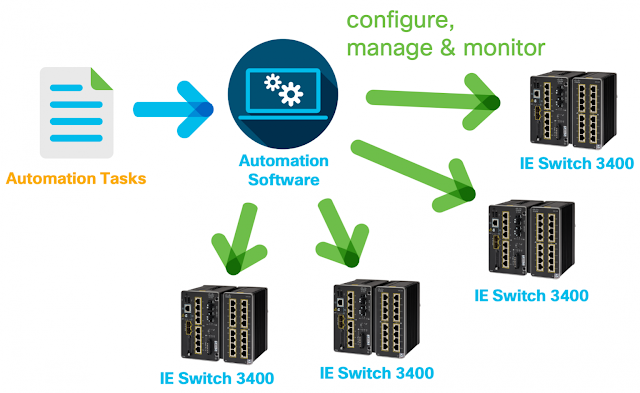
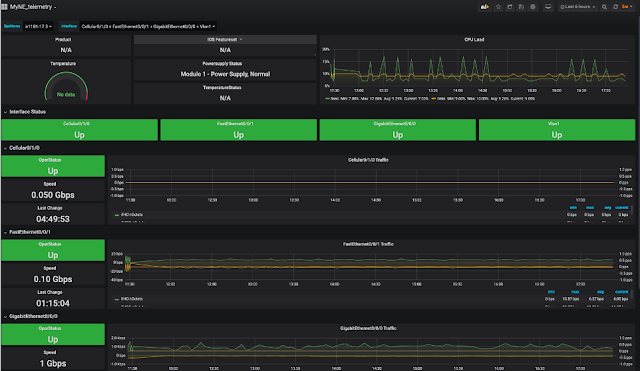
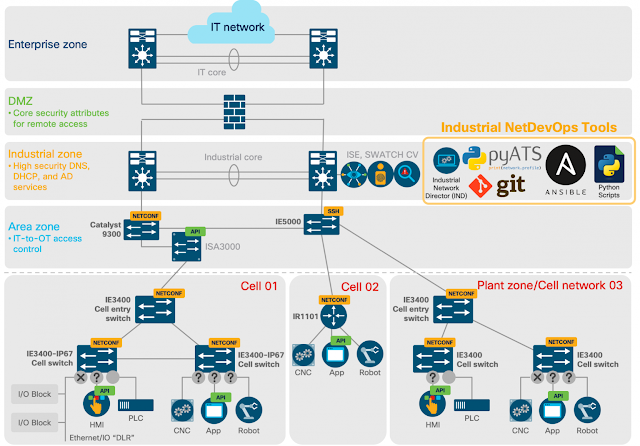
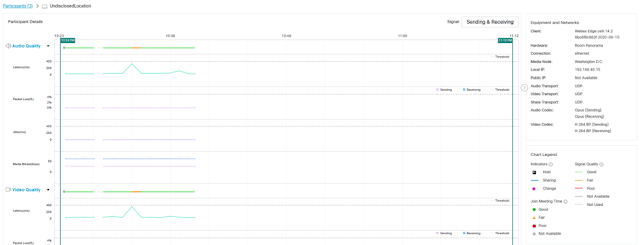
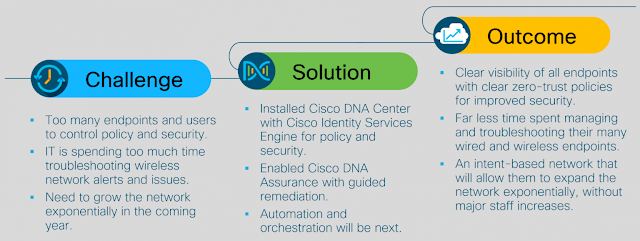
Cisco DNA Assurance and Cisco SD-Access are two major components of Cisco’s Digital Network Architecture, and are implemented using the Cisco DNA Center management platform. Together, these enable organizations to apply business intent to the network, creating unprecedented levels of visibility and control across the entire enterprise network.
Real customers sharing real experiences
For anyone who has been skeptical about our claims about the benefits of Assurance and SD-Access, this report should help sway your opinion. There are many firsthand accounts from customers who are using these solutions in their networks, not just as demos or proof of concepts, but to actually run their IT operations. Participants in the study represented a range of business sizes and industry verticals, making it even more impressive that the results were so positive across the board.
Cisco DNA provides real benefits
According to the IDC authors, customers initially turned to SD-Access and Assurance to make managing complex operations easier, prepare for anticipated growth, and become more proactive in their approach to network management. What they discovered was that as network management becomes easier and performance improves, staff productivity increases and greater innovation company-wide becomes possible.
Some highlights of the results
◉ Average annual benefits of $3.18 million on a per organization basis
◉ 462% five-year ROI
◉ 9-month payback period
◉ 49% more efficient network management staff
◉ 35% more efficient network security teams
◉ 86% reduction in unplanned downtime
A key reason that the measured ROI was so high is that the time savings is compounded across all areas of network management and extends to non-IT personnel as well. Customers reported a wide range of positive benefits. With Cisco SD-Access, security is both more effective and easier to deploy and maintain. With Cisco Assurance, service issues are easier to track down and are detected earlier. These improvements lead to reduced downtime and improved application performance.
Source: IDC 2020
Cisco DNA solves real problems
Legacy network processes are inefficient and do not scale to the number of clients and devices now in use today. As the scale of the network increases, the friction inherent in manual processes for onboarding and managing connectivity cause a cascade of difficulties such as:
◉ Less than optimum experience for network users.
◉ Policy enforcement becomes more and more complex and inefficient.
◉ Holes open up in security policies.
◉ Network operators do not have visibility into what is happening in the network at any given moment.
◉ Problems take time to identify and solve, making users frustrated and slowing productivity across the company.
We believe this report helps prove that SD-Access and Assurance aren’t just shiny new toys. These solve real problems experienced by most network operators. With these solutions, you can proactively solve problems. You can match policy to the user, not the machine. You can automate routine tasks and roll out changes more quickly, making your network and your business more agile and able to respond to changing conditions.
Here is a concrete example that one of the customers in the study shared about their experience with SD-Access that illustrates this point about time savings:
A big thing for us is the rapid deployment or moving of different segmented networking groups. For example, right in the middle of one of our projects we had one of the labs moved. But it took 4 hours instead of what would have been about a month prior to SD-Access.