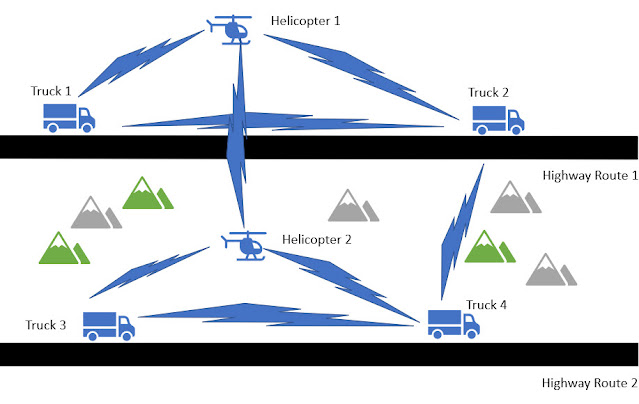
Cisco Radio Aware Routing addresses several of the challenges faced when merging IP routing and radio communications in mobile networks, especially those exhibiting ad hoc (MANET) behavior. This technology has applications in the defense industry as well as state and local government for search and rescue, law enforcement, and disaster assessment.
Saturday, 19 March 2022
Cisco Radio Aware Routing
Thursday, 17 March 2022
Unified Software Tracing Comes to Cisco IOS XE – It’s Unified, Binary, Streaming, and Highly Scalable
Software tracing is essential for Cisco’s team of enterprise networking software engineers, along with the legions of developers, systems admins, and tech support personnel among our customers. Tracing is the specialized use of logging to capture the operational behavior of code down to the code execution path. It’s indispensable for developers for troubleshooting network software in production to catch bugs, errors, misconfigurations, or other problems throughout the birth and lifecycle of products.
Cisco has provided a more efficient and effective way to use network software traces at scale for our 80+ enterprise platforms. It’s called unified tracing.
With unified tracing, all traces deployed in software running anywhere in the system (e.g., in line cards or other field replaceable units [FRUs]), are streamed to the main processor of the Cisco device and collected in a single set of files. This integration of trace messages provides time-ordered, real-time visibility into what a router, switch, wireless controller, or Internet of Things (IoT) device is doing across its approximately 100 processes.
Here’s how we’ve ramped up tracing in a big way and what it means for enterprise networking.
Tracing Gets Binary in Cisco IOS XE 16.0
Release 16.x introduced binary tracing to the Cisco IOS XE code base. It’s now widely used.
Binary tracing relies on compiler technology to assist in the encoding of each trace point, allowing for the storage of non-ASCII text objects, like packets and software-generated objects in the trace stream. These binary objects provide richer operational information about how network platforms are performing.
Fully distributed, binary tracing also enables tracing on steroids, with some Cisco enterprise platforms able to exceed peak trace rates of two million traces per second per process. It also separates the encoding of high-performance traces from the decoding of traces, which can be displayed to users later.
Unified Tracing introduced in Cisco IOS XE Release 17.7
With binary tracing alone, each process writes traces independently to separate files. If you have 100 processes, you have 100 separate sets of files, which slows down troubleshooting.
With unified tracing, all trace files for a system are merged into one trace file set of messages with all of the information about their origins (Figure 1). Each trace event uniquely identifies the calling site information and carries context to know where in the system and the source code it was produced.
Features and Benefits of Unified Tracing
More Meaningful, Scalable Traces
Tuesday, 15 March 2022
Randomized and Changing MAC (RCM)
What is Randomized & Changing MAC (RCM)
Historically wireless clients associate to the wireless network using the manufacturer assigned mac address that is associated with the wireless network interface card (NIC). This manufacturer-assigned mac address, which is globally unique, is also known as burn-in address (BIA). Use of this burn-in address everywhere raises the question of end-user privacy as the end-user can be tracked with WIFI’s mac address. In this document, this will be referred to as normal mac (address), in contrast to the random mac (address).
To improve end-user privacy, various operating system vendors (Apple iOS 14, Android 10 and Windows 10) are enabling the use of the locally administered mac address (LAA), also referred to as the random mac address for WIFI operation. When wireless endpoint is associated with random mac address, the MAC address of the endpoint changes over time.
