Fueling digital transformation success with cost and resource optimization over applications, workloads, and components
Digital transformation comes with an irony that is not lost on the IT teams. Applications and the digital experiences they enable require cloud-based resources for which costs can easily spiral out of control. Worse, lack of visibility means that utilization of these resources can be difficult to accurately assess.
This creates a conundrum. Fast, reliable application performance depends on sufficient allocation of cloud resources to support demand, even when usage spikes. Under-resourcing in this area can cause significant performance challenges that result in very user experience. With this in mind, teams responsible for migrating workloads to the cloud or spinning up resources for new applications can often over-provision cloud resources to be on the safe side.
The more complexity that is introduced by sprawling suites of tools, containers, application programming interfaces (APIs), and serverless components, the more ways there are to incur costs. And the more ways there are to fall short of efficiency goals as cloud resources sit idle.
As a result, technologists are under pressure to find out where costs are out of alignment and whether resources have been allocated in ways that support the business.
Taking the guesswork out of optimization
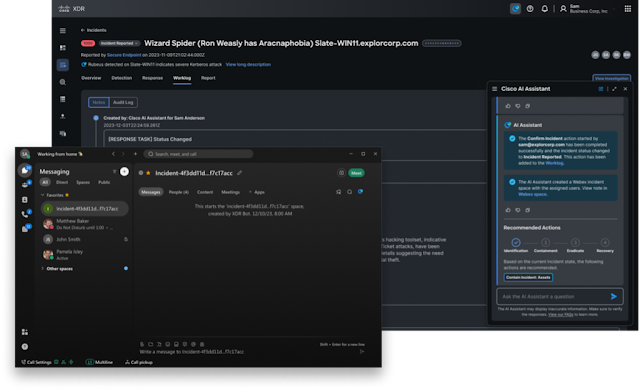
Cisco Full-Stack Observability allows operational teams to gain a broad understanding of system behavior, performance, and security threats across the entire application estate. It also equips them to understand and optimize cloud resource utilization. This optimization helps organizations lower costs by properly modulating asset utilization across workloads, paying only for what they need through right-sizing resource allocation.
It offers optimization capabilities for resolving poorly aligned cloud spend with actionable insights into hybrid costs and application resources within their established monitoring practices. While over-provisioning to avoid downtime is wasteful from both a budgetary and sustainability perspective, under-allocation presents a serious risk.
When applications are constrained by insufficient resources, the resulting poor application performance or even downtime can damage organizational reputation and revenues. With Cisco Full-Stack Observability, teams can scale up or down to ensure resources sufficiently support workloads.
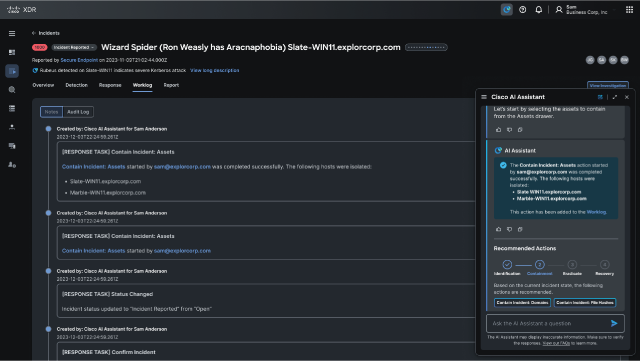
Moreover, Cisco Full-Stack Observability solutions provide visibility into application-level costs alongside performance metrics down to the pod level. It helps perform granular cost analysis of Kubernetes resources, allowing FinOps and CloudOps teams to understand the composition of their cloud spend as well as the cost of resources that are idle. Armed with granular cost insights, organizations can mitigate overspending on unused resources while ensuring that critical applications have adequate resources.
Driving optimization with AI and ML
Artificial intelligence (AI) is driving change in observability practices to improve both operational and business outcomes. Cisco Full-Stack Observability combines telemetry and business context so that AI and machine learning (ML) analytics can be uniformly applied. This allows IT Operations teams to extend their value and truly be strategic enablers for their business.
For example, application resource optimization with Cisco Full-Stack Observability takes aim at inefficiencies in Kubernetes workload resource utilization. By running continuous AI and ML experiments on workloads, it creates a utilization baseline, analyzing and identifying ways to optimize resource utilization. The resulting recommendations for improvement help to maximize resource usage and reduce excessive cloud spending.
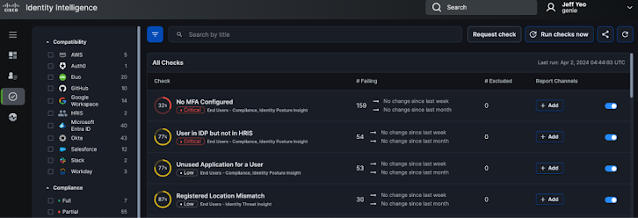
Cisco Full-Stack Observability offers capabilities, moreover, to identify potential security vulnerabilities related to the application stack and optimize the stack against these threats. It continuously monitors for vulnerabilities within applications, business transactions, and libraries with the ability to find and block exploits automatically. The result is real-time optimization without constant manual intervention.
To understand and better manage the impact of risks on the business, Cisco security solutions use ML and data science to automate risk management at multiple layers. First, code dependencies, configuration-level security vulnerabilities, and leakage of sensitive data are continually assessed. Second, business priorities are established through a measurement of risk probability and business impact.
This comprehensive approach to optimization makes Cisco Full-Stack Observability a powerful solution for modern, digital-first organizations.
Source: cisco.com