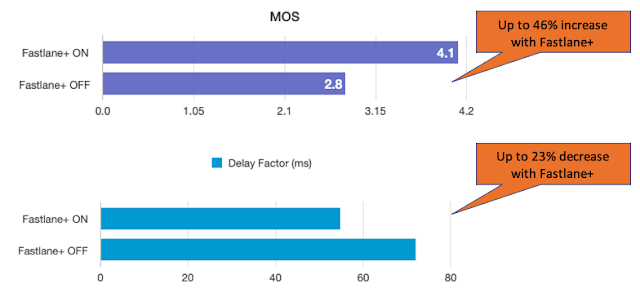
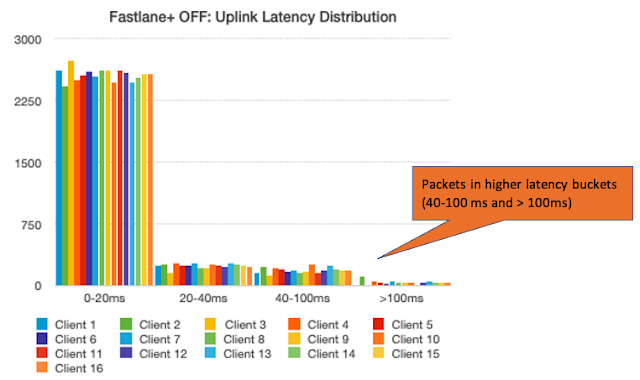
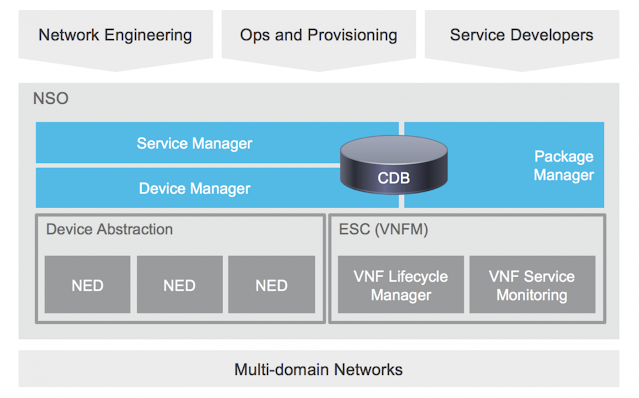
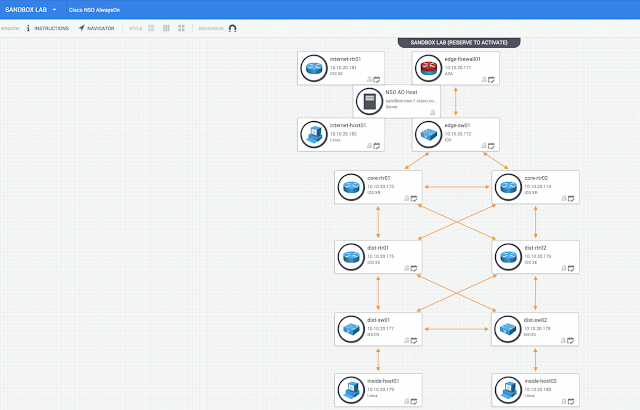
IT professionals in financial services have been instrumental to ensuring the integrity of global financial markets over the last year. Their hard work has helped keep the world’s largest economies working and financial aid flowing to those who need it most.
For them, few things remain unchanged from the pre-COVID world. Many network engineers had their hands full supporting large scale migrations to remote working. But aside from that, one constant during this time of change is that IT budgets are not increasing. “Do more with less,” “Reduce costs,” and “Extract more value,” are a few common mantras. The message is clear—each dollar spent on IT projects must have a tangible business benefit associated with it. With this increased focus on efficiency and cost, now is the perfect time for financial services companies to consider investing in cloud-based IT.
Benefits of cloud-based IT
Migrating IT infrastructure to a cloud-based platform can help improve efficiency and reduce costs for finserv companies by accelerating business processes, simplifying technology, and boosting operational efficiency. Today’s reality has required businesses to rethink how to help their employees collaborate safely while working from remote locations as they begin the return to work. By leveraging cloud-based solutions, workers and IT support teams are able to troubleshoot issues quicker, reduce downtime, and lower costs both for employees and for the end-customer.
Supporting rapid change
Before COVID, financial services companies were embarking on their cloud journey in pockets, with the primary focus on software development environments and connections to provide staff with secure connectivity. The rapid changes required for companies to function during the early days of the pandemic necessitated quick adoption of cloud-based technologies for enterprise voice, contact centers, remote access and network security. Projects that would have taken weeks or months were now being done in hours or days, driven by a need to get lines-of-business operational and keep companies viable. Now that the industry has successfully dealt with the crises of 2020, and have been operating in the new normal for several months now, a few trends have emerged that will drive IT decisions going forward— including preparing for a return to work and facilitating future growth.
Preparing for return to work
While bank branches never closed, most campuses and offices did. Optimistic news around vaccine development and distribution has led many companies to prepare for the return to work and reconsider the landscape for the office environment.
For example, adding cameras could help ensure compliance around masks and social distancing policies. Access sensors could help track room occupancy and ensure timely and consistent sanitation practices. In a traditional environment, implementing such practices could take up to a year. However, by taking advantage of the ability to configure a network and add components to that network without configuration of individual components, we can continue to meet the accelerated timelines required for the return to work.
Scaling for the future
Traditional companies deal with mergers and acquisitions, but for financial services companies, growth is typically purchased. Network teams are not revenue generators, and as a result, mergers have historically been underfunded and understaffed. The inevitable outcome of years or decades of that reality is a patchwork quilt of networks that are all sort-of connected. Each legacy organization retains some idiosyncrasies, issues, and non-standard hardware that requires specialized support personnel. That complexity leads to lower velocity than what lines-of-business have come to expect throughout the pandemic. With everything needed to deploy a branch, campus, or office network, cloud adoption takes advantage of the appetite that company departments have developed for speed. This emphasizes the critical need to scale for the future growth of financial services companies and the need for simplicity.All in all, the events of 2020 have been a catalyst for change and digital transformation within the financial services sector. Cisco Meraki offers solutions to address the challenges that come with such abrupt changes including facilitating the campus and client network, creating operational efficiencies, and reducing downtime and loss of revenue.
Source: cisco.com