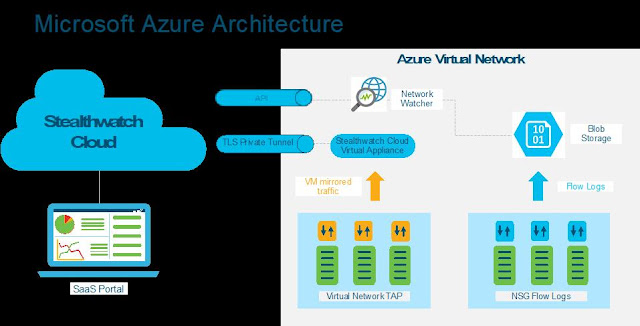
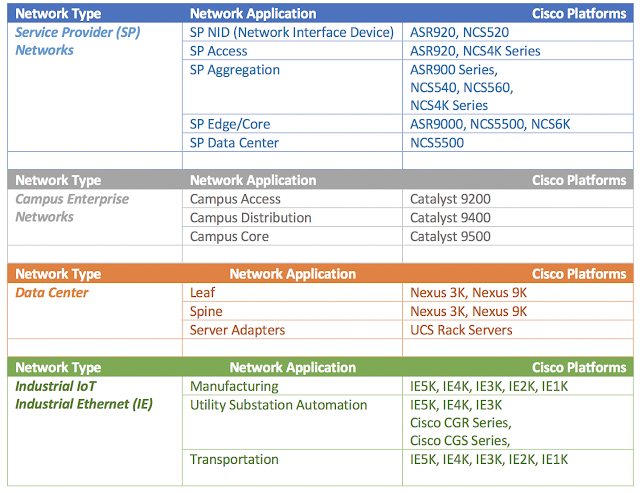
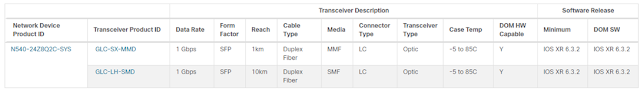
Like the engine is to a race car, IT is at the heart of your business—to keep it running around the clock, deliver new products and services, drive transformation, and extend to new markets globally. So, it’s no surprise two of the top three operational priorities for CIOs include delivering a stable IT and increasing operational efficiencies.
Keeping your IT engine secure and running at optimal performance, while meeting the needs of your business can be a lot to juggle. With limited time and resources, we know your time is best spent on what matters most for your business. In fact, forty-six percent of IT use outsourcing to access skills and thirty-two percent plan to increase their outsourcing spend.
Having the right IT services pit crew in place who not only has the expertise to keep your network up and running but delivers business value is critical. And if something goes wrong, they can resolve it quickly, so you can focus on more important matters.
Keeping your IT engine secure and running at optimal performance, while meeting the needs of your business can be a lot to juggle. With limited time and resources, we know your time is best spent on what matters most for your business. In fact, forty-six percent of IT use outsourcing to access skills and thirty-two percent plan to increase their outsourcing spend.
Having the right IT services pit crew in place who not only has the expertise to keep your network up and running but delivers business value is critical. And if something goes wrong, they can resolve it quickly, so you can focus on more important matters.
Here are three things to consider that will enhance efficiency, uptime, and resolve problems quickly to help maintain a stable IT.
1. Have better visibility to operate more efficiently
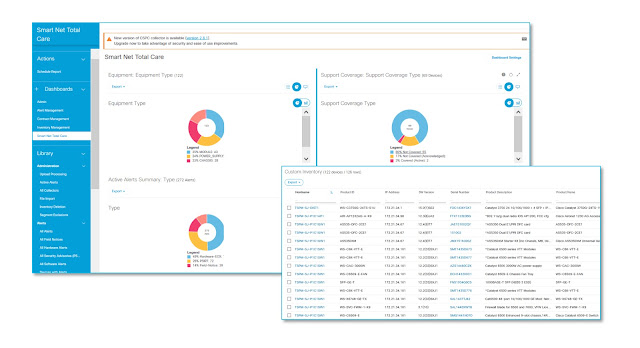
A key part of keeping everything running smoothly and error-free is knowing exactly what is installed in your network. To do this you have a couple of different options, each with their own considerations. To see what you have running on your network, you have to go through the process of accessing each device manually or running different manual scripts to collect parts of the information needed to create an inventory view. Depending on how many devices you need to manage, the first option is very labor intensive, while the latter can be error prone. If you happen to miss a device, you won’t be able to see that piece of hardware, leaving it open to potential vulnerabilities – and adding more manual efforts to your plate.
