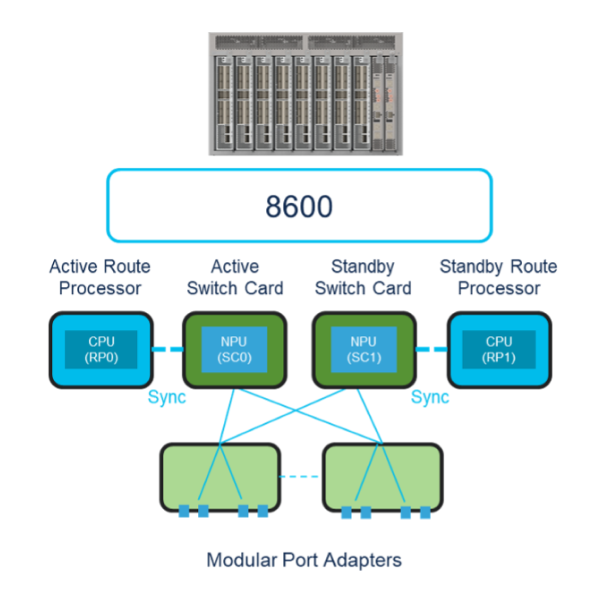
Instead of having to choose between a fixed or distributed system, customers can now also consider the new centralized system with Cisco 8600 Series Routers (see Figure 3), which blend the resource efficiency of fixed systems with the interface flexibility, upgradeability, and redundancy of distributed systems.
Figure 3. Centralized system
Similar to distributed systems, centralized systems have in-service, replaceable, redundant RPs with CPU and redundant switch cards (SCs) with NPUs to support both data plane and control plane redundancy. Cisco 8600 Series Routers have modular port adapters (MPAs) that can be replaced while in service and enable interface flexibility. Like fixed systems, the forwarding decisions on centralized platforms are handled centrally on the RP/SC instead of the line card.
With the unique centralized design of Cisco 8600 Series Routers, the life of a data packet is carefully managed such that when traffic ingresses on one of the MPA interfaces, the physical layer (PHY) on the ingress MPA sends the traffic to both SCs. The Silicon One ASIC on both SCs processes the packets, so in the event of a failure with the active SC, the other standby SC always has all the packets to support data plane redundancy. At a point in time, only the packets processed by the active SC are forwarded to the network, and packets processed by the standby SC are dropped.
Use cases
With currently over five billion global internet users, it is becoming increasingly impractical for capabilities such as peering to happen at only traditional, centralized internet exchanges. Distributed peering points are emerging across the network to help avoid unnecessarily backhauling traffic to centralized locations. However, metro locations such as colocation sites, data centers, and central offices can be space-constrained, and every additional rack unit (RU) of space is extremely costly.
Deploying right-sized platforms like Cisco 8600 Series Routers can address some of the operator resource challenges while achieving lower upfront costs, data plane and control plane redundancy, port diversity, and architectural simplicity using single-chip forwarding with less components to help lower TCO.
Additional use cases for the Cisco 8608 router include as a core label switch router (LSR), routed data center top-of-rack (ToR)/leaf, and aggregation for cloud and CSP networks. Cisco 8600 Series Routers are also part of the Cisco routed optical networking solution, with support for 400G DCO optics to improve network operational efficiency and simplicity.
Cisco innovations
Cisco Silicon One offers unmatched flexibility with a common silicon architecture, including software development kit (SDK) and P4 programmable forwarding code across multiple network roles (see Figure 4), while supporting fixed, distributed, and centralized systems (see Figure 5). With Cisco Silicon One used in Cisco 8600 Series Routers, we maintain the architectural simplicity and uniformity across the three architecture types. Having a unified architecture helps network operators simplify operations through consistency with upgrades, feature parity, training, testing/qualification, deployment, and troubleshooting.
Figure 4. Cisco Silicon One portfolio and network roles
Figure 5. Form factor types using Cisco Silicon One
Silicon One architecture achieves high performance and full routing capabilities without external memories. The clean-sheet internal architecture includes on-chip high-bandwidth memory (HBM) and supports multiple modes of operation by enabling a router to operate with a single forwarding chip, a line card network processor, and a switch fabric element. This flexibility enables consistent software experience in multiple roles and rapid silicon evolution.
Benefits of simplicity and uniformity across the three architecture types for network operators include:
- Consistent software experience across multiple network nodes.
- Simplified network operations through consistency with upgrades, qualification, deployment, and troubleshooting.
