In short, SD-WAN has arrived and organizations are deploying it worldwide. So what can we look forward to as this technology enters its next phase? Let me preview some of the ways we are working to bring even more control, functionality, and flexibility to SD-WAN.
Turning the Internet into a Manageable and Secure WAN
One of the key features of SD-WAN is the ability to use multiple connectivity options simultaneously to always have the most reliable or appropriate connection for application Quality of Experience. Specifically, you can choose among the options available for the location: MPLS, Ethernet, internet, leased lines, DSL, LTE networks, and soon 5G. It’s this flexibility to choose the most cost-effective and best-performing connectivity option available to provide the ideal application experience for each location of a distributed workforce. For example, need to ensure that Office 365 Cloud is performing as needed at branch offices? Instead of relying on an expensive MPLS connection backhauling to headquarters for connections to multicloud applications, use a secure Direct Internet connection to the Microsoft Cloud, which is continuously monitored by SD-WAN to meet performance SLAs.
What’s next? The ability to manage end-to-end connectivity from enterprise to 5G endpoints and back will bring greater levels of control over data traffic and application performance. The key to extending intent-based networking controls from enterprise to 5G cellular endpoints is network slicing in the 5G channels in conjunction with micro-segmentation in the enterprise. 5G slicing enables the carrier to separate traffic into unique partitions, keeping sensitive data separate from normal traffic. The technique enables 5G providers to maintain the necessary service level agreements for low-latency traffic, and create an end-to-end virtual network encompassing compute and storage functions.
Wired and wireless Enterprise networks are already segmented to channel traffic according to type (sensitive/video/IoT), priority, and latency. Today with 4G LTE, the enterprise segmented traffic destined for a cellular endpoint would move onto the cellular network with few controls over how the data is segmented and managed. The new 5G networks can be sliced to match the security and performance requirements of the segments in the enterprise, thus maintaining the original policies from end-to-end. A security policy, for example, that is established in the enterprise network will follow a person’s device as it transitions from the enterprise to a 5G network slice. Cisco SD-WAN will be able to take full advantage of network slicing in 5G to meet the security and segmentation needs of enterprise networks.
Virtualizing Network Functions for the SD-Branch
Bringing the focus back to ensuring robust branch connectivity, we are enhancing the functions that run on the local edge routers and appliances along with the core SD-WAN software suite. Virtualizing network functions (VNF) increases local performance and minimizes backhaul traffic to corporate data centers DMZs or cloud platforms. Many functions are being virtualized on edge routers and appliances—such as optimization and intelligent caching, application-aware firewalls, intrusion detection, and URL filtering. And, of course, SD-WAN’s full security stack supports compliance, direct internet access, direct cloud access, and guest access.
Virtualizing critical functions and running them at the cloud edge—in the branch office, store, or clinic—improves both the efficiency and cost-effectiveness of distributed computing and a remote workforce. VNFs can also be run on cloud platforms and colocation facilities to spread the functionality over multiple remote locations. For example, by consolidating VNFs on a provider’s IaaS platform—a virtual network hub—IT can reduce management costs while being able to spin up or down new virtual machines as needed to accommodate workloads and connectivity for a group of regional branches. More on this in a future blog post.
Improving Application Quality of Experience with WAN Optimization
WAN optimization techniques have been around since the early days of frame relay and MPLS. The main goal of dedicated optimization appliances was to maximize the throughput on these relatively expensive circuits. As new technologies such as VoIP and video became critical to business, optimizing the circuits to provide the necessary Quality of Service grew in importance. But as direct internet connections became the rule rather than the exception for accessing popular SaaS and cloud apps, a much more granular, flexible, and automated WAN optimization process is required. Thus SD-WAN was designed to meet the new application QoE demands.
There are several optimization methods that Cisco SD-WAN currently employs to improve the QoE for cloud and SaaS applications accessed by the distributed workforce. Currently, Cisco SD-WAN monitors the available links for latency, packet loss, and jitter that affect throughput and performance. By dynamically measuring these characteristics and comparing them with service levels that specific applications require, the SD-WAN can automatically decide which circuits to use for individual applications. VoIP and video are two applications that require specific levels of latency and low jitter to perform correctly. While a SaaS application may be more tolerant of jitter, it still requires a guaranteed level of throughput to provide satisfactory performance. SD-WAN automates the monitoring and selection of appropriate paths to maintain expected QoE for each type of application.
Supplementing these existing performance attributes of SD-WAN are new controls for TCP optimization, forwarding correction, and packet duplication. SD-WAN provides metrics that aid in fine tuning the optimal TCP congestion algorithm to improve application performance. For example, the Cisco SD-WAN TCP optimization engine, a new layer in the Cisco SD-WAN stack, helps maintain superior application performance in high latency networks such as satellite, transcontinental, and other types of circuits prone to high-loss and high-latency.
