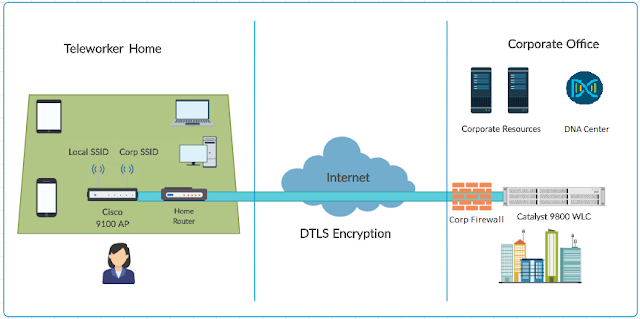
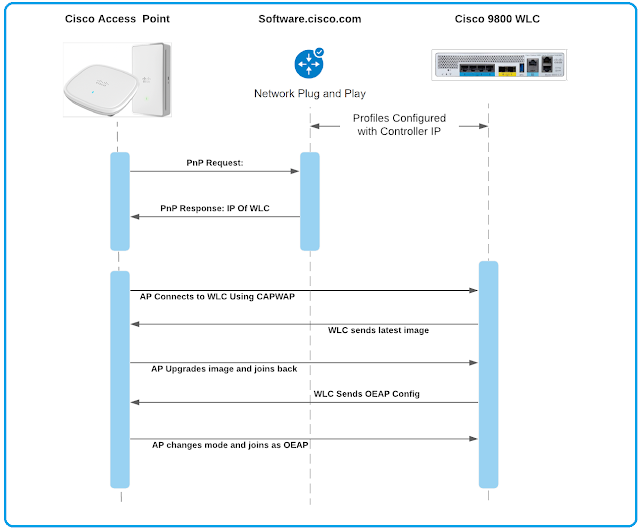
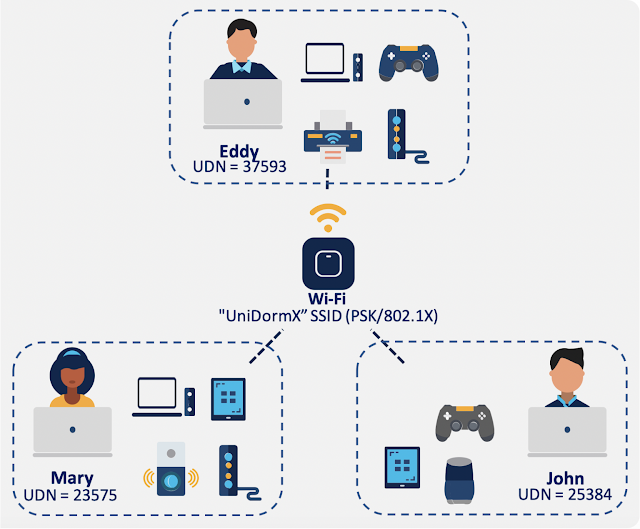
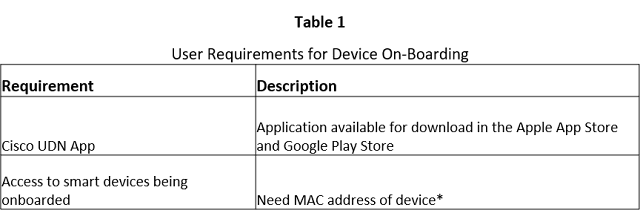
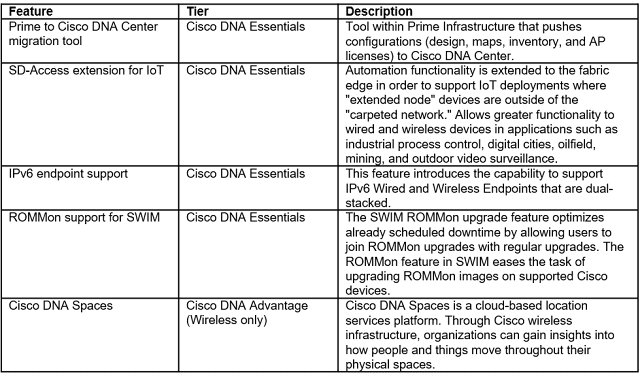
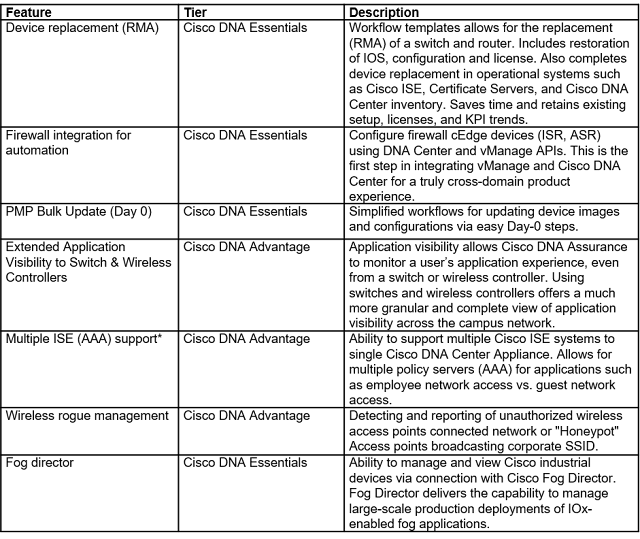
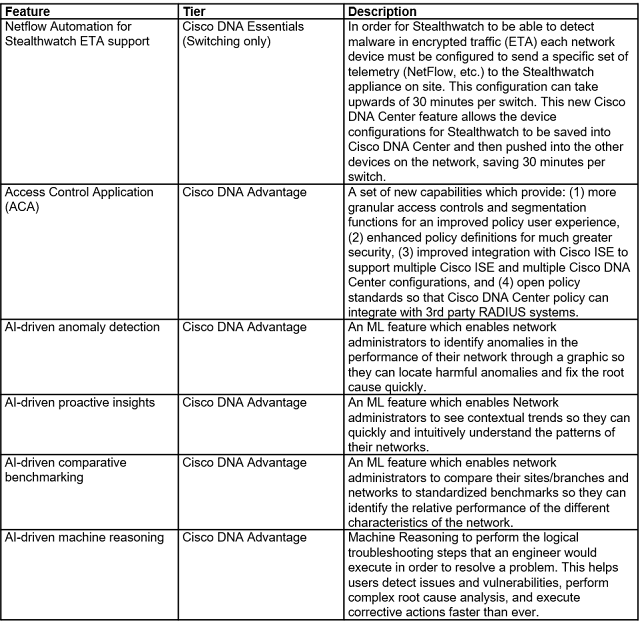
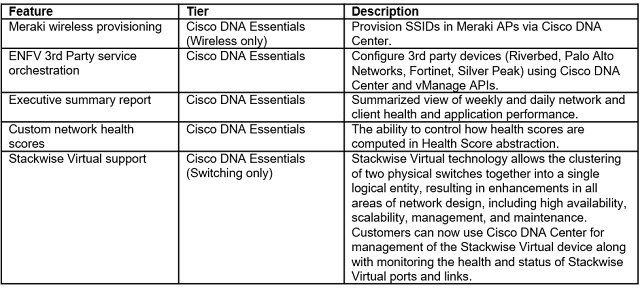
In this unprecedented time where remote work has expanded and become the norm – Webex continues to innovate to give our customers the tools they need to keep their remote workers secure – whether they’re on the go on their personal mobile devices or safely working from home using company managed devices.
Mobile Webex IT Administrators have been clamoring for more granular policy enforcement tools and also more integrations with their existing tool sets. To solve for both of these, Webex now has integration with Microsoft Intune Mobile Application management, including:
◉ Passcode/Touch ID
◉ Document sharing
◉ Preventing application backup
◉ Disabling screen capture
◉ Enforcing Application Encryption
◉ Disabling Copy and Paste
◉ Remote Application Wipe
And for those customers who aren’t using Intune, Webex allows them to secure the Webex mobile apps by self-wrapping it with their preferred Mobile Application Management solution SDK by providing app binaries.
In addition, Webex now supports AppConfig – the industry standard for Mobile Application Management. Customers can deploy several policies like disable copy and paste across virtually any MDM solution.
Finally, Webex is continuing to augment native Control Hub Mobile Application Management controls and just released a capability to block message notifications on mobile screens to prevent against data loss on unattended devices.
