Saturday, 8 October 2022
Demonstrating Trust and Transparency in Mergers and Acquisitions
Thursday, 6 October 2022
CCNA Practice Test Will Help You With the Real Exam
If you want to propel your IT and networking career by taking the CCNA certification exam, you have come to the right place! This article will impart complete information on all the CCNA syllabus topics, exam details, tips, and how the CCNA practice test can help you get a flying score.
Cisco 200-301 Exam Overview
The Cisco 200-301 or CCNA exam incorporates what an applicant should know to become a skilled networking professional. Cisco 200-301 exam covers the following topics:
- Network Fundamentals (20%)
- IP Services (10%)
- IP Connectivity (25%)
- Network Access (20%)
- Security Fundamentals (15%)
- Automation and Programmability (10%)
And mastering these topics will allow applicants to obtain the well-known CCNA certification. To focus on the fundamentals, the CCNA 200-301 exam will include 90-110 questions and needs to be finished in 120 minutes. But, the journey won’t begin until you pay the application fee - $300. After that, to help you cover what will be evaluated in this Cisco exam, the vendor provides one training course with a similar name, Implementing and Administering Cisco Solutions (CCNA), that’s completely practical and actual information-based.
CCNA is an entry-level certificate offered by Cisco, as a justification for your skill to excel in a practical networking field. Moreover, it concentrates on IT technologies and combines networking skills with technical expertise to ensure successful applicants are armed with all the essential skills in just about all domains of the digital world.
Top Tips to Crack CCNA 200-301 Exam Like a Pro
1. Know the Cisco 200-301 Exam Details In-Detail
A solid starting point for the CCNA 200-301 exam is knowing the exact CCNA syllabus topics. Indeed, you are never going to pass this exam on the first attempt if you don’t understand what it will include, how much time you will be given to finish the questions, and what task formats you will confront.
2. Build a Realistic Study Plan That You’ll Actually Stick To
A study plan is excellent, but it creates monotony, whereas creating a realistic study plan will be helpful. For the Cisco 200-301 exam, determine how much time you wish to spend on every objective, what resources you will utilize, and when you want to take the exam. Planning will also help you sidestep stress and keep you stimulated.
3. Use the CCNA Practice Test
It’s good if you wish to get a feeling of the actual exam environment before the scheduled exam date. This will help you familiarize yourself with the exam structure and boost your confidence. If you can’t deal with the Cisco 200-301 exam questions, you will inevitably know what to concentrate on to help you pass the CCNA exam on the first try. Hence, taking the CCNA practice test will be crucial to shaping your path by helping you endure an exacting 2-hour-long exam.
4. Become a Part of an Online Community and Forum
You can become a member of an online community where you can meet other exam-takers and professionals with whom you can exchange knowledge and exam tips and find explanations for your doubts. One such community is the CCNA Certification Community on the Cisco Learning Network. Here you can ask queries, exchange ideas and meet with other members studying for the CCNA 200-301 exam. It also contains links to articles that relate to CCNA prep and exams.
How CCNA Practice Test Can Help You Score Much Better in Your Cisco 200-301 Exam
Following are some of the prominent reasons behind the growing importance of CCNA practice tests-
1. Imparts Clarity of the CCNA 200-301 Exam Structure
Practicing CCNA practice tests will allow you to understand the structure of the Cisco 200-301 exam and enhance your odds of passing the exam and getting your desired score in the exam.
2. Analyze Your Weak Areas by Reviewing the Result of the CCNA Practice Test
The evaluation of the performance of your CCNA practice exam can give valuable insights into the areas you need to concentrate on well. Significantly, comprehend how much time you have dedicated to the correct answers. Find shorter ways to solve such questions in less time. This can boost your analytical skills and also give you more time to focus on questions that are tough for you.
3. CCNA Practice Test Works As a Revision of the Whole Syllabus
By performing the CCNA practice test, you can revise the whole CCNA syllabus. A CCNA practice test assesses your skills for the exam and knowledge of the resources you own. Regular practice of CCNA practice tests can strengthen the frequently asked pieces of information and techniques used, and your brain becomes better at recovering them every time. This can help you prepare well for the exam with focus and perseverance.
Also Read: Make Your Resume Competitive With CCNA 200–301 Certification
4. CCNA Practice Test Helps Overcome Exam Anxiety
Finally, any exam can yield a lot of stress, mainly if one isn’t prepared adequately. A CCNA practice test helps you mentally and psychologically ready for an exam and understand how it would feel when solving it.
You learn how to control your anxiety under pressure and concentrate on answering CCNA 200-301 exam questions without worrying about the result. If you score well in a CCNA practice test, it gives you confidence while acing the actual exam.
Conclusion
It’s not possible to think about a career in IT infrastructure and networking without cracking the Cisco 200-301 exam. And to become certified as well as confirm your expertise, you should take up appropriate training and CCNA practice tests. For that, follow the top tips mentioned in this article to pass this exam like a pro. Good Luck!!
