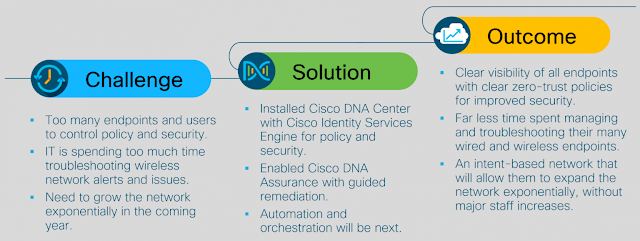
Industrial NetDevOps solves real-world problems
◉ Breaking down the barriers and building a closer alignment between the IT and OT departments ◉ Increase network change management, incident management and security
◉ Lower OT expenses and downtime while increasing your network effectiveness and agility
These crucial and well-desired subjects are exactly what Industrial NetDevOps is trying to solve. And DevNet has the tools and learning resources to help you start with that journey right away:
◉ Free Webinar, July 14th — Register Now
◉ New Learning Labs
◉ New Scripts on Code Exchange
What is Industrial NetDevOps?
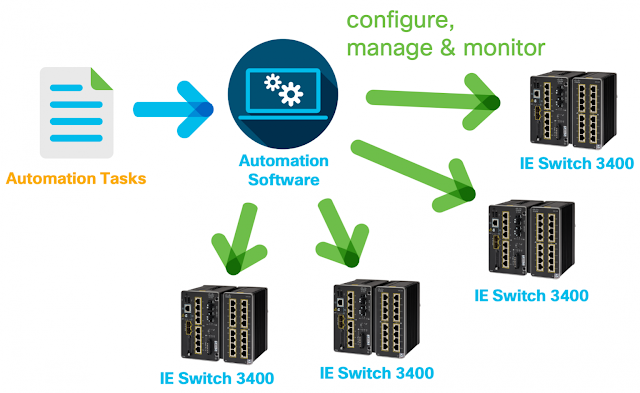
Industrial NetDevOps brings the culture, tools, technical methods and best practices from DevOps to Industrial Networks.
Instead of using SNMP and CLI, you configure, manage and monitor industrial network devices via standardized network device APIs and software automation tools. Industrial NetDevOps workflows use Open Source, standards and Python scripts alongside commercial devices and tools to deliver fast-responsive and secure industrial networks.
DevOps is a set of practices that combines software development (Dev) and IT operations (Ops). Similar to DevOps, in the industrial space are industrial operations professionals who understand and control the equipment (OT/Dev), but need support from their IT colleagues to make OT-data meaningful, OT-devices accessible and better aligned with other business systems (IT/Ops).
The vision of Industrial NetDevOps is taking the full advantage of both teams by working together: Creating a single source of truth for network configurations (e.g. with Git), making small but well tested changes to the network, deploy configuration changes though APIs, use automation to save time and costs, enable automated IT network services for operations professionals, get real-time health data of your network and OT devices and many more.
What has changed? Why move now?
Operations leaders recognize that operational data they use to support real-time decision making could create additional value for the company. The vision of a fully connected factory is real, the transformation is happening right now. Therefore, the industrial network needs to be as responsive, agile and secure as it has ever been.
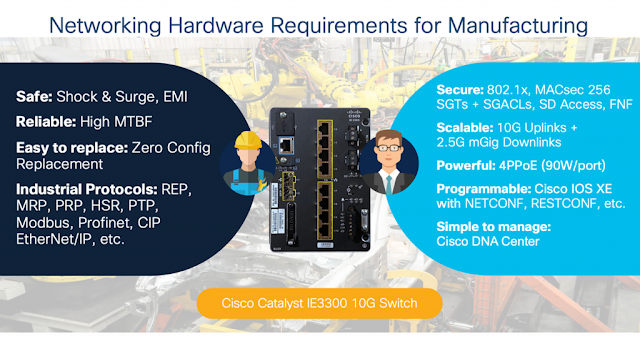
Cisco realized this movement and is leading it: The industrial switch series IE3x00, the embedded switch ESS3300 and the industrial router IR1101 are running IOS XE (same as on the Catalyst 9000 Series) which enables model-driven programmability with open APIs and data models such as NETCONF/RESTCONF & YANG. Also, the Cisco Catalyst 9800 Series Wireless Controller supports model-driven programmability along with traditional APIs.
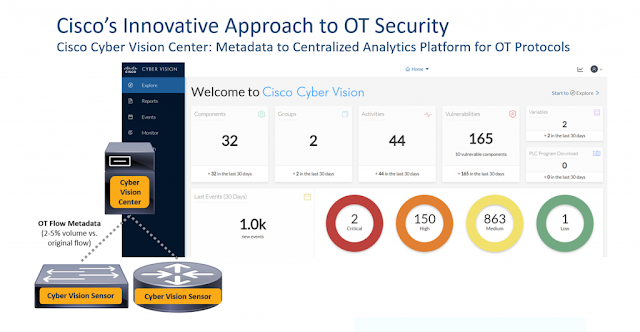
Furthermore, the network controller and orchestration software Cisco DNA Center supports an extensive REST-API as well as the industrial security software Cisco Cyber Vision. As you can see, Cisco’s industrial software and hardware is ready for the transformation!
