The COVID-19 pandemic has thrust the world into an era of massive digital business transformation across industries like manufacturing, utilities, smart cities, oil and gas, and transportation. To meet these new challenges and keep business operations running smoothly, we need cost-effective solutions. Traditionally, IoT solutions were typically used to reduce operational expenses and increase operational equipment efficiency (OEE). With the onset of the pandemic however, the need for managing business operations remotely across these IoT verticals has increased rapidly. This has led to a sudden, unprecedented shift towards an increased adoption of cloud native IoT management applications hosted by public cloud providers in partnership with IoT SaaS vendors. An example for such a use case is remotely managing operations of IOT gateways and edge compute applications deployed on a manufacturing floor. This migration from having personnel onsite managing and accessing devices, IoT gateways, and edge compute applications to remote cloud based management brings a new set of IoT security challenges that are primarily seen in a cloud native application. While cloud native applications are considered reasonably secure in general, there is still room for improvement. Containers, orchestrators, and APIs present in an application’s surrounding infrastructure represent new attack surfaces. In addition to the cloud service itself, each of these layers has an array of user-defined configuration settings intended to help users apply their security policies. This manual configuration is often fraught with opportunities for user error and misconfiguration, opening the IoT applications to potential security attacks.
In addition, new technology and architectural trends are emerging within the functionality of IoT management applications. These new trends change the way gateway management, security, and network management is done for IOT networks. They also alter how edge compute applications run on IoT gateways and integrate with public cloud-based platforms like Amazon Web Services, Microsoft Azure, and Google Cloud. In this technical blog we will discuss some of the emerging architectural trends in the IoT industry. They are classified as the six critical pillars of cloud native IoT management application in a hybrid cloud and multi cloud environment:
◉ Compute scalability
◉ High frequency data processing
◉ Low latency data processing
◉ Robust data processing pipeline
◉ Variety of IoT protocols
◉ Cloud native IoT messaging service
We will discuss these six critical pillars further in detail, but first let’s look at the challenges they are solving.
Challenges of distributed edge IoT data infrastructure
Distributed edge computing makes sense for a variety of use cases in IoT applications. Consider the following challenges with a cloud native integration for the distributed IoT edge:
◉ Bandwidth – traditionally the available WAN network bandwidth is a focus for data centers. However, this focus will shift towards IoT edge computing use cases as many distributed edge IoT deployments emerge.
◉ Latency tradeoff – some IoT use cases would experience increased latency if data processing happened in a cloud or fog layer and there should be a tradeoff to do it in a distributed edge paradigm.
◉ Heterogeneity– in a cluster of gateways deployed at the edge, heterogeneous compute capability of these individual gateways could affect the overall efficiency by adding dissimilar components to handle tasks for the edge compute scenario.
◉ Transparency– conceals the separated components in a distributed edge network to allow the disparate pieces to work in sync.
◉ Concurrency– allows several IoT clients to access shared resources at the edge, which creates concurrent access related problems.
◉ Security– is simpler when all compute resources are consolidated in a centralized data center but not in a distributed edge as in IoT network architectures.
◉ Backup – of dispersed IoT data requires new data protection strategies in a distributed edge IoT to cloud data pipeline paradigm.
5G enabled IoT applications require a highly dynamic response from the end to end IoT system, which creates the need for a distributed event driven edge compute service. To meet these demands, IoT application developers need a flexible and agile development environment like the cloud native approach to quickly create event driven edge compute applications running on IoT gateways. However, introducing such a cloud native approach can come with its own challenges. Take for example fleet management use cases. IoT gateways are deployed on vehicles for continuous monitoring of GPS location, collecting telemetry, and other diagnostic health information. Adding an additional distributed event processing component at the edge for communicating to a cloud native IoT application to manage these gateways could lead to an increased latency, which may eventually create OT operational issues for the end customer. Therefore, it is very important to design the edge application in a resilient and robust manner. Cisco Edge Device Management offers such capability to seamlessly integrate with Cisco IoT Operations Dashboard.
Real-world cloud native IoT illustration of transportation use case
Cisco IR829 Industrial Integrated Services Routers, Cisco Catalyst IR1100 Rugged Series Routers, and Cisco Catalyst IR1835 Rugged Series Router
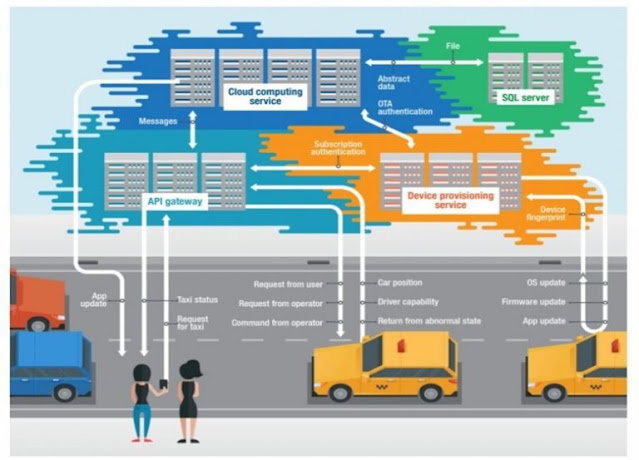
Further technical challenges that can arise in a distributed IoT Edge compute scenario as follows:
1. In connected vehicle/car related use cases the ECU’s software tech stack embedded in the vehicle is different from those of the cloud application software stack to enable quicker integration based on the API’s exposed by the cloud platforms.
2. Limited vehicle’s embedded computing resources and lack of scalability to directly integrate with a cloud native management application
3. Mobility roaming constraints specific to unstable LTE/4G WAN network link connections for exchanging telemetry data at scale in remote deployments.
