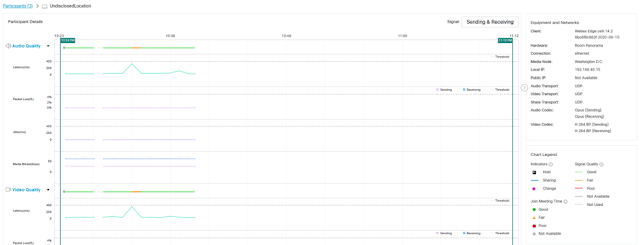
Some of the most common questions emanating from customers in this situation include the following:
◉ “I want to see how my business is impacted by COVID-19. How can I ensure my campus is safe to re-open?”
◉ “How can I provide personalized customer experiences while ensuring social distancing?”
◉ “How can I ensure the number of employees attending work is within the safe threshold?”
◉ “How can I track and alert employees if the number of people within the campus at a given time poses a threat to the safety and health security of all in attendance?”
Get Help Safely Returning to Your Campus with the Cisco CX offer for Cisco DNA Spaces
Cisco offers a location-based analytics solution—Cisco® DNA Spaces—which digitizes physical spaces to provide you with insight about people throughout your workspaces, including how, where, and when they move through your location. It collects data from your existing Cisco Wi-Fi access points to provide information about people, including employees, customers, patrons and visitors, as well as things, such as assets and sensors, within your properties. Built with a variety of applications (apps), Cisco DNA Spaces sets up workplace density thresholds to monitor the number of employees in buildings across campus, provides notifications when thresholds are reached, shares safety information, and enables rapid response to incidents via proximity reporting.
In line with this, Cisco Customer Experience (CX) has introduced a new Service offer that helps you deploy and address your use cases with Cisco DNA Spaces. The Cisco CX offer for Cisco DNA Spaces delivers our new Advise and Implementation Service that helps with design, configuration, deployment and post-implementation support of Cisco DNA Spaces, which empowers businesses to analyze data from their workspaces and define actionable insights to accelerate office re-openings.
Our CX experts analyze your current environment and requirements, advise you on the best solution design and configuration for agreed upon use case(s), and tests and validates the desired functionality prior to production use. You’ll get expert help with right-fit use-case implementation, including a knowledge transfer session and post-implementation support to enable ongoing use of the solution and help you maintain essential business operations. We’ll make sure you can take full advantage of these location-based services to leverage critical visibility throughout your physical workspace locations, which plays a crucial role in managing the safe return of people to your workspaces.
Two levels of Advise and Implementation packages are available for Cisco DNA Spaces—small and large packages—based on the size of your organization. You’ll have the option to get support for up to five buildings (or 30 floors or shops) to cover your physical workspaces, smart captive portals for enhanced customer experience, CX post-deployment use assistance, and more.
How Cisco CX Simplifies and Accelerates Your Safe Workspaces
Next-generation sensing capabilities are already built into your Cisco Wi-Fi access points—such as Cisco Catalyst®, Aironet®, and Meraki®. However, they need to be turned on and aligned, and Cisco CX will do that for you. If you don’t already have them, Cisco CX can quickly deploy new Cisco Wi-Fi access points for you. We’ll take care of complete connectivity between your Cisco Wi-Fi access points, Cisco network, and the cloud-based Cisco DNA Spaces solution. Furthermore, the granular data collected by your Cisco Wi-Fi access points feeds the Cisco DNA Spaces apps. From this app data, you can then leverage advanced analytics to achieve powerful insights into end-user behavior—how people use, move, and occupy spaces. The following apps are seamlessly bundled in our Cisco DNA Spaces solution:
◉ Right Now App: Sets workplace density thresholds to monitor the number of employees in Wi-Fi enabled zones across campus.
◉ Notification Trigger: Uses a rule engine to power an API, which triggers notifications when thresholds set by the Right Now App are crossed. Keep your teams updated at all times with automated notifications via Webex Teams™, SMS, or email.
◉ Impact Analysis App: Helps you determine whether your operations need to be adjusted for the improved safety of your people by measuring the effectiveness of your back-to-safe-workspaces policies, including whether it’s safe to introduce more people into your physical workspaces.
◉ Proximity Reporting App: Delivers historical analytics, allowing you to trace the steps of your Wi-Fi connected people. This app reports the presence and path down to individual users, while also reporting who else was present, allowing you to investigate incident impact across employees and zones by tracing proximity.
◉ Engagements App: Shares contextually triggered safety information with employees based on where
they are in any of your buildings. The rule engine drives dynamic engagements based on each building classification as well as individual employee personas for more relevant information.
With the data stream created by Cisco Wi-Fi access points and fed to the bundled Cisco DNA Spaces apps, you can gauge the effectiveness of your back-to-work policies, and determine when it’s safe to allow more people back into your office. This includes the ability to determine if there is an area in any of your workspace zones where people are clustering and breaking your distancing guidelines. The real-time analytics offered by Cisco DNA Spaces make it easy to monitor the number of people across campus, including the effectiveness of your distancing policies with workspace density thresholds throughout all your monitored zones and across points of ingress and egress. Notification triggers generated by policy breaks and proximity reporting help you take action to keep your people safe. Your employees can also receive safety information triggered contextually based on their presence in any of your monitored physical zones. All this can be managed through a single, cloud-based pane of glass to simplify how you consume and leverage location services to keep your people safe.
Safety Can’t Wait—Start Your Location-Based Analytics Today
If you plan to re-open your campus gradually, we’ll work at your pace, easing into a broader rollout and expanding to deploy more specific use cases when you’re ready. Regardless of your rollout scheme, you’ll enjoy easy procurement and fast deployment. Leverage the right expertise to get up and running quickly with Cisco DNA Spaces in days, versus weeks, all while prioritizing the safety of your people.