What are the Use-Cases which you can start right now?
To give you a better understand of how powerful Industrial NetDevOps can be with our Cisco industrial solutions, here are some use-cases which will get you started. However, there are many more!
◉ Enable or disable remote access with just one REST-API Call: By simply defying a service as a python script which will execute pre-defined NETCONF commands to create, enable and disable ACLs on specific industrial hardware, for example the IE3400.
◉ Deploy your desired IOS configuration for hundreds or thousands Cisco IE switches automated with the software automation tool Ansible and just one command. For example, configure the IND bootstrap-, specific ISE-, PROFINET-, CIP-, PTP-configuration and so on with one centralized tool or even application of yours.
◉ Get fully automated and tailored reports about the health of your network and IT/OT devices via the REST APIs of Cisco Cyber Vision and Cisco Industrial Network Director. In the same process-chain, analyze the report with other Cisco tools: Check each DNS query what has been made in your industrial network with the Cisco Umbrella Investigate API to see if some requests were malicious and highlight the originators.
◉ Enable ChatOps in your Industrial Environment: Operations professionals can easily change the network configuration and many other application settings via simple text messages on Cisco Webex Teams (see the example below with the IR1101). What changes the OT worker is allowed to make will be pre-defined by the IT team.
How does the Toolset of Industrial NetDevOps look like?
It depends on your use-cases and requirements what skills are important – you do not need to know them all! Here is breakdown of which technologies and tools will help you further to enable Industrial NetDevOps:
◉ Programmability Basics: Understanding REST-APIs and Python (or any other programming language) are the basics for programmability which will help you automating your tasks and can solve specific IT/OT challenges.
◉ Device Level: In order to leverage the APIs directly on your industrial device (e.g. IE3400) for a single configuration change or getting device operational data, get started with NETCONF/RESTCONF and YANG.
◉ Controller & Orchestrator Level: If you manage your industrial hardware with Cisco DNA Center, Industrial Network Director, Kinetic GMM or vManage, you can simply do that with the REST-APIs and automate your tasks with Python for example.
◉ Configuration Management: If you want to change the IOS configuration on hundreds or thousands of devices, get started with the software automation tools Ansible, Puppet, Chef or others.
◉ Network Verification: If you want to know if your IOS configuration on which of your IE3400s has changed in the last weeks or months or want to test your IOS configuration, definitely get started with the Cisco framework pyATS.
◉ Security: Especially in an industrial environment network security is highly important. Together with the industrial security software Cisco Cyber Vision (REST-API capable), Cisco Firepower & FirePower Threat Defense (REST-API capable), the ruggedized Cisco Industrial Security Appliance ISA3000, Cisco Stealthwatch (REST-API capable) and Cisco Identity Services Engine (pxGrid API) enable your network to talk to these security tools and the other way round.
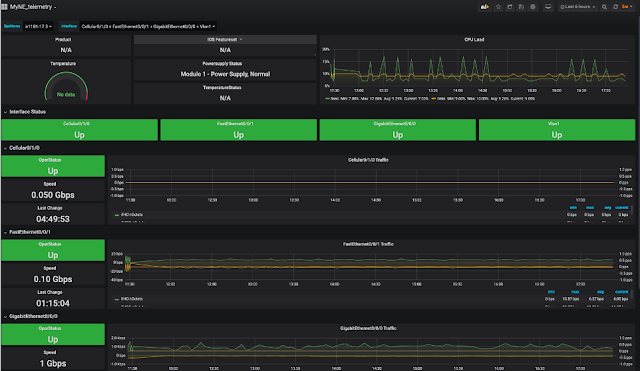
◉ Telemetry and Monitoring: To visualize your collected data from your industrial device (e.g. IR1101 in the image below), get started with streaming telemetry and the TIG-stack (Telegraf, InfluxDB and Grafana), ELK-stack (Elasticsearch, Logstash and Kibana) or any other preferred databases and dashboards.
Where should I deploy the Industrial NetDevOps tools?
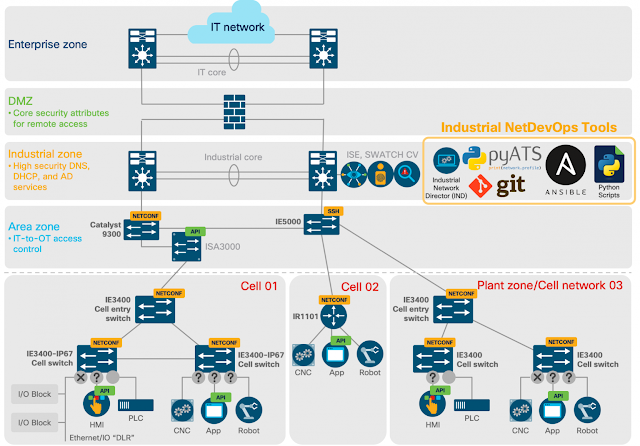
As usual, this depends on your architecture, devices, and industry. However, if we look at the Converged Plantwide Ethernet (CPwE) Architecture, it makes sense to include these tools in the Industrial Zone as seen in the image below.
Source: cisco.com