Cisco Smart Net Total Care makes having insights in your installed base effortless and automated with its integrated smart capabilities through the Smart Net Total Care portal and collector software which automatically collects device information on Cisco products. Once the collector is installed and configured, it can run automated network discoveries, automated network inventories, and automated inventory uploads back to Cisco. With the click of a mouse you can view your installed base data, helping you manage your Cisco devices easier and operate more efficiently. “The automation on the Smart Net Total Care backend makes a small team’s performance large in executionand impossible to do otherwise,” John Baldwin, IT Manager for Infrastructure Projects and Architectures, Pella.
2. Ensure devices are up-to-date and secure to maximize uptime
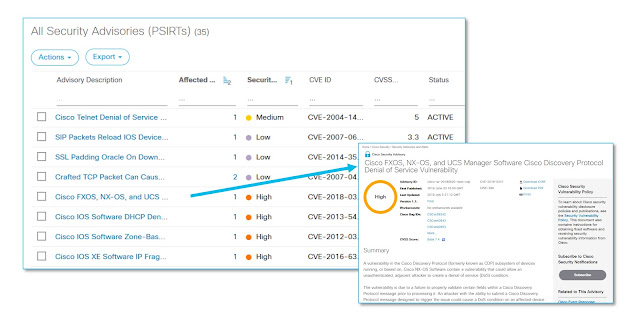
Keeping all of the devices in your network secure and up-to-date is critical. Part of preventing any potential vulnerabilities is making sure that your devices are running code that isn’t impacted by known critical bugs or PSIRTs, and is aligned with compliance rules. However, when a problem does arise, you have to access that device, obtain the software version and type, and manually search cisco.com to find any issue associated with that specific product type and software version. When you need to get information on your device’s lifecycle you need to manually look for all of that data using End-of-Life and End-of-Sales product bulletins for each device. If you have thousands of devices you’re tasked with tracking and keeping secure, that is a daunting task.
The Smart Net Total Care portal gives you visibility into your devices, including what IOS you’re running to help ensure you’re using the appropriate code versions across your devices, eliminating the potential for more vulnerabilities. In addition, PSIRT, BUG and automatic lifecycle data correlation and custom reports help you manage your device security more efficiently. “We can see which device are covered and at what service level, so we can appropriately cover devices to minimize risk within our environment,” Operations Manager, Service Provider.
3. Get an accurate view of your devices to resolve issues quickly
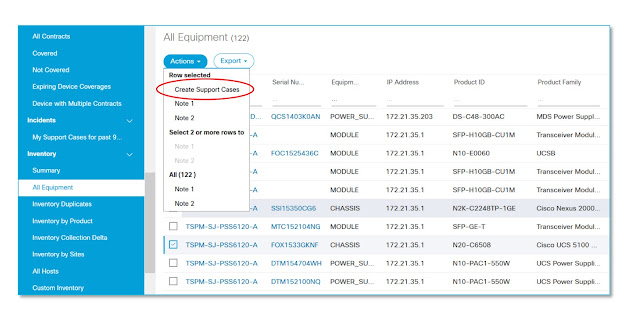
When you face a network downtime or device issue, time is always of the essence, especially if you have thousands of devices to maintain. And that’s not just the time spent in finding the number to call support. It starts with having to gather all of the device-level information you need just to open a case to get the problem resolved. That includes the device serial number, product ID, and contract number related to that device. Depending on the kind of inventory view you have (and how comprehensive it is), all of this data could take you a long time to gather. This does nothing but delay your time to issue resolution and take up even more of your limited time.
Smart Net Total Care can help you reduce your time spent in resolving issues drastically by giving you a clear and accurate view of your device information. The portal software does all of the correlation of your collected device serial numbers, product IDs, and contract numbers automatically, which means you don’t have to spend time looking for information. You can also initiate a Technical Assistance Center (TAC) case directly and instantly within the portal if you experience an issue, shortening your time to resolution even more. “Greater visibility across the network allows us tobetter prioritize and plan ahead for updates and replacement of equipment, assuringthe continuous operation of the company.”.
Whether you’re a large or small enterprise, Cisco’s Smart Net Total Care delivers world-class technical support that keeps your organization running smoothly, while driving business value.