Supporting applications at the edge with high-performance, easy to manage UCS C240 SD M5 Server
As more data and processing needs exist and are growing rapidly at the edge, providers and customers are exploring methods to avoid the bandwidth, latency, and overall costs of backhauling content to the traditional data center. Instead, the industry is moving towards enabling the more intense computational needs closer to where this data and content is gathered and presented.
According to IDC (1), 50% of new enterprise IT infrastructure deployed will be at the edge by 2023, and there will be an 800% increase in the number of apps at the edge by 2024. The industry is already looking for innovative methods to uniformly operate in this greatly scaled out environment.
We talked with many customers looking at these needs in areas such as service providers, hosting providers, enterprise branch, retail, defense, and many others, they have shared some common requirements:
◉ Solution optimized for a compact and tactical environment
◉ Simple on-boarding to management and orchestration tools by non-IT personnel
◉ Autonomous operations, with an ability for simple periodic updates
◉ Easy access and maintenance by non-IT personnel
◉ Performance that traditionally resides within today’s Data Center
◉ Enhanced security to operate within shared-use multi-access facilities
◉ Flexible options along with global 24×7 support
Cisco used these customer requirements to guide us as we developed a new UCS server platform for our customers. Our teams have been working hard on this problem and we are excited to announce the new Cisco C240 SD M5 server.
Introducing the Cisco UCS C240 SD M5
The Cisco UCS C240 SD M5 is available today and delivers a performance edge solution integrated with our Cisco Intersight offering to allow the same advantages in edge that existing Cisco customers consume in their data centers today.
The Cisco UCS C240 SD M5 delivers the following key capabilities for customers:
◉ Simplicity: Easy deployment and connection to network and power
◉ Turnkey: Simple onboarding into already defined policy
◉ Cloud or Virtual Appliance Managed: Simple Intersight claiming, Cloud or Connected/Private Virtual Appliance
◉ Economic: Match workload density needs to ratio’s only seen inside traditional DC with full performance – while fewer device touches and full Intersight management means reduced operational costs
◉ Future Proof: Standard peripherals and accelerators supported as rest of UCS line
◉ Agile: Intent based Intersight template definition of many edge sites from a single policy
◉ Complete Stack at Edge: When combined with HX and HXAP (both of which will be available late 2020 on the C240 SD M5) you have platform for full stack management to match storage, SD-WAN, servers, network all in a coordinated fashion
Optimized for a compact and tactical environment
The Cisco UCS C240 SD M5 is built for environments within and outside a traditional data center with some key points below. The C240SD M5 Server:
◉ Can be stacked up to 4 high without racking – or in 2 and 4 post racks
◉ Can be installed against rear wall with minimum 6” rear clearance
◉ Is just under 22” deep
◉ Can be powered by 120/240VAC or -48VDC
◉ Users can connect 2 nodes together directly with 10GE cable for workload live-migration
◉ Can be deployed with 1 or 2 Intel Xeon SP processors (configuration options will change)
◉ 24 DIMM slots supporting up to 256GB DDR4, or add 128/256/512GB PMEM modules to a maximum of 9TB
◉ 2-6 SAS/SATA/NVMe Drives, 2 M.2 Drives
◉ 2-6 PCIe slots (Gen3 with 2 x16, 4 x8)
◉ Will have future NEBS L3 qualification
◉ Unit has optional internal M.2 boot drives
◉ Has a tamper-evidence device that will raise alarms in multiple management systems
◉ FCS operation up to 10,000 ft, testing in progress to 13,000 ft
◉ FCS temp range from 10-40C, testing in progress to 50C (and peripheral options come into play)
◉ Shock in operation a 10g, and non-operational to 20g
Simple on-boarding to management and orchestration tools by non-IT personnel
In order to gain the advantage of remote installations without IT staff travel, Cisco has invested in methods to ease the onboarding of the C240 SD M5 both in situations where a pre-staging can be done, and also developing a low-touch deployment that will be allow direct shipments to remote sites. These methods will allow remote staff who have limited compute expertise to perform an installation of the Cisco edge solution. Some key elements include:
◉ Staging Intersight pre-claim today
◉ Intersight onboarding directly by non IT remote staff in near future
◉ Remote config setup, validation, and OS installation via policy
◉ Operational analytics
In summary the customer can stage at a partner today, units for global deployment, or in near future just deploy at these global locations with no staging required. All state to be installed on that server (config, options, OS/Hypervisor, Analytics, etc.) can be done not only remotely – but in the policy already defined within Intersight.
