In 2024, digital methods of payment are outpacing cash. 3D printers are becoming a fixture in implant surgery and AI is adding color to the world for people who are visually impaired, using just a phone—and the network.
Society expects and depends on an ever-increasing fusion of digital and physical experiences for everyday life and business progress. This dependency is apparent in the 2024 Cisco Global Networking Trends Report, which shows a continued correlation between network investment in fueling digital experiences and the benefits felt by organizations.
When the 2,000+ IT leaders surveyed were asked about their network investment and results over the past 12 months, they quickly pointed to a clear uptick in every key business metric: increased customer and employee satisfaction, improved operational efficiency, and business growth.
The road to success has been bumpy.
Driving transformation while on empty
IT is at the helm of delivering digital experiences, and the pressure is more intense than ever. Network architectures are more sophisticated, more complex, and spread across more multiclouds and multi-vendors than ever. IT leaders are also besieged by rising cybersecurity risks, increased demand from new app and workload types, and vastly distributed workforces and infrastructures.
Even more, over a third of respondents use multiple, separate management systems or ad hoc integrations when managing their campus, branch, WAN, data center, and multicloud architectures.
Identifying or solving just one network issue is currently a dizzying swivel-chair operation as IT teams hop between various management systems. Some respondents even admit they currently have no API-driven network ecosystem integrations today, meaning these management systems are working independently and inefficiently.
After years of grappling with point solutions deployed during the pandemic, that in part led to current IT challenges, there have been bright spots.
Over a third (39%) of IT leaders shared that they currently use a platform architecture across some networking domains and strongly support platform adoption. They see the value of a platform approach leading to faster IT and business innovation (43%), improved network performance and security posture (40%), and cost savings (37%). Also clear is that a platform equals the simplicity of having software, policy, open APIs, advanced telemetry, and automation all in one place.
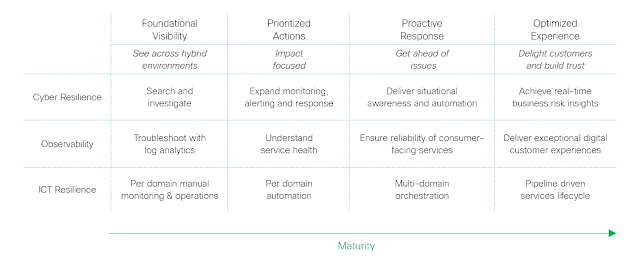
So, it’s no surprise that respondents said 72% of their organizations will adopt a network platform to handle one or more network domains within two years. Even more, 39% of them expect to scale across all networking domains, as shown in the maturity model below.
Figure 1: This graphic compares the status of network maturity today vs. where respondents expect to be in two years.
Blind spots ahead
Deploying and managing digital experiences and ensuring everything is up and working—at scale—is top-of-mind for IT, and it hasn’t proven easy.
Providing service reliability to ensure predictable and consistent user experiences is an area for significant improvement for 41% of respondents. A key factor is the lack of visibility into complete network paths, including internet and cloud networks, according to 35% of respondents. IT leaders feel hampered in assuring the digital experience and achieving digital resilience across owned and unowned infrastructure—more on this from me at Cisco Live 2024.
The alarms are going off
As digital experiences and the network scales, so does the threat landscape. According to the report, 40% of IT leaders cite cybersecurity risks as their number one concern impacting network strategy over the next 12 months. They’re looking to combat these threats in a few ways.
First is integrating network and security processes, technology, and tools, with half of respondents making this their top network security investment over the next two years. Second is moving more security tools to the cloud to protect the increasingly distributed infrastructure and workforce better.
Like cybersecurity, we can’t have a conversation in 2024 without AI.
Speeding ahead with AI
The promise of AI is the needed reprieve for IT organizations struggling with a lack of resources and automation to handle basic operational tasks. Only 5% of respondents believe their teams are equipped to deliver the innovations needed to help steer business strategy, satisfy customers, and optimize operations.
Within two years, 60% expect AI-enabled predictive automation across all domains to manage and simplify network operations.
Data center upgrade plans for greater throughput and scalability to meet the AI need include enhanced Ethernet (56% of respondents). 59% of respondents also plan to simplify their data center network operations with AIOps within two years.
This is just a snippet from the 2024 Global Networking Trends Report. It provides a critical perspective from IT leaders who must ensure the network delivers secure digital experiences for all. One thing is clear: the network continues to be in the driver’s seat for digital experiences and a catalyst for business transformation.
Source: cisco.com