The random mac address was limited to probe for known wireless networks. This is now expanded to association to the wireless networks. While this works well for the privacy of the end-user, it brings unique challenges to the Enterprise IT admin, who has been depending so far on the unique endpoint identity as the basis for driving policies. This will also affect different WIFI deployment models e.g., Guest, BYOD (Bring Your Own Device) and location analytics, etc. which rely on the uniqueness of the mac address.
To address and alleviate the issues due to the usage of random MAC addresses in the existing wireless deployments, Cisco provides an RCM solution.
Random Mac Identification and Client access
MDM (Mobile Device Manager)/ISE BYOD Integrations:
DNA Center visibility, Troubleshooting, Usage tracking for RCM
Future of Random MAC Solution
Sunday, 13 March 2022
Introducing the new ‘Defending Against Critical Threats’ report
Today, we’re pleased to launch our annual Defending Against Critical Threats report. Inside, we cover the most significant vulnerabilities and incidents of 2021, with expert analysis, insights and predictions from our security and threat intelligence teams across Cisco Talos, Duo Security, Kenna Security, and Cisco Umbrella.
It’s clear that 2021 – and, indeed, the start of 2022 – has been very challenging for security defenders. To bring our Defending Against Critical Threats: Analyzing Key Incident Trends report to life, I sat down with six expert threat hunters and analysts from these teams, and asked them to tell me about their findings on one specific cybersecurity threat, or incident, from the past 12 months. Each expert chose to discuss a topic which tells us a lot about the current priorities of threat actors – below you’ll find a brief summary on some of the key themes we covered.
We also conducted a survey among 190+ security and technology leaders via PulseQA to gauge their perspectives on the current threat landscape. We found that 66% of respondents felt that the complexity and volume of cybersecurity attacks had escalated in 2021, whilst 36% felt that attacks had stayed consistent with the previous year.
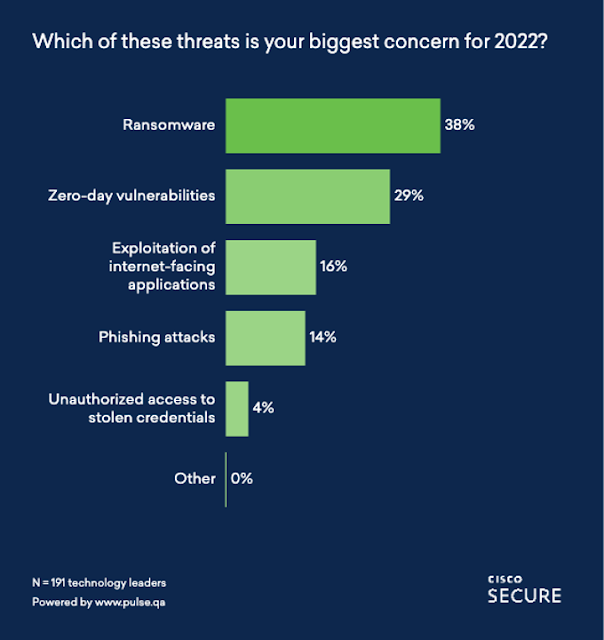
In the survey, we also asked about the top threat concerns security leaders had for 2022. Ransomware came in as the top concern, with 38% of respondents choosing that option. In the report, we discuss the evolution of ransomware and how it has reached a critical level for certain bad actors, provoking a more severe and structured governmental response. You’ll read about this in Matt Olney’s (Talos’ Director of Threat Intelligence and Interdiction) section about the Colonial Pipeline attack.
Here’s what we cover in the new Defending Against Critical Threats:
Thursday, 10 March 2022
Focus on HyperFlex: Sizing A New Cluster Using the Sizer and Profiler Tools
In this ‘Focus on HyperFlex’ blog, we’ll zero-in on different aspects of the Cisco HyperFlex (‘HX’) hyperconverged system and ways to make HX work best for you and your organization. This edition will illustrate on how to size a cluster when you might not have all the details of the workload worked out. In this situation, HyperFlex Profiler is the right approach to learn more about the workloads.
