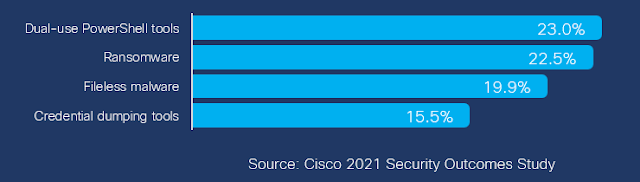
| Challenge: Expertise | Challenge: Time | Challenge: Evidence |
| “My team can’t be experts on every new threat, or all be experts in threat hunting.” | “I don’t have enough time to go after every new threat, alert, patch and compromised device.” | “We can’t always identify which threats to prioritize or get to the root cause of every attack.” |
Tuesday, 28 February 2023
An Easier Way to Secure Your Endpoints
Saturday, 25 February 2023
The Rise and Rise of DevOps Adoption
Demystifying DevOps
Statistics on DevOps adoption
 |
| Figure 2. Impact of DevOps on organizations. (Source: Atlassian) |
Recent surveys and studies complement the steady increase in the adoption of DevOps in organizations. In a Global Market Insights study, the DevOps market size exceeded US$7 billion in 2021 and is expected to grow at a CAGR of over 20% from 2022 to 2028 to a value of over US$30 billion.*
 |
| Figure 3. (Source: Atlassian) |
Outlook for DevOps in the Future
Thursday, 23 February 2023
Getting to the Core of the Digital Divide with 5G Fixed Wireless Access
Why Fixed Wireless Access?
Growing Fixed Wireless Access from 4G to 5G
Wednesday, 22 February 2023
Boost Your Cisco 200-301 Exam Score with CCNA Practice Test
To earn the Cisco Certified Network Associate (CCNA) certification, you must pass the Cisco 200-301 exam. This exam tests your knowledge and skills in networking fundamentals, network access, IP connectivity, IP services, security fundamentals, automation, and programmability. To prepare for the exam, you need to have a solid understanding of CCNA syllabus, and the best way to do so is by taking CCNA practice test.
This article will discuss different study resources, why CCNA practice tests are essential, and how they can help you ace the Cisco 200-301 exam.
Helpful Study Resources to Ace Cisco 200-301 Exam
Preparing for the Cisco 200-301 exam can be daunting, but with the right study resources, you can ace the exam and take your networking career to the next level. This article will explore the best study resources for the Cisco 200-301 exam that will help you prepare for the test and achieve your certification.
Cisco Learning Network
The Cisco Learning Network is a comprehensive resource for anyone studying for a Cisco certification. This platform offers a variety of resources, including self-paced e-learning courses, study groups, and practice exams. The Cisco Learning Network also has a community of experts available to answer your questions and provide guidance throughout your studying process.
Official Cert Guide
The Official Cert Guide is a comprehensive study resource written by Cisco experts. This guide provides in-depth coverage of all exam objectives, with detailed explanations of concepts and practice questions to help you gauge your understanding. The guide also comes with access to an online practice test engine, which provides you with practice questions and simulates the exam environment.
Cisco Press Books
Cisco Press is the official publisher of Cisco certification and technology books. Their books cover a wide range of topics related to networking and provide detailed explanations of concepts and technologies. For the Cisco 200-301 exam, Cisco Press offers a variety of books, including the Official Cert Guide, Exam Cram, and study guides.
CCNA Practice Test
Evaluating your preparedness for an exam by taking a CCNA practice test is advisable, as it can give you an idea of your readiness for the actual exam. Once you have taken the exam, you can examine your performance and make improvements in areas where you need to. It is also recommended that you take a complete practice test, as this can help you tackle the daunting task of taking the actual exam and the anxiety that comes with it.
Why Are CCNA Practice Tests Important?
CCNA practice tests are a great way to prepare for the Cisco 200-301 exam. These tests mimic the exam and allow you to practice and assess your knowledge and skills in a simulated environment. By taking practice tests, you can identify your strengths and weaknesses and focus on areas that need improvement.
Practice tests also help you familiarize yourself with the exam format, types of questions, and time constraints. This familiarity will help you feel more confident and less anxious when taking the exam.
How CCNA Practice Tests Can Help You Ace the Cisco 200-301 Exam
Identify Knowledge Gaps: CCNA practice tests can help you identify knowledge gaps in each exam topic. By doing so, you can focus on areas that need improvement and reduce the chances of missing questions during the exam.
How to Find CCNA Practice Tests
There are many resources available online that provide CCNA practice tests. You can find free and paid options, and choosing a resource that meets your needs and budget is essential.
Some popular resources for CCNA practice tests include Cisco's Official Practice Test and the nwexam website. Both platforms offer a comprehensive official practice test that explains each question.
Conclusion
Taking CCNA practice tests is essential to preparing for the Cisco 200-301 exam. These practice tests can help you identify areas where you need improvement, build your confidence, reduce your anxiety, get used to the exam format, and experience different types of questions. By taking advantage of CCNA practice tests, you can increase your chances of success and become a certified Cisco network associate.
Tuesday, 21 February 2023
Cisco Introduces 100G Service Edge To The Catalyst 8500 Family
Deploy WAN Innovations At Scale
What Makes C8500-20X6C An Industry-Leading Services Edge Platform?
Add Muscle To Your Network With C8500-20X6C
Thursday, 16 February 2023
Evolution towards Full-Stack Observability
Modern Applications are complex
Monitoring to Visibility to Full-Stack Observability
Saturday, 11 February 2023
Boost your 80km links to 100G with QSFP-100G-ZR4-S optical modules
Introduction
 |
| Cisco’s QSFP-100G-ZR4-S pluggable module |