- CML_USERNAME: Username for the CML user
- CML_PASSWORD: Password for the CML user
- CML_HOST: The CML host
- CML_LAB: The name of the lab
Thursday, 18 January 2024
How to Use Ansible with CML
Tuesday, 16 January 2024
Using the Knowledge Store on Cisco Observability Platform
Build custom observability solutions
Get a step-by-step guide
- The knowledge store is a JSON document store
- A solution package can define a Type, which is akin to adding a table to a database
- A Type must specify a JSON schema for its allowed content
- A Type must also specify which document fields uniquely identify documents/objects in the store
- A solution may include objects, which may be of a Type defined in the solution, or which were defined by some different solution
- Objects included in a Solution are replicated globally across all cells in the Cisco Observability Platform.
- A solution including Types and Objects can be published with the fsoc command line utility
Provide value and context on top of MELT data
Saturday, 13 January 2024
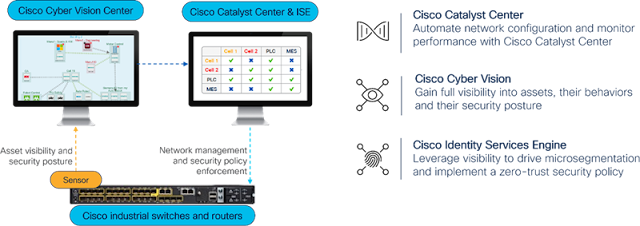
Cisco wins Manufacturing Solution of the Year award for integrating industrial security with networking
An integrated network and security architecture
Put the award-winning solution to work for you
Monday, 8 January 2024
How Can 350-501 SPCOR Exam Help You Obtain CCNP Service Provider Certification?
To attain the CCNP Service Provider certification, you must pass two exams: one core exam and one concentration exam of your choice:
Cisco 350-501 SPCOR Exam Details
The Cisco 350-501 SPCOR exam is a 120-minute test that covers 90-110 questions on the following topics:
The test is offered in English, and the fee for the exam is $400.
Quality Study Materials and Various Preparation Alternatives for Exam Prep
There are specific methods for thoroughly understanding exam details and topics. Various preparatory resources have been designed to instill confidence in candidates preparing for any Cisco test, ensuring their success and eventual certification as specialists. The following are some of the widely used study materials available for applicants:
Be sure to utilize these resources wisely to achieve the necessary scores. Nevertheless, more than merely having a wealth of excellent materials is required. It is crucial to remain dedicated and maintain consistency in your studies.
Cisco 350-501 SPCOR Exam Preparation Tips
1. Setting Clear Goals for Exam Preparation
Start your preparation journey by defining clear study objectives. Create a realistic study schedule that aligns with your daily routine. Setting achievable goals will help you stay focused and motivated throughout preparation.
2. Utilizing Official Cisco Resources
Cisco provides official study materials that are tailored to the exam objectives. Leveraging these resources ensures that you cover the essential topics comprehensively. Additionally, explore Cisco's online courses and webinars for interactive learning experiences.
3. Exploring Third-Party Study Resources
While official resources are crucial, supplement your study materials with reliable books and study guides from reputable authors. Engage with online forums and discussion groups to exchange insights with fellow exam takers and gain diverse perspectives.
4. Hands-On Practice and Lab Exercises
Theory is vital, but hands-on practice is equally important. Set up a virtual lab environment to apply your knowledge in a practical setting. This approach enhances your understanding of concepts and boosts your confidence in tackling real-world scenarios.
5. Effective Time Management
Balancing work, study, and personal life can be challenging. Develop time-saving study techniques and adhere to a well-structured schedule. Efficient time management is critical to covering all exam objectives thoroughly.
6. Staying Updated with Industry Trends
The world of networking is dynamic, with constant advancements. Stay informed about industry trends and incorporate real-world scenarios into your study sessions. This ensures that your knowledge is exam-oriented and relevant in the ever-evolving field.
7. Building a Support Network
Joining study groups and seeking guidance from experienced professionals can significantly enhance your preparation. Share insights, ask questions, and learn from others' experiences. A support network provides motivation and a valuable source of information.
8. Mock Exams and Self-Assessment
Practice tests are invaluable in gauging your preparedness. Take mock exams to identify weak areas and focus on improving them. Regular self-assessment ensures that you enter the exam confidently and well-prepared.
9. Mindfulness and Stress Management
Exam anxiety is natural, but managing stress is crucial. Incorporate mindfulness techniques and relaxation exercises into your routine. A calm mind enhances cognitive function and effectively helps you tackle exam-related stress.
10. Continuous Learning Beyond the Exam
Certifications open doors, but the learning journey continues after the exam. Consider certifications as a part of your broader career development. Explore additional resources for ongoing education and professional growth.
11. Common Mistakes to Avoid
Be aware of common pitfalls in exam preparation. Whether it's procrastination, lack of focus, or over-reliance on certain study materials, understanding and avoiding these mistakes will contribute to your success.
Conclusion
In conclusion, success in the Cisco 350-501 SPCOR exam requires a well-rounded and strategic approach to preparation. You can enhance your chances of success by setting clear goals, utilizing diverse resources, and maintaining a support network. Remember, the journey is as important as the destination.
