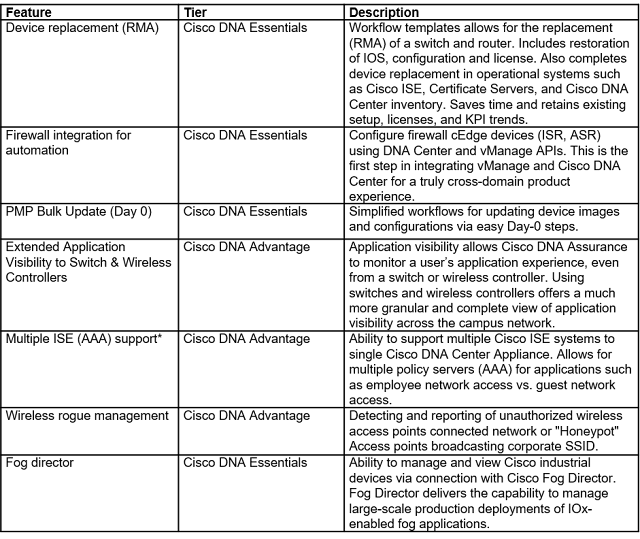
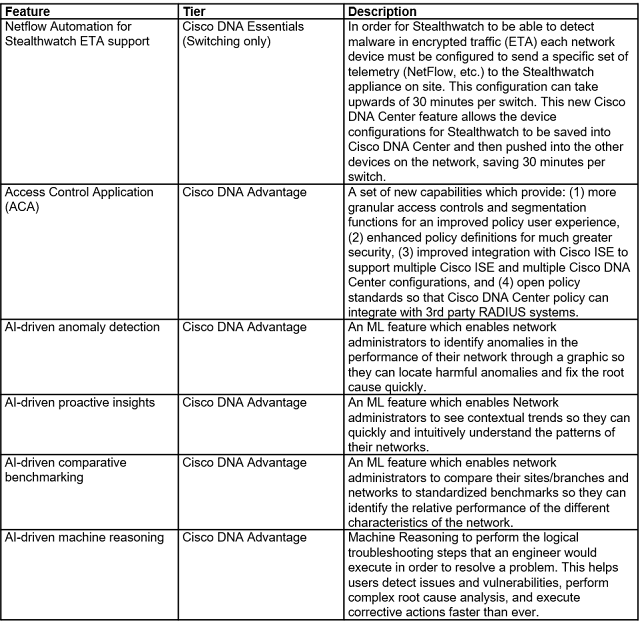
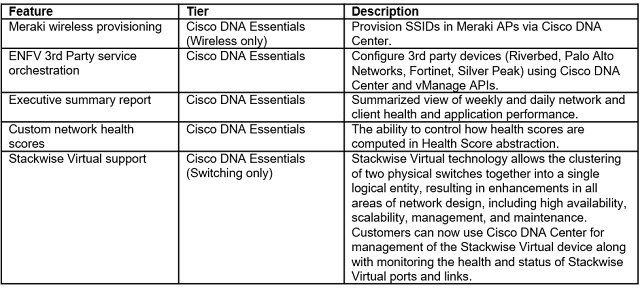
As pandemic restrictions ease, we’re working to manage a safer return to the office. Our strategy includes monitoring workspace density. If people are maintaining the recommended distance, we’ll consider inviting more people back. If not, we’ll pause.
This blog is an update to the initial plans I shared in Helping to keep employees safe by measuring workspace density with Cisco DNA Spaces. As I write this, we’re using Cisco DNA Spaces to monitor workplace density in 20 Cisco offices, including several in Asia Pacific and Europe. Here are our experiences after the first few months, and what’s ahead.
Before using Cisco DNA Spaces to monitor workspace density, we needed to confirm that most people in our buildings connect at least one device—phone, tablet, or laptop. In the first offices to open, Seoul and Beijing, we assigned people to count the number of people entering and exiting each floor lobby. The count closely matched the Cisco DNA Spaces count, giving us the confidence to move ahead.
This blog is an update to the initial plans I shared in Helping to keep employees safe by measuring workspace density with Cisco DNA Spaces. As I write this, we’re using Cisco DNA Spaces to monitor workplace density in 20 Cisco offices, including several in Asia Pacific and Europe. Here are our experiences after the first few months, and what’s ahead.
Counts are accurate
Before using Cisco DNA Spaces to monitor workspace density, we needed to confirm that most people in our buildings connect at least one device—phone, tablet, or laptop. In the first offices to open, Seoul and Beijing, we assigned people to count the number of people entering and exiting each floor lobby. The count closely matched the Cisco DNA Spaces count, giving us the confidence to move ahead.
To make sure we don’t count one person with a connected laptop, tablet, and phone as three people, Cisco DNA Spaces groups all devices that log in with the same username. Privacy is a top priority at Cisco, so we don’t capture or store the username. Instead it shows up as a string of random characters (a hash) that can’t be mapped back to a person.
Grouping devices by username was one of our suggestions as “Customer Zero.” While we’re not the first company to use Cisco DNA Spaces, we are the first to use it to monitor workspace density to plan a safer return to work. As Customer Zero we’re giving the DNA Spaces product team our feedback as a customer so they can continually improve the product. We’re also sharing our experiences with other customers, as I’m doing here, to help them get the most value from their own deployments.
More accurate than the access-control system
Before the pandemic, our Workplace Resources (WPR) team estimated building occupancy based on data from the access-control system. But badge-in data has limitations for measuring workplace density. One problem: it doesn’t report when people exit the building. If 500 people enter a building throughout the day, at 4:30 p.m. there could be 500 people (dense)—or 100 (less dense). Another drawback of badge data is that readers typically are only at the building entrance—not on each floor. We don’t know if everyone is on one floor or they’re spread out across all floors.
Cisco DNA Spaces solves both problems. We can see how many people are present right now. And we can also see which floor people are on. We can even divide floors into zones, measuring density by zone.
What if people are too close?
The sooner we find out that too many people are in a particular zone, the sooner we can take action to get back to target density. Using the DNA Spaces Right Now app, we entered rules—for example, no more than 20 people in building 14, floor 1, zone A. if that rule is broken, the app sends an alert to the specified teams—via email, in a Webex Teams space, or another system. Our WPR team prefers Webex Teams alerts so they don’t have to worry about missing an email.
Beyond density measuring
During the pandemic our WPR team is cleaning surfaces more frequently. They can see which areas are the most heavily trafficked (and need more frequent cleaning) by checking the Right Now app. Some of our other ideas:
◉ Show floor occupancy to employees to help them decide when and where to work. We plan to integrate Cisco DNA Spaces with digital signage and our employee self-check app for COVID-19 symptoms, Cisco Office Pass. Employees will see historical occupancy of different areas of the building at different times. (You might have seen this on store and hospital ER websites). We’ll use Cisco DNA Spaces Firehose API to integrate with digital signage and the mobile app.
◉ Bring more kinds of sensor data into Cisco DNA Spaces, such as Cisco Meraki door intrusion sensors and cameras.
◉ Report the location of things as well as people. We could track expensive engineering and test equipment, for example, and alert security staff when wireless devices leave the building with someone other than their registered owner.
◉ Provide wayfinding (aka blue-dot navigation) on a mobile app. We’re already trying this out in the Cisco LifeConnections Health Center.
◉ Improve safety during disasters. When a building is evacuated, we can check if any devices remain connected to Wi-Fi. We’re thinking that employees who want to associate their name with their location will be able to opt in.
Lesson learned: check if building maps are accurate
Here’s a lesson learned from our experience as Customer Zero. Be sure to double-check access point locations, height, and orientation on building maps before uploading the maps to DNA Spaces. In our case, inaccurate building maps complicated deployment for the first few buildings. The maps had “drifted” over time as building layouts changed and access points were installed and moved. If an access point isn’t where you think it is, the reported location of devices connected to that access point won’t be accurate.