Autonomous operations, with an ability for simple periodic updates
In many of these types of edge deployments, having a model that is not connected to the cloud is a mandatory element. Cisco has many deployment models starting with simple stand-alone device management through our Cisco Integrated Management Controller that can be configured via multiple scripting and API methods. To take this further, based on our customer requirements we have developed the Intersight Connected Virtual Appliance which maintains a relationship with Cisco for real-time analytics and support, or the Private Virtual Appliance that has no connectivity back to Cisco. The latter provides isolation in the customer environment much like perpetual isolated software components common today.
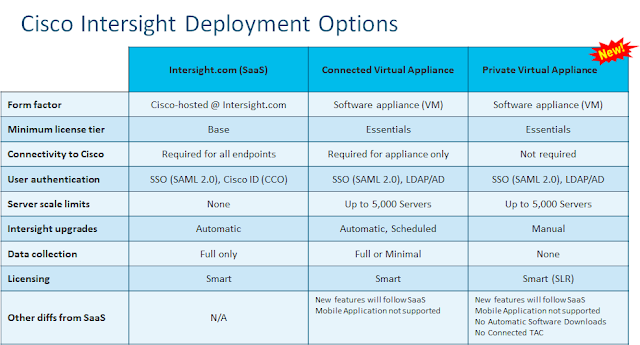
To allow a capability of keeping updates for latest support and features ,the connected appliance can operate disconnected for up to 90 days – when the connection can be re-established, or in the case of the private appliance disconnected for same duration before customers are asked to update the appliance via a downloaded package.
Easy access and maintenance by non-IT personnel
The C240 SD M5 has a key advantage of all front access, where only rear components are the redundant fan modules. The components allow for easy replacement with easy access should maintenance be required.
Performance that traditionally resides within today’s Data Center
In many edge platforms today, the processing and peripheral/storage needs are much smaller for far edge points of the environment. Using those platforms to address the performance needs of hosting workloads, processing of data and video, transcoding, etc. are forcing higher processing and peripheral needs into the space between DC and edge. The Cisco UCS C240 SD M5 fits into that space and offers the performance of the full suite of most Intel Xeon SP models, Intel N3000 FPGA devices, nVidia T4 devices, up to 6 PCIe slots (2 x16), SAS/SATA or in combination with 6xNVMe.
As customers look to deploy SD-WAN solutions that include edge sites, methods to store large amounts of data where it is generated at the edge, process that data at the edge, our solution when combined with HyperFlex and HyperFlex Application Platform in the coming quarter will provide a full-stack solution to those locations with a single point of management and analytics.
Enhanced security to operate within shared-use multi-access facilities
As the data, business processing, and key Intellectual Property move outside the well-defended DC into these edge locations, the ability to secure these elements moves from an over the top add-in into a integrated strategy. Cisco UCS C240 SD M5 bases our security in our Cisco ACT2 technology that validates the hardware, the booting process, all firmware components up the stack. Cisco also supports Self Encrypting Drives in this solution, so that a unit will brick if removed. Cisco also includes tamper sensing within the solution that will allow central alarming.
Flexible options along with global 24×7 support
Customers we have talked with envision using the C240 SD M5 offering in combination of bare metal workloads, container workloads, standard virtual server hosting, Cisco HyperFlex solution, and more generally in a variety of storage heavy or PCIe dense deployments.
Cisco has multiple methods in the C240 SD M5 for sharing support information with Cisco TAC, including the fully connected TAC offering inside Intersight. All of the benefits of Cisco Intersight from an infrastructure automation and orchestration perspective are available to the C240 SD M5 at launch.
Customer Focused, Operate at Scale
Customers desire a platform for performance edge needs that is agile, simple, and economic. The new Cisco UCS C240 SD M5 delivers on that promise by providing a turn-key platform that is simple to deploy and operate and reduces the burden of IT staff. Future options for new acceleration technologies, driven by Intersight intent based policy and centrally managed will remove significant roadblocks to a modern performance edge. Operating at the scale of thousands or higher is much more straightforward with the UCS C240 SD M5 and Intersight together.