New Mobile Security and Granular Controls
Mobile Webex IT Administrators have been clamoring for more granular policy enforcement tools and also more integrations with their existing tool sets. To solve for both of these, Webex now has integration with Microsoft Intune Mobile Application management, including:
◉ Passcode/Touch ID
◉ Document sharing
◉ Preventing application backup
◉ Disabling screen capture
◉ Enforcing Application Encryption
◉ Disabling Copy and Paste
◉ Remote Application Wipe
And for those customers who aren’t using Intune, Webex allows them to secure the Webex mobile apps by self-wrapping it with their preferred Mobile Application Management solution SDK by providing app binaries.
In addition, Webex now supports AppConfig – the industry standard for Mobile Application Management. Customers can deploy several policies like disable copy and paste across virtually any MDM solution.
Finally, Webex is continuing to augment native Control Hub Mobile Application Management controls and just released a capability to block message notifications on mobile screens to prevent against data loss on unattended devices.
Securing Your Remote Workforce with Granular Tools
Another capability that we’ve added blocking file share for groups. For instance, you may have a group of contractors in your company and you don’t want to run the risk of your contractors sharing sensitive data files from their desktop – so now you set up policies for groups from sharing their files – based on their group classification in your active directory. Using Cisco Directory Connector – Webex administrators can get group information directly from their active directories – directly from the Webex Control Hub. They can set up groups of people – like contractors vs. employees; investment bankers vs. retail bankers; or groups of those who provide patient care vs. those in financial administration.
Figure 1 – Active Directory groups in Webex Control Hub
Without having to back to their active directories – Webex admins can:
◉ View all active directory groups
◉ Search for a specific active directory group
◉ View all members in an active directory group
◉ View group attributes like usage, type, owner and number of members
Webex Control Hub gets this information by syncing with the customer’s active directory. And customers can choose how frequently they sync and when and what to sync. This is such a streamlined workflow for customers who are accustomed to having to sync by individual user. And we’ll be adding new security controls based on Active Directory groups in the future.
Additionally, Webex Admins can:
◉ Control file upload control or file upload and download control
◉ Only allow people to upload when they are on the corporate VPN network
◉ Define their network location by IP range and IP addresses – and they can enable file sharing restrictions based on those addresses & ranges
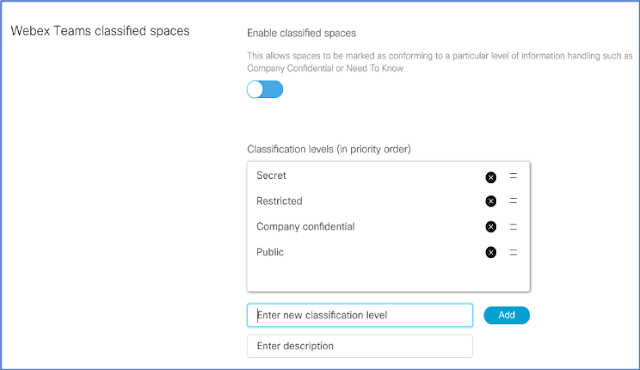
New Webex Space Classifications
Webex space classifications can help enable companies to safeguard content by labeling spaces and then having 100 characters of explainer text for each.
Figure 2 – Webex Teams space classifications
Webex administrators can set up any five labels that they want within Control Hub. Many companies will elect to set their policies around security – for instance:
◉ Public
◉ Private
◉ Confidential
◉ Highly confidential
◉ Restricted
And then the creator of the space would label and add up to 100 characters of explainer text for each space he or she creates.
Additionally, Webex administrators can build data loss prevention policies in their Cloud Access Security Broker – using the APIs that Webex provides – for instance – they could prohibit file uploads in a space that’s classified as “Top Secret.” Or they can set up policies for when users collaborate with someone outside of their company – and those external users will get an alert that the space they are entering has a classification.
Users also have the ability to elevate the space classification – but they can’t lower the space classification. For instance, if someone in a space starts introducing confidential information in a public space, the creator or space owner could change that space classification to “confidential.”
Unparalleled Security for Remote Work
Whether it’s the ability to secure mobile devices so users can safely use Webex on the go, or granular tools to prevent data leakage – Cisco has unparalleled security to secure your remote work force.