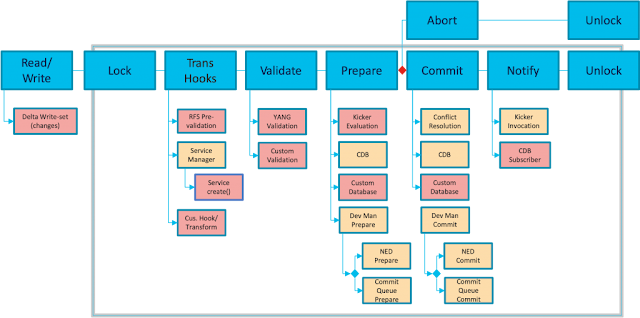
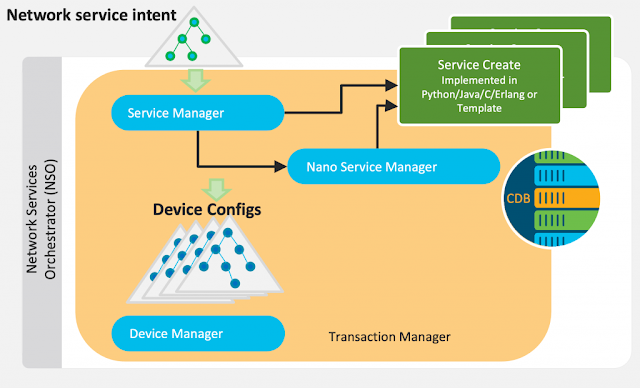
How NSO 6.0 Delivers Up To 9x Faster Transaction Throughput
Shaping NSO for Increasing Demand
The New Concurrency Model
Unexpected Outcomes
Sometimes it Pays Off to Dare a Little More
Tuesday, 4 October 2022
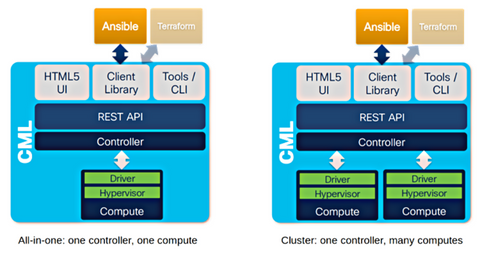
CML 2.4 Now Supports Horizontal Scale With Clustering
When will CML 2 support clustering?
This was the question we heard most when we released Cisco Modeling Labs (CML) 2.0 — and it was a great one, at that. So, we listened. CML 2.4 now offers a clustering feature for CML-Enterprise and CML-Higher Education licenses, which supports the scaling of a CML 2 deployment horizontally.
But what does that mean? And what exactly is clustering? Read on to learn about the benefits of Cisco Modeling Labs’ new clustering feature in CML 2.4, how clustering works, and what we have planned for the future.
CML clustering benefits
How clustering works in CML v2.4 (and beyond)
Defining a controller or a compute during CML 2.4 cluster installation
CML 2.4 scalability limits and recommendations
Saturday, 1 October 2022
Empowering the four IT personas using Cisco DNA Center with Rings of Power
There are many variations of the “Law of Constant Change”; while they all have their own spin on it, the common thread is that change is constant and that it needs to be harnessed. When looking at changes and disruptions in technology, it comes as no surprise that there are numerous transformations and trends which are reshaping the IT landscape. The megatrends and change drivers span a wide range of business changes and transformation agents such as:
Thursday, 29 September 2022
[New] 200-301 CCNA: Cisco 200-301 Free Exam Questions & Answers
Cisco CCNA Exam Description:
Cisco 200-301 Exam Overview:
- Exam Name- Implementing and Administering Cisco Solutions
- Exam Number- 200-301 CCNA
- Exam Price- $300 USD
- Duration- 120 minutes
- Number of Questions- 90-110
- Passing Score- Variable (750-850 / 1000 Approx.)
- Recommended Training- Implementing and Administering Cisco Solutions (CCNA)
- Exam Registration- PEARSON VUE
- Sample Questions- Cisco 200-301 Sample Questions
- Practice Exam- Cisco Certified Network Associate Practice Test
Cisco 200-301 Exam Topics:
- Network Fundamentals- 20%
- Network Access- 20%
- IP Connectivity- 25%
- IP Services- 10%
- Security Fundamentals- 15%
- Automation and Programmability- 10%
- CCNA Practice Test: Your Best Assistants to Tackle CCNA 200-301 Exam
- CCNA 200-301 Exam: Details, Preparation Options and Career Scope
- Why Is CCNA Practice Test Important for Cisco 200-301 Exam Preparation?
- Why Now Is the Time to Pass CCNA 200-301 Exam?
- Will CCNA Practice Test Have an Impact on Cisco 200-301 Exam Score?
- Some Useful Tips to Pass Cisco 200-301 Exam Using CCNA 200-301 Practice Test
- Prepare for CCNA 200–301 Exam With CCNA Practice Test
- Appearing For CCNA 200-301 Exam? CLICK HERE.