During my time in sales, teams often asked me to size a HyperFlex cluster and provide a customer quote. It was customary to have many more questions than the team or customer could answer about the application. Normally, they would provide me with an Excel sheet with some CPU and memory values. That is a great start, and it gave me deep insight into the customer’s application. However, an application profile is not only about averages of CPU and memory. There are several more parameters needed, including the performance and latency peaks. With the customer’s permission, I would run a HyperFlex Profiler in their environment to gain more information about their application. Before installing the OVA on their vCenter, I would explain what HyperFlex Profiler is and how it helps with sizing their new HyperFlex environment.
HyperFlex Profiler
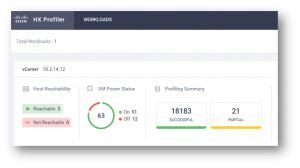
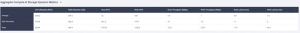
If there is no historical insight into the potential clustered application environment, then start with HyperFlex Profiler. HyperFlex Profiler will gather data on the vCenter environment and consolidate that mass of data to a single, easily digestible file. This file will quickly size the cluster after importing it into the HyperFlex Sizer tool and paint a clearer picture of the environment and workloads.
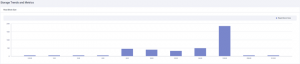
However, profiling the environment is not a quick hit in a short period of time. The best approach is to run the HyperFlex Profiler for at least seven days or, preferably, 30 days. A longer measuring period ensures you capture data when “end of the month reports” are run. Of course, don’t just measure the environment during a weekend when there is little traffic! Be sure to capture at least one logical business cycle for that application.
The HyperFlex Profiler is an OVA installed on a VMware environment. The only configuration is to provide (read-only) access to the vCenter environment and define which servers the HyperFlex Profiler will monitor. Multiple servers and/or clusters can be selected. For environments running different types of workloads, it is recommended to isolate them by selecting the servers in their environments – for instance, the VDI or the SQL environment. Of course, selecting all servers and workloads is also an option. Keep in mind that you will have more overhead this way.
When it is monitoring the environment, you will see the following:
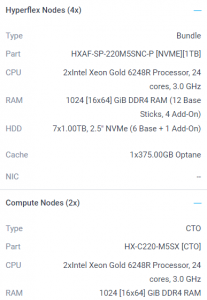
HyperFlex Sizer
Create an estimate
Tuesday, 8 March 2022
EIS in Transition: Impacts on Digital Transformation for Federal Networks
For Federal agencies, Enterprise Infrastructure Solutions (EIS) has provided a comprehensive, solution-based method to address their IT telecommunications and infrastructure needs. Over the years, EIS has seen many changes that directly impact stakeholders. But its primary purpose as a key driver for the digital transformation of enterprise telecommunications and networking solutions remains unchanged. Yet many agencies, such as Networx and WITs, face contract expirations on May 31, 2023. To maintain momentum for digitization, Federal agencies must begin the transition now by strategically mapping how and where it should start.
What’s next for Federal Digital Transformation?
For decades, Cisco has built a strong relationship with the U.S. Federal Government. Our portfolio of products, solutions, and services provide Federal agencies with the critical technology and support they need to enable the transformation of their networks within the EIS contract.
By leveraging these existing contracts, agencies are reducing costs and acquisition time. They’ve been able to digitize aging systems and catch-up to the private sector in capabilities. But now what? Which direction should Federal agencies go as they transition contracts within EIS? The simple answer: Cisco SD-WAN.
Beyond EIS with SD-WAN
Cisco SD-WAN is the premier choice for replacing expensive and aging legacy WAN. Federal agency networks leveraging Cisco’s SD-WAN solution can benefit from:
◉ Enhanced user experience
◉ Reduced costs
◉ Simplified operations
◉ Improved performance
◉ And robust security.
Cisco SD-WAN enables more efficient bandwidth allocation, powering critical applications to faster, smoother performance. This capability is now a necessity as Federal agencies move to cloud services and witness an explosion of app-wielding users connecting remotely.
Wi-Fi6 for the Federal Government
Partnering for the future of EIS
Monday, 7 March 2022
Cisco 300-435 ENAUTO | Syllabus | Exam Overview | Questions | Study Guide
Cisco ENAUTO Exam Description:
Cisco 300-435 Exam Overview:
- Exam Name- Automating and Programming Cisco Enterprise Solