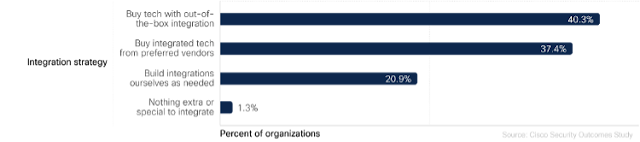What makes a successful cybersecurity program and how can organizations improve their resilience in a world that seems increasingly unpredictable? How do we know what actually works and what doesn’t in order to maximize success?
These are the types of burning questions guiding Cisco’s Security Outcomes Study series. In the second edition of the study, Cisco conducted an independent, double-blind survey of over 5,100 IT professionals in 27 countries. This article highlights data from the latest volume to focus on security resilience in the region spanning Europe, Middle East and Africa (EMEA).
The study focuses on a dozen outcomes that contribute to overall security program success. Four of them in particular are crucial for building resilience:
◉ Keeping up with the business (Security should enable, not impede)
◉ Avoiding major incidents (…And their business impacts)
◉ Maintaining business continuity (…Even when disaster strikes)
◉ Retaining talented personnel (You can’t stay on top when top staff won’t stay)
Assessing Security Resilience in EMEA
We calculated an overall resilience score for each surveyed organization based on their ratings for the outcomes listed above. The chart below compares that score across the three global regions. Organizations in the Americas scored a scant 1.7% better than the global average, while EMEA organizations landed about 2% below that mark. And the width of the gray error bars further diminishes those differences. Overall, we simply don’t see huge discrepancies in security resilience at the regional level.
Regional comparison of mean security resilience score
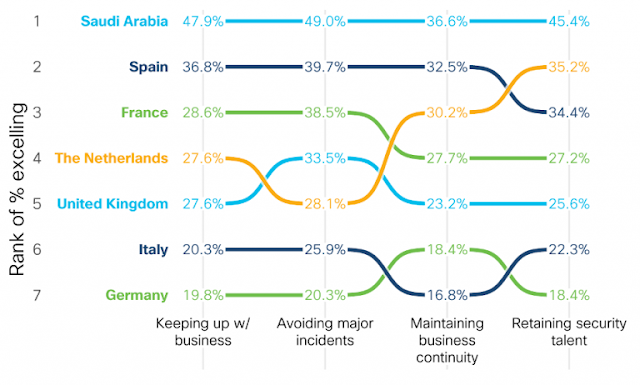
When examining resilience at the country level, however, differences begin to emerge. The next chart shows the proportion of organizations in each country reportedly “excelling” in each of the four outcomes related to security resilience. In other words, about 48% of firms in Saudi Arabia say their security program is doing a great job keeping up with the business. About 37% excel at maintaining business continuity, and so on. So, pick your country of interest and trace its success level across each outcome.
Country-level comparison of reported success levels for security resilience outcomes
Interested in comparing countries in the EMEA region across all 12 security outcomes beyond those shown here for resilience? Download the
EMEA spinoff of the Security Outcomes Study, Volume 1.
Perhaps the most interesting aspect of this chart is the comparison it provides among countries. The reported success rates by security professionals in the countries at the top are roughly twice that of those on the bottom. And for the most part, each country maintains its relative position across all outcomes.
The obvious question here is what lies behind these apparent differences in security resilience among countries? Is Saudi Arabia really that much more resilient than Germany? Might German organizations have a more realistic grasp of what it means to be resilient and know there’s a lot of work left to do? Perhaps it’s somewhere between those possibilities or something else altogether.
Whatever the reason, the key takeaway here is that success rates for all countries indicate that organizations aren’t as successful as they’d like to be in the area of security resilience.
Improving Security Resilience in EMEA
How can organizations in the EMEA region improve those outcomes, thereby making their firms more resilient? That’s an excellent question and one we were eager to explore in the
Security Outcomes Study. The study revealed five security practices—affectionately referred to as the Fab Five—that boost security program success more than any others. If you’d like a lot more information about the Fab Five and how to maximize their effectiveness, the
latest edition of the Security Outcomes Study is the place to go.

The Fab Five: Highly effective practices for achieving security program outcomes
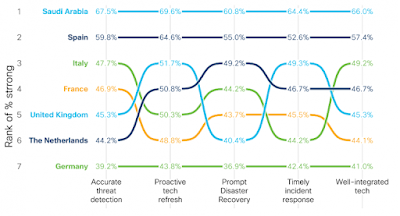
Before we examine how these practices improve resilience, let’s first check how well each country has implemented each of the Fab Five. The chart below mimics the one above for outcomes and is interpreted similarly. Once again, we see Saudi Arabia reporting the strongest implementation of these practices and Germany reporting the lowest. Countries shift around quite a bit beyond that.
Country-level comparison of reported success levels for five leading security practices
As with the outcomes chart, reasons behind these country-level differences are difficult to pinpoint. We suspect there’s a mix of maturity, cultural, and organizational factors at play. But hey, if you have thoughts, we’d love to hear them. Use #SecurityOutcomes on LinkedIn or Twitter to get our attention.
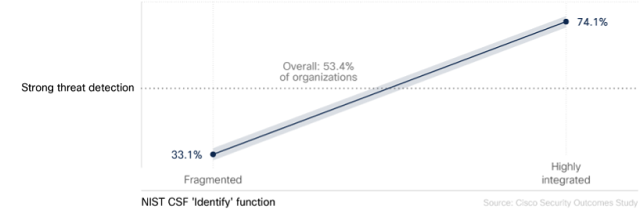
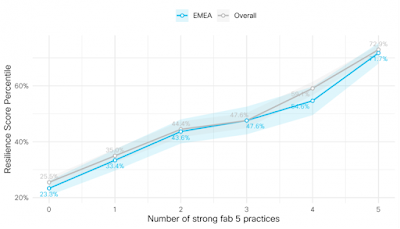
Remember that security resilience score we shared above for the regions? Great, because it’s coming back into play in this next chart. We wanted to test whether practicing the Fab Five actually improved resilience among EMEA organizations participating in our study. As seen in the chart below, that’s a definitive “Yes!”
Organizations that don’t do any of these practices well ranked in the bottom 25% for resilience, whereas those strong in all five reversed that standing and rose into the top 25%!
Effect of implementing five leading security practices on overall resilience score
Resilience has always been critical for cybersecurity. However, the last several years have really driven home the point that organizational defenders must be ready for anything. We hope this analysis demonstrates two things: 1) Organizations in the EMEA region have room for improving security resilience, and 2) It is actually possible to do so.
Source: cisco.com