At Cisco, we have asked thousands of our employees around the world to work from home. Most of them came to the office every day. Other companies have also taken this step, and many more will do so soon. We are all motivated by the same things: care for the people we work with, a desire for everyone to stay healthy, and the hope that by preventing community transmission we can shorten this period of disruption.
While our teams are at home, we want to support them in every way we can, which includes helping them be productive in their jobs so they can continue to drive towards their goals. Although we have a strong culture that supports remote work when it makes sense, and amazing technology to enable it, this shift can still be daunting. At Cisco, we’ve always had business continuity planning and even though the plan exists for shutting down corporate headquarters, it’s never too late to take one more look before everyone leaves the building. Here are the questions we’ve been asking. Maybe some of them may help you, too.
Thanks so much, stay healthy, and please let us know how we can help.
Some employees new to working from home will need help. In addition, regardless of planning, systems may glitch when exposed to multiples of their regular loads. We have to be ready for a spike in IT cases.
There is no easy way to dramatically staff up IT to the extent that might be called for, at least not quickly. Proactive advice to employees is critical. Send notes on how your remote work tools function, and how to set them up. If possible, encourage people to test work-from-home tools, like their VPN software, while they are still in the office.
And remember that people will pull together in a crisis. Your community is a powerful resource. Setting up employees to support each other, via online chat tools, wikis, forums, and email lists can reduce the load on IT.
If your business has resources behind a corporate firewall, it’s likely that your users will connect to them using a virtual private network (VPN). The VPN concentrator that connects these users to your corporate network may not be configured for the new load of remote users.
It might be time to do a few things to increase your capability to handle an increased load. Obviously, you can acquire more VPN concentrators and get them installed
Check your IP pool. The new load of remote workers could outnumber the IP addresses in the pool reserved for external access. The pool can be increased by your staff.
Employees can be asked to not use their VPN-connected work computers for non-work tasks. During this crisis, it is fair to ask employees to be disciplined in their use of company resources. You might be shocked at the amount of cat videos streamed through your corporate VPN. Blocking entertainment sites like Netflix and Hulu could also be a part of this strategy, but honestly, for most of us, asking employees would probably be just as effective and with less conflict.
Companies whose VPNs are configured to handle all traffic from workers’ devices might want to look at enabling split tunneling, where traffic destined for work resources goes over the VPN link, while internet bound traffic does not. AnyConnect can even selectively split tunnel by whitelisting only IP ranges of trusted sites. Just a few ranges can have a dramatic effect. Of course, this would have security ramifications and it’s up to your security team to weigh the risks here.
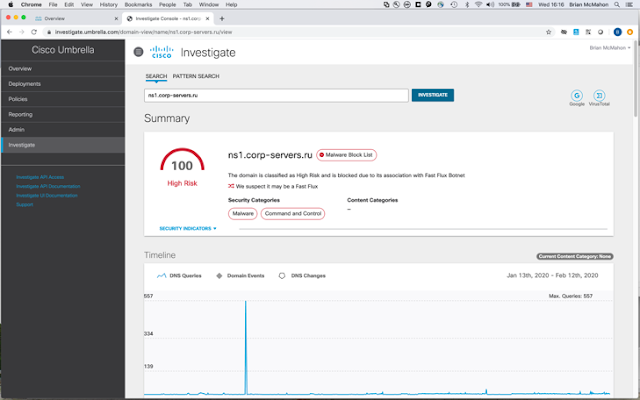
You can also leverage Cisco’s Umbrella infrastructure to secure your Internet bound traffic instead of pushing more traffic through your VPN and security stack. It’s remarkably easy to setup and can be done remotely.
While many workers get productive by just connecting the laptops to the home ISP and your company VPN, that may not be true for call center employees or anyone with direct communication needs. There are teleworker gateways (including our own products) that will let these workers put their dedicated communications devices online from their homes.
Under the work-from-home scenario, network loads shift. Now is a good time to make sure your business’ network links are configured for more traffic. Depending on the types of links you have, it may be a simple and straightforward call to upgrade your committed information rate (CIR). If not, using the tips above to reduce network load might be even more relevant.
At your employees’ homes, ISP capacity may come in to play as well. Many ISPs today are configured to support massive loads to handle video streaming traffic. ISP execs say this traffic peaks at about 8pm every day, so during the lighter workday, there should be ample capacity to handle business networking needs, even video calling. Also, several ISPs are working to eliminate data caps and bandwidth throttling.
It is still possible that the work-from-home transition will tax consumer networks. As one of our IT practitioners says, “As you get further out from the company’s network, things are outside your control.”
Should performance for remote workers suffer, employees should know how to take measures to improve their online experience, especially in collaboration tools like video conferencing. Employees can turn off video during a call (if the software doesn’t adapt automatically to network issues), or even route audio to their phone.
Have you trained your employees in best practices for working remotely?
The nature of work changes when your teams are no longer sitting together. Some employees may be able to get more done, while others will find working from home isolating. More critically, the role of managing changes. Everyone, including people not working from home, will have to allot extra time and energy to staying in touch with the co-workers.
We have a number of remote working tips, including regular community time for all teams as well as a block every day where there’s a video bridge everyone on the team connects to, and people can call in to talk as available, get small things resolved and just catch up. It can be a comfort and social leveling function for everyone in a time of flux.