To better tackle lossy networks, even for non-TCP applications, the Cisco SD-WAN optimization stack includes a Forward Error Correction (FEC) mechanism. FEC improves application experience by using additional parity packets to protect against loss. In situations when the loss percentage is very high, the Cisco SD-WAN optimization stack maintains performance by deploying a Packet Duplication feature. These optimization features help mitigate packet loss over noisy channels, thereby maintaining high application QoE for voice and video in particular. They are being integrated into the Cisco SD-WAN stack in upcoming IOS-XE releases. All three optimization techniques are managed via Cisco vManage and vSmart virtual network functions.
Edge-to-Cloud Protection with Integrated SD-WAN Security Stack
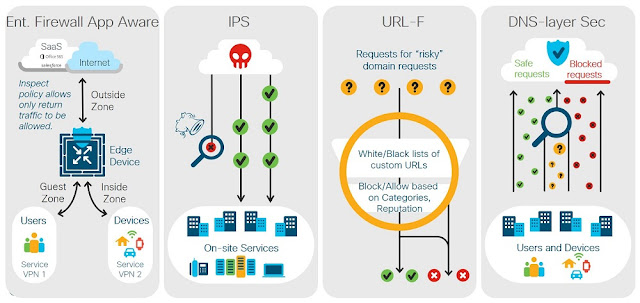
Securing branch to cloud to data center traffic, in all its permutations, is a key strength of SD-WAN. Last year Cisco added a virtualized security stack to provide multiple levels of protection at the cloud edge that includes:
- Application-Aware Enterprise Firewall with the ability to identify, permit, or block over 1400 applications.
- Intrusion Protection System (IPS) using Snort, the most widely deployed IPS engine in the world, to deliver real-time network defense against malware intrusions.
- URL-Filtering with advanced reporting on over 80 URL categories, providing IT with greater visibility and reducing risk with usage policies customized to an organization’s unique needs.
- DNS/web-layer security with integrated connections to Cisco Umbrella to prevent enterprise branch users, guests and mobile users from accessing inappropriate internet content and known malicious sites that might contain malware and other security risks.
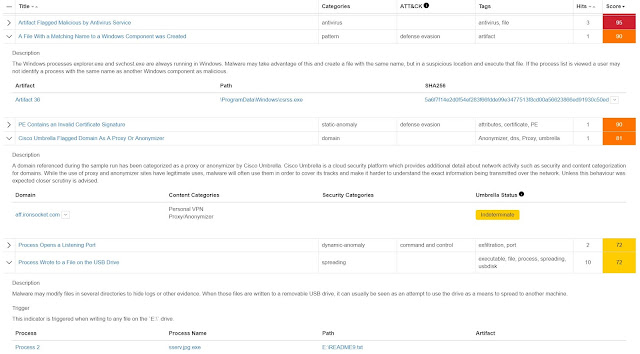
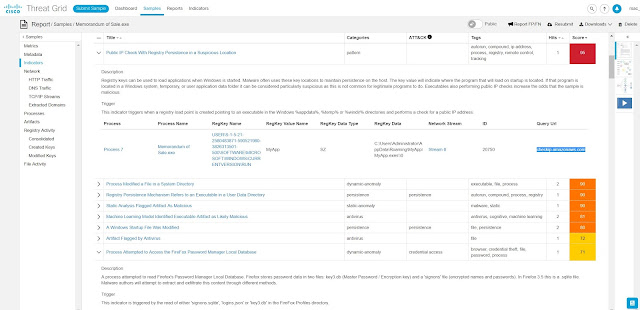
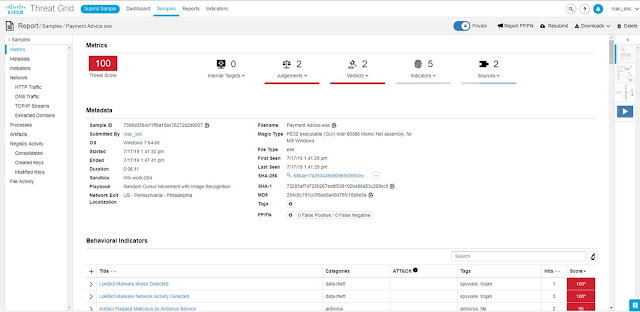
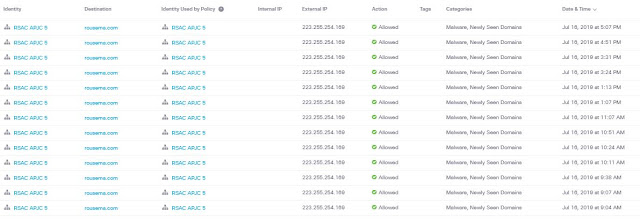
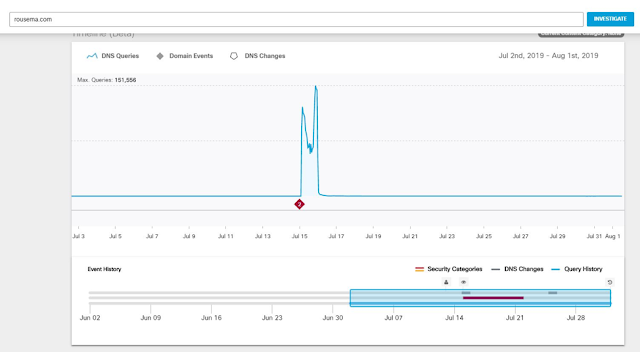
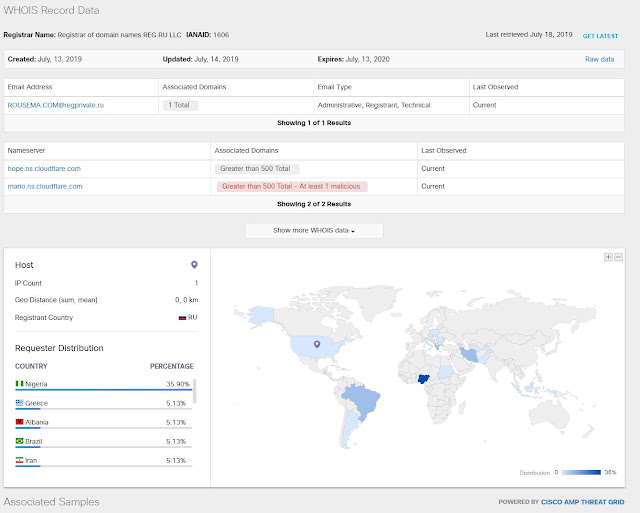
Coming soon to a Cisco edge router near you is Cisco Advanced Malware Protection (AMP) Threat Grid operating as a virtual network function (VNF). The additional AMP-focused layer includes a context-aware knowledgebase of known malware infectious agents. Cisco AMP Threat Grid identifies and alerts IT staff of discovered infections, and provides information on the malware method of attack, a measure of the threat it poses, and how to defend against it. Operating at the branch edge, with the SD-WAN VNF security stack, AMP Threat Grid provides a layer of malware protection, examining all incoming and outgoing traffic, ensuring that malware originating from direct internet connections can’t infect branch devices. Similarly, malware originating from the branch can’t hide in traffic outbound to the enterprise network or cloud applications.
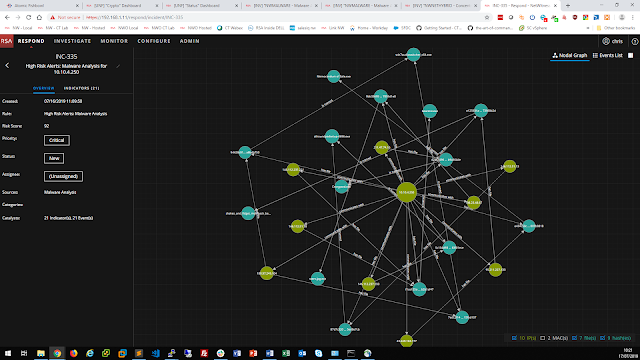
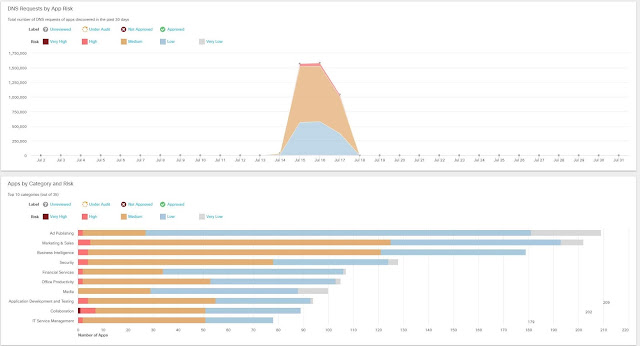
Threat insights exposed with AMP Threat Grid are viewable through the Cisco vManage Portal where administrators can also initiate protective actions such as segmenting infected devices from the rest of the network. The vManage Portal gives network admins a view across the entire WAN, displaying all suspected infections, malware type, and paths of infection through the network. To augment security threat intelligence, the VNF instances of AMP Threat Grid working at the local edges are continuously connected to both AMP Cloud and Threat Grid Cloud, both managed by Cisco Talos Security.
AMP Cloud and Threat Grid Cloud collect malware and suspicious file data from Cisco installations around the world, maintaining a Malicious File Hash catalogue of suspected infections and keeping the information up to date on all Cisco routers as well as third-party security tools via an open API. For example, API integration of AMP Cloud and Threat Grid Cloud with application-aware, threat-focused firewalls provides rapid identification of suspected malware files with automated sandboxing of unknown files in the Threat Grid Cloud for additional analysis.
SD-WAN Continues to Improve Branch Connectivity, Application QoE, and Security
Cisco SD-WAN is foundational for a new software-defined network architecture. As organizations become more distributed, the workforce needs new ways to connect edge to cloud, data center to branch, while ensuring a high Quality of Experience for cloud and SaaS applications wherever they are needed. Cisco is at the forefront of this new wave of distributed connectivity, continuously refining our SD-WAN software and security stack to meet the needs of the digital enterprise.