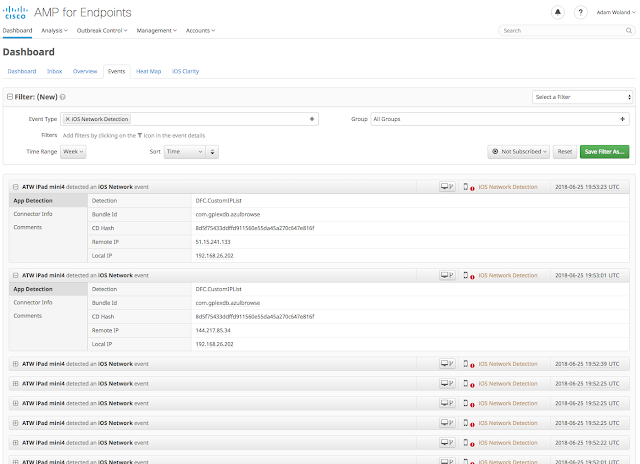
When downloading an application from the App Store, do you actually check the logistics of it? For example, how is it connecting to the internet? Or an even more relatable scenario: that game you were playing while waiting in line paused to present an advertisement, was it triggered by an IP address or a DNS request? The majority of times, users don’t check or understand those nitty gritty details. We simply see something we like, click, and begin launching the app onto our devices.
However, what if that application is connecting to a malicious IP address? And in a case that your employee is using a corporate-owned iOS device and downloads that app; this presents a security gap.
The Umbrella extension within Cisco Security Connector serves as a first line of defense against threats by protecting users from malicious domains. Umbrella delivers both DNS-layer encryption and enforcement on top of an intelligent proxy that provides URL and file inspection for risky domains. Therefore, when your employee attempts to make any connections to the internet, Cisco Security Connector is there to protect your business against suspicious app and user-initiated network requests.
But applications can also connect to malicious IP addresses. To counter that, Cisco Security Connector is continuing to innovate with a newly added IP Blocking feature as a part of Clarity. This IP Blocking feature now provides complete network protection for your corporate-owned iOS devices. With just a few clicks, adminscan simply add a suspicious IP address to their blacklist and regulate that list accordingly; giving more control to businesses. Now, whether it’s a direct IP connection or DNS request, Cisco Security Connector can secure your users end-to-end.
Cover All Your Bases: IP Addresses and DNS Requests
The Umbrella extension within Cisco Security Connector serves as a first line of defense against threats by protecting users from malicious domains. Umbrella delivers both DNS-layer encryption and enforcement on top of an intelligent proxy that provides URL and file inspection for risky domains. Therefore, when your employee attempts to make any connections to the internet, Cisco Security Connector is there to protect your business against suspicious app and user-initiated network requests.
But applications can also connect to malicious IP addresses. To counter that, Cisco Security Connector is continuing to innovate with a newly added IP Blocking feature as a part of Clarity. This IP Blocking feature now provides complete network protection for your corporate-owned iOS devices. With just a few clicks, adminscan simply add a suspicious IP address to their blacklist and regulate that list accordingly; giving more control to businesses. Now, whether it’s a direct IP connection or DNS request, Cisco Security Connector can secure your users end-to-end.
Image: iOS Events List
Cisco Security Connector
Cisco Security Connector allows businesses to gain deep visibility and control across all devices. With the ability to integrate with existing MDM/EMM such as Cisco Meraki Systems Manager, VMware AirWatch Cloud EMM, and MobileIron on-premises EMM, Cisco Security Connector ensures ease of deployment as well as adaptability to a business’s current environment.
With similar Cisco Advanced Malware Protection (AMP) capabilities extended to iOS devices, users can now gain insight into all application and device behaviors on all devices. Though most importantly, as part of the AMP console, admins can now have one single location to manage all their endpoints.
Unfortunately, we can’t control our employee’s actions on our network, but what we can control are the results of it. So, cover all your bases with Cisco Security Connector.