Depending on your industry, up to 100% of your teams may soon be working from home, and due to the exponential nature of viral spreads, the situation is likely to outpace traditional planning methodologies. If you do not have a business continuity plan that encompasses this type of crisis, we recommend you quickly address your workers’ technology needs, your internal network, and management policies. Open communication with all constituencies is vital.
And whether it’s as-needed all-hands meetings with the CEO and medical experts, or ramped-up management one-on-ones, it’s important everyone feels cared for during this time. We hosted our first company-wide Q&A session with corporate medical doctors on Covid-19 with just two hours notice and nearly 20,000 attendees. It was an indication of everyone’s hunger for information and connection.
When so much is uncertain and worrisome, I think it’s that much more important to make it possible for people to continue working with their teammates, and still find wins together. With the right management and technology behind them, at least this part of life can remain familiar and comfortable.
Thanks so much, stay healthy, and please let us know how we can help.
Is IT ready to handle a spike in support calls and tickets?
Some employees new to working from home will need help. In addition, regardless of planning, systems may glitch when exposed to multiples of their regular loads. We have to be ready for a spike in IT cases.
There is no easy way to dramatically staff up IT to the extent that might be called for, at least not quickly. Proactive advice to employees is critical. Send notes on how your remote work tools function, and how to set them up. If possible, encourage people to test work-from-home tools, like their VPN software, while they are still in the office.
And remember that people will pull together in a crisis. Your community is a powerful resource. Setting up employees to support each other, via online chat tools, wikis, forums, and email lists can reduce the load on IT.
Is your VPN ready for the load?
If your business has resources behind a corporate firewall, it’s likely that your users will connect to them using a virtual private network (VPN). The VPN concentrator that connects these users to your corporate network may not be configured for the new load of remote users.
It might be time to do a few things to increase your capability to handle an increased load. Obviously, you can acquire more VPN concentrators and get them installed
Check your IP pool. The new load of remote workers could outnumber the IP addresses in the pool reserved for external access. The pool can be increased by your staff.
Employees can be asked to not use their VPN-connected work computers for non-work tasks. During this crisis, it is fair to ask employees to be disciplined in their use of company resources. You might be shocked at the amount of cat videos streamed through your corporate VPN. Blocking entertainment sites like Netflix and Hulu could also be a part of this strategy, but honestly, for most of us, asking employees would probably be just as effective and with less conflict.
Companies whose VPNs are configured to handle all traffic from workers’ devices might want to look at enabling split tunneling, where traffic destined for work resources goes over the VPN link, while internet bound traffic does not. AnyConnect can even selectively split tunnel by whitelisting only IP ranges of trusted sites. Just a few ranges can have a dramatic effect. Of course, this would have security ramifications and it’s up to your security team to weigh the risks here.
You can also leverage Cisco’s Umbrella infrastructure to secure your Internet bound traffic instead of pushing more traffic through your VPN and security stack. It’s remarkably easy to setup and can be done remotely.
Do Call Center Employees have the Teleworker equipment they need?
While many workers get productive by just connecting the laptops to the home ISP and your company VPN, that may not be true for call center employees or anyone with direct communication needs. There are teleworker gateways (including our own products) that will let these workers put their dedicated communications devices online from their homes.
Do you have enough raw network capacity? Do your employees?
Under the work-from-home scenario, network loads shift. Now is a good time to make sure your business’ network links are configured for more traffic. Depending on the types of links you have, it may be a simple and straightforward call to upgrade your committed information rate (CIR). If not, using the tips above to reduce network load might be even more relevant.
At your employees’ homes, ISP capacity may come in to play as well. Many ISPs today are configured to support massive loads to handle video streaming traffic. ISP execs say this traffic peaks at about 8pm every day, so during the lighter workday, there should be ample capacity to handle business networking needs, even video calling. Also, several ISPs are working to eliminate data caps and bandwidth throttling.
It is still possible that the work-from-home transition will tax consumer networks. As one of our IT practitioners says, “As you get further out from the company’s network, things are outside your control.”
Should performance for remote workers suffer, employees should know how to take measures to improve their online experience, especially in collaboration tools like video conferencing. Employees can turn off video during a call (if the software doesn’t adapt automatically to network issues), or even route audio to their phone.
Have you trained your employees in best practices for working remotely?
The nature of work changes when your teams are no longer sitting together. Some employees may be able to get more done, while others will find working from home isolating. More critically, the role of managing changes. Everyone, including people not working from home, will have to allot extra time and energy to staying in touch with the co-workers.
We have a number of remote working tips, including regular community time for all teams as well as a block every day where there’s a video bridge everyone on the team connects to, and people can call in to talk as available, get small things resolved and just catch up. It can be a comfort and social leveling function for everyone in a time of flux.
How can we make sure our teams feel cared for?
Depending on your industry, up to 100% of your teams may soon be working from home, and due to the exponential nature of viral spreads, the situation is likely to outpace traditional planning methodologies. If you do not have a business continuity plan that encompasses this type of crisis, we recommend you quickly address your workers’ technology needs, your internal network, and management policies. Open communication with all constituencies is vital.
And whether it’s as-needed all-hands meetings with the CEO and medical experts, or ramped-up management one-on-ones, it’s important everyone feels cared for during this time. We hosted our first company-wide Q&A session with corporate medical doctors on Covid-19 with just two hours notice and nearly 20,000 attendees. It was an indication of everyone’s hunger for information and connection.
When so much is uncertain and worrisome, I think it’s that much more important to make it possible for people to continue working with their teammates, and still find wins together. With the right management and technology behind them, at least this part of life can remain familiar and comfortable.