5. CAN bus data decoding/encoding via protocol translation at the edge and embedded software development challenges to cater to a wide variety of automotive communication protocols
Implementing IoT cloud-based management application itself should minimize the risks that could otherwise arise from integrating edge and cloud. Enterprises can also take additional steps to ensure that their entire ecosystem is secure-from the cloud to the IoT endpoints running at the edge. We need to consider the following security specific challenges for cloud native IoT application.
◉ End to end observability
◉ Secured edge computing stack
◉ Edge cluster monitoring
◉ Secure IoT cloud convergence

End to End Cloud native IoT architectural Illustration
Embedded code is typically static and tailored to a specific platform. It is tested meticulously to ensure safe, secure, reliable, and deterministic operation. However, Cloud native IoT applications typically run on non-deterministic Linux and have many hidden library and Kubernetes clusters or other infrastructure dependencies.
They often can’t be certified to IoT standards such as IEC 61508, ISO 26262, or DO-178C. Even if they could be certified, the cost of certification is prohibitive as it is proportional to the number of effective source lines of code (eLOC) used in the system. For reference, the Linux kernel alone consists of more than 25 million lines of code. The growing number of security threats and attacks happening in the entire stack of IoT systems increase the need for end to end visibility in a cloud native application architecture. We have built a cloud native
IoT Security application to mitigate these threats.
The challenges and emerging architectural trends as discussed above for different IoT use cases in a distributed edge compute environment drive the need for a scalable cloud native IoT management application architecture.
Possible solutions
In some IoT use cases, the IoT product architectures across industries would require CEP (complex event processing) or processing high volumes of data in a 3V (volume, velocity, variety) model. This drives the need for the following IoT application capabilities classified as the six pillars of cloud native IoT management application in a hybrid cloud or multi cloud world.
◉ Compute scalability: There is an inherent need for scale up/down capability of compute processing power for building IoT applications. This is due to the variety of OT traffic spanning across IoT architectures in different industries.
◉ High frequency data processing: IoT traffic is highly bursty in nature. Therefore, processing of high volume of data without any adverse performance issues to the end-to-end system performance is critical.
◉ Low latency data processing: The majority of IoT use cases require low latency-based processing of OT traffic flows and data.
◉ Robust data processing pipeline: Since IoT requires a low overhead and no single point of failure in the data processing pipelines from the edge to the cloud, cloud native application architectures are suitable to handle robust data processing pipeline.
◉ Variety of IoT protocols: The number of IoT protocols (connectivity, message queues, streaming data, analytics, databases) and specifications of IoT standard have traditionally dealt with interface specifications and related data models, such as device-to-cloud interfaces. This requires cloud native IoT application architecture support.
◉ Cloud native IoT messaging service: The IoT industry’s definition of cloud native IoT messaging service is as follows:
◉ The standards-based offering doesn’t rely upon the services of a particular cloud vendor.
◉ Transparent, elastic scalability that can accommodate peaks and valleys in telemetry data traffic from IoT devices.
◉ Transparent fault tolerance and high availability that fulfills the service level agreements business critical IoT applications require.
◉ Ability to run on different public cloud platforms.
◉ Open API allows for the integration of the data with other cloud and third-party services.
It is easier to build IoT applications or an IoT platform using cloud native principles for both a hybrid cloud and multi cloud journey for our customers and partners. Traditionally, ICS, cyber-physical systems and other operational technology systems were dependent on embedded compute platforms. But the convergence of OT and IT in
Industry 4.0 has created a need for building cloud native IoT applications and AEP’s (Application Enablement Platforms). This need is at odds with legacy embedded code running in traditional OT systems. Cisco has built a cloud native
IoT management application, which can manage both, the life cycle of edge compute applications and the IoT gateways in a scalable manner.
Cisco IoT architectural solution
We developed Cisco IoT Operations Dashboard to solve these issues along with the technical debt incurred with Cisco’s legacy IoT management applications and based on the global macro trends seen in IoT. The Operations Dashboard comprises of the following main modules: Cisco Edge Device Management, Cisco Edge Intelligence, Secure Equipment Access, and Cisco Industrial Asset Vision. Cisco Edge Intelligence securely handles traffic routed in a hybrid cloud environment from different I/O devices PLC’s devices/OT systems to IoT applications hosted in the public cloud environment. Secure Equipment Access provides capability to remotely manage access and interact with both the gateways and connected devices. This can be used to directly troubleshoot or monitor the IoT devices in your deployment. Operations Dashboard is a cloud native application for deployment, management monitoring, troubleshooting, and gaining insights into IoT network edge connectivity, which is agnostic to different connectivity technologies.
Operations Dashboard provides the following three key services:
2. Cisco Industrial Asset Vision: Monitoring of facilities and assets using Cisco’s
industrial sensors.
3. Cisco Edge Intelligence: Edge to multi cloud data orchestration.
From a security perspective we offer a full stack observability platform with Cisco Cyber Vision, Cisco Telemetry Broker, and Cisco SecureX to complement the end-to-end security stack for a diverse set of IoT use cases. With this new cloud native paradigm, you can define each network edge as a small cloudlet for doing security analytics at the edge locally
Key takeaways
Based on these emerging market trends in the cloud native IoT application management, IoT security, and the IoT gateway management, it’s important for you to take action. Cisco IOT Operations Dashboard is based on cloud native primitives and addresses the above discussed scenarios. It leverages the available cloud native infrastructure and tools for enabling your successful journey to a hybrid and multi cloud architecture, and future-proofs your investment.
Source: cisco.com