Saturday, 6 January 2024
Synchronizing Technology and Organizational Culture for Optimal Outcomes
Understanding the Challenge of Martec’s Law and Strategically Adopting Technology
Effective Application of Martec’s Law to Enhance Organizational Outcomes
Leveraging Cisco’s Insights and Best Practices
Orchestrating Technological and Cultural Change: A Customer Success Focus
Addressing Current (and Future) Federal Mandates with an Integrated Multi-Architecture Approach
Conclusion: Seizing the Opportunity to Shape the Future
In a Nutshell
Thursday, 4 January 2024
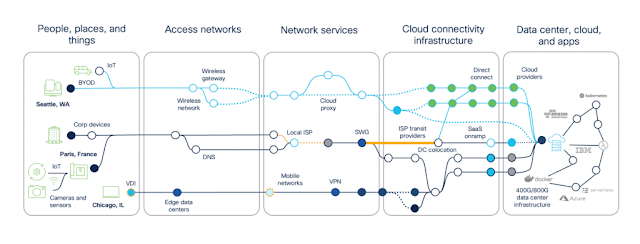
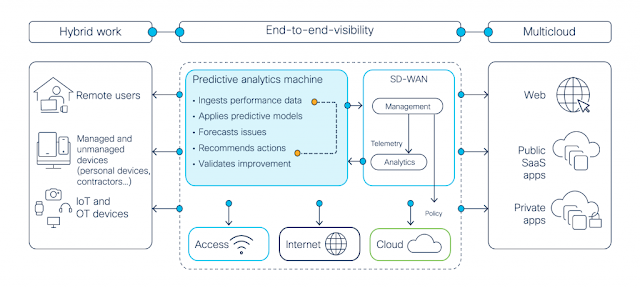
AIOps Drives Exceptional Digital Experience Through Network Assurance
Predictive analytics for SD-WAN and an internet-centric world
Predictive analytics at work in the real world
Predictive and proactive operations is the way forward
Tuesday, 2 January 2024
5 Environmental Sustainability Trends for 2024
Reflections from COP28
Environmental sustainability trends for 2024 and beyond
- In 2015, the UN-brokered Paris Agreement established an international treaty on climate change. To limit global warming to 1.5°C, greenhouse gas (GHG) emissions must peak before 2025 at the latest and decline 43% by 2030. Plans and targets were made by countries and organizations globally to achieve this.
- As we get closer to that milestone, it’s becoming increasingly clear that there is no consistent or accurate way to measure progress, both within countries and industries, and globally, to hold us accountable.
- Pressure is growing on both the public and private sector, with demands for mandatory reporting now a worldwide refrain.
- Regulatory bodies are now considering approaches that can deliver concrete outcomes, but data sources are varied in quality, reporting is fragmented, and many organizations lack the technology to generate and analyze the data they require.
- 2024 could see this come to a head with the emergence of new industry standards with a focus on GHG emissions accounting and climate impact materiality. The tech industry can play a critical role in delivering enabling technologies that will help companies monitor and assess their footprint.
- Many traditional ‘power grids’ are already being stretched to their limits, and increasingly common weather phenomena will continue to add more and more stress. In the U.S., the North America Electric Reliability Corporation warned that much of the U.S. power grid is at an increased risk of failure during major storms or long cold snaps this winter. (Source: 2023–2024 NERC Winter Reliability Assessment)
- At the same time, the growth of renewables demands a more efficient grid to allow renewables to become more viable and avoid the conversion losses all too common in today’s grids. (Source: Digitalizing Europe’s energy system to power the green energy revolution)
- Micro grids have already begun to show their viability, which may start encouraging more ideas in harnessing them.
- In order to avoid dangerous and costly failures of energy delivery systems, businesses and the public sector must begin now to address the future needs of the grid.
- We know that AI workloads increase demand for electricity and water as they place enormous demands on data center infrastructure. (Source: The AI Boom Could Use a Shocking Amount of Electricity) But the benefits of AI for sustainability have the potential to outweigh that impact.
- Like many other areas, data will be crucial to tackling sustainability challenges. With the promise of AI to make sense of data and offer crucial insights, sustainability could benefit greatly from the application of AI.
- AI is only as good as the data it is being fed. So, the emergence of AI may also help solve another major challenge in sustainability: accurate and consistent measurement and the need for centralized and common tooling.
- Power over Ethernet (the coupling of connectivity and power delivery on the same cable) was first adopted as an IEEE standard in 2003. Since then, use cases for PoE have been varied, but fairly niche, as the vastly preferred method of electrical connectivity remains copper wiring.
- The need for buildings to become smarter has never been greater. Building operations and construction accounted for an estimated 37% of CO2 emissions globally in 2021. PoE will allow builders, owners and tenants to use the network to deliver power and connectivity together, enabling a true smart building.
- Technological developments are an important part of strategies to mitigate climate change, but discussions at COP28 reinforced the critical role of nature-based solutions, like protecting forests or restoring coastal marshes.
- We must innovate and fill gaps in our understanding of nature-based solutions and when to use them. We must deliver climate mitigation, safeguard biological diversity, improve food security, and create more inclusive and resilient communities.
- Anticipate an uptick in projects that leverage nature’s capabilities, such as afforestation, reforestation, and sustainable land management.