Thursday, 22 June 2023
The Value of SOC2 and ISO27001 in Enhancing Customer Trust
Wednesday, 21 June 2023
The Cisco DCCOR 350-601 Exam: What to Expect and How to Prepare
Cisco Systems is an internationally renowned company that specializes in internet networking. Its extensive range of networking solutions has greatly benefited businesses in various industries by offering essential services and communication products. The need for skilled professionals who are certified in managing and enhancing IT systems and infrastructure within companies is on the rise. The CCNP Data Center DCCOR 350-601 certification equips individuals with the necessary skills and knowledge to address technical and operational challenges at different stages and devise effective solutions.
Overview of the Cisco DCCOR 350-601Certification
The exam has a duration of 120 minutes, during which candidates will encounter a variety of question formats, including multiple-choice, drag-and-drop, and simulations. The number of questions in the exam can range from 90 to 110. To take the DCCOR 350-601 exam, candidates are required to pay a fee of $400. The exam is conducted in English.
The DCCOR 350-601 exam encompasses a diverse array of subjects pertaining to data center technologies. Several prevalent topics that are addressed in this examination comprise:
Cisco DCCOR 350-601 Exam Preparation Resources
To effectively prepare for the Cisco DCCOR 350-601 exam, it is crucial to leverage a combination of study materials and resources. Here are some recommended resources that can enhance your preparation process:
1. Cisco Official Certification Guide
The Cisco Official Certification Guide is an authoritative resource covering all exam objectives comprehensively. It offers in-depth explanations, real-world examples, and practice questions to help you grasp the concepts and reinforce your knowledge. Study this guide thoroughly and use it as a reference throughout your preparation journey.
2. Cisco Learning Labs
Cisco Learning Labs provides a hands-on experience by offering virtual environments to practice various data center technologies. These labs enable you to gain practical skills and reinforce your understanding of the concepts covered in the exam. Take advantage of these labs to get hands-on experience with Cisco equipment and familiarize yourself with real-world scenarios.
3. Cisco Online Communities and Forums
Engaging with online communities and forums dedicated to Cisco certifications can be immensely beneficial. These platforms allow networking professionals to connect, share experiences, and seek guidance. Active participation in discussions will enable you to gain valuable insights, learn from other's experiences, and clarify doubts.
4. Cisco DCCOR 350-601 Practice Exams
Practice exams are invaluable resources for gauging your exam readiness. These resources simulate the exam environment and help you identify areas to improve. Regularly practicing with these materials can enhance your time management skills and help you become familiar with the question formats, ensuring a smoother experience on exam day.
5. Training Courses
Consider enrolling in an official training course for the Cisco DCCOR 350-601 exam preparation. These intensive programs provide expert-led training, hands-on labs, and comprehensive study materials. The structured approach offered by these courses can significantly streamline your learning process and ensure you cover all the exam objectives effectively.
Effective Exam Preparation Tips
1. Create a Study Plan
Develop a well-structured study plan to make the most of your preparation time. Start by assessing your current knowledge and identifying areas that require more focus. Allocate dedicated study sessions and set realistic goals for each session. Breaking the topics into manageable chunks ensures comprehensive coverage and prevents last-minute cramming.
2. Follow a Systematic Approach
Adopting a systematic approach to studying is vital for success. Begin by understanding the foundational concepts and gradually progress to more complex topics. Take notes, create mind maps, and use visual aids to reinforce your understanding. Revise previously covered topics regularly to maintain a solid grasp of the material.
3. Utilize Active Learning Techniques
There may need to be more than passive reading to retain information effectively. Employ active learning techniques such as summarizing concepts in your own words, discussing topics with study partners, or teaching the material to someone else. These techniques promote a more profound understanding and long-term retention of the subject matter.
4. Hands-on Practice
There must be more than just theory to excel in the Cisco DCCOR 350-601 exam. Devote time to hands-on practice with data center technologies. Set up a virtual lab environment using tools like Cisco Packet Tracer or GNS3 to gain practical experience configuring and troubleshooting network devices. Practical application of the concepts enhances your understanding and builds confidence.
5. Review and Reinforce
Regularly reviewing the material you have covered is crucial for retention. Set aside dedicated time for review sessions where you revisit previous topics, answer practice questions, and identify any areas that need further reinforcement. Utilize flashcards or create summary sheets to condense essential information and facilitate quick revision.
6. Take Care of Yourself
Exam preparation can be intense and demanding, but prioritizing self-care is essential. Get enough sleep, eat well-balanced meals, and engage in physical activities to keep your mind and body in optimal condition. Taking breaks and managing stress effectively will improve your overall well-being and focus during study sessions.
Conclusion
Achieving success in the Cisco DCCOR 350-601 exam requires diligent preparation and leveraging the right resources. Following a well-structured study plan, utilizing recommended resources, and adopting practical exam preparation tips can enhance your knowledge, boost your confidence, and increase your chances of attaining a favorable outcome. Remember, continuous learning and practical application of the concepts are vital to becoming a proficient network engineer in the dynamic world of data centers.
Start your journey today with Cisco DCCOR 350-601 exam preparation, and unlock new opportunities in the ever-evolving networking field.
Tuesday, 20 June 2023
Security automation with Cisco XDR
Response Playbooks
- Identification – Review the incident details and confirm that a breach of policy has occurred.
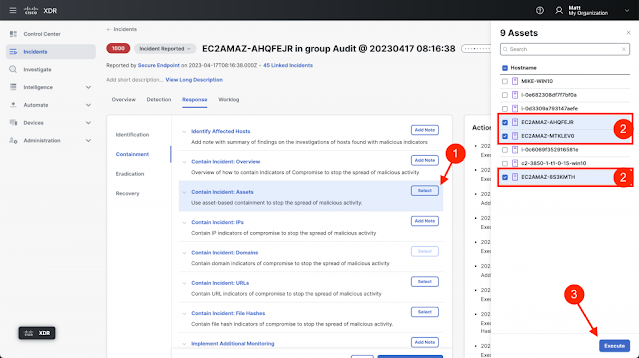
- Containment – Prevent malicious resources from continuing to impact the environment.
- Eradication – Remove the malicious artifacts from the environment.
- Recovery – Validate eradication and recover or restore impacted systems.
Automated Workflows
- Approval Task – Take response actions after an approval task is approved, or notify the team if a request is denied.
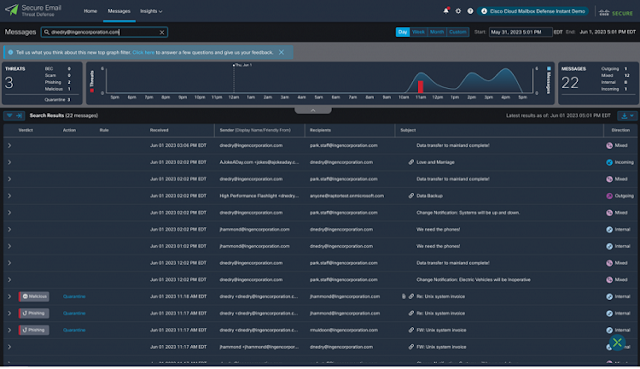
- Email – Investigate suspicious or user-reported emails as they arrive in a spam or phishing investigation mailbox.
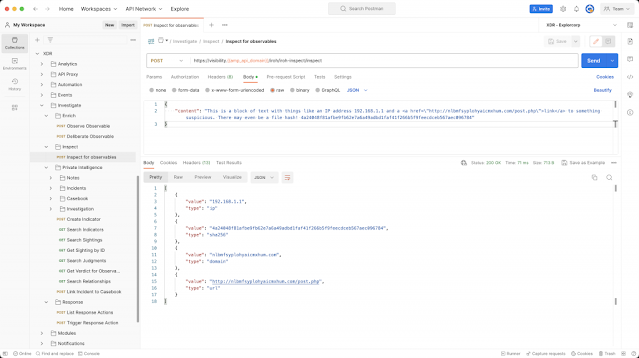
- Incident – Enrich incidents with additional context, take automated response actions, assign to an analyst, push data to other systems like ServiceNow, and more.
- Schedule – Automate repetitive tasks like auditing configurations, collecting data, or generating reports.
- Webhook – Integrate with other systems that can call a webhook when something interesting happens. A message being sent to a bot in Webex, for example.