- Unified security and trust across the network.
- Programmable interfaces via consistent APIs.
In addition to the capabilities of the Silicon One chipset, Cisco 8600 Series Routers include significant innovations, such as the Cisco IOS XR network operating system (NOS) and the chassis design itself. For example, Cisco 8600 Series Routers enable all major components to be in-service field-replaceable, which helps reduce operational costs.
The single-forwarding chip design on Cisco 8600 Series Routers is well suited for smaller locations by offering simplicity through more bandwidth with fewer components, which helps streamline costs, power, and space (including with chassis depth of less than 600 mm) while also reducing latency.
The first platform in the Cisco 8600 Series Routers product line is the Cisco 8608 router, which includes these components:
- Chassis: The router has an eight-slot 7RU chassis at 580 mm depth, which hosts fans, power supplies, RPs, SCs, and MPAs.
- Route processor: The RP hosts the CPU complex and the I/O ports. RPs fit vertically in the chassis from the front panel. Up to two RPs are supported in the system and the RPs operate in active-standby mode for a redundant system.
- Switch card: SCs sit orthogonally in the back of the MPAs with connections to all MPAs. SCs directly host the NPUs, with up to two SCs in the system that work in active-standby mode to deliver data plane redundancy.
- Power supplies: The router has four power supplies that can provide redundant power to the system. The power options include pluggable 3.2 KW AC and pluggable 3.2 KW DC.
- Fans: There are eight fans in the system, with each fan individually removable or replaceable to provide N+1 fan redundancy to the system.
- Modular port adapters: With a high degree of flexibility, the Cisco 8608 router supports a diverse range of interfaces, including 4×400 GbE, 24×10/25/50 GbE, and a combination of 16×100 GbE or 12×100 GbE+1×400 GbE or 8×100 GbE+2×400 GbE.
- Network operating system: Cisco IOS XR is the common NOS across access, aggregation, edge, and core platforms, including Cisco 8600 Series Routers. IOS XR provides network intelligence, programmability, and trustworthy solutions to help deliver operational efficiency.
- Manageability: Cisco Crosswork Network Automation is a comprehensive software platform that helps plan, provision, manage, optimize, and assure multi-vendor/multi-domain networks, including Cisco 8600 Series Routers, to help reduce operational costs.
Customer benefits
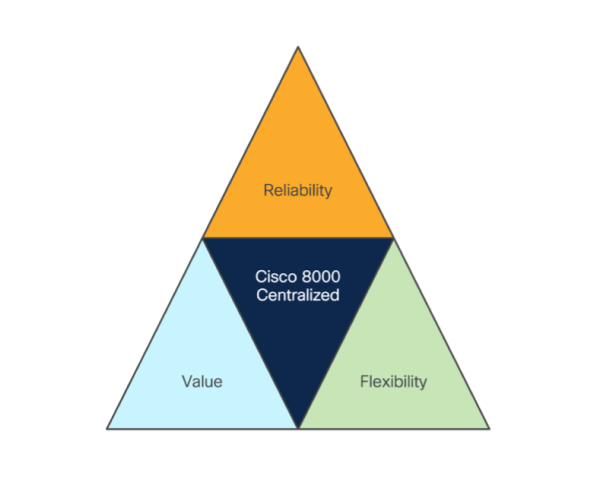
The centralized architecture of Cisco 8600 Series Routers enables customers to take advantage of three main benefits (see Figure 6), including:
- Reliability: The unique hardware architecture provides industry-leading reliability with both control plane and data plane redundancy without loss of any front face plate.
- Flexibility: In-service upgradability and mix-and-match port support from 1G to 400G to help to efficiently meet both user and network traffic demands.
- Value: Customers can experience greater value with:
- Investment protection
- MPA backward compatibility
- Next-generation SC compatibility
- Optimized CapEx spending with right-sized platform to meet specific scale, space, power, and redundancy requirements
- Optimized OpEx spending with field-upgradeable and reusable components (similar to distributed systems) combined with using automated operations
- Sustainability that can help customers toward meeting their sustainability goals using a simplified centralized architecture.
Figure 6. Enabling customer outcomes
Meet evolving network priorities
Cisco is empowering customers with a hybrid architecture to meet their ever-changing network demands. Cisco 8600 Series Routers are a culmination of innovations in silicon, software, and hardware—all coming together to deliver a new breed of simple, reliable, flexible routers that give customers more choices and help maximize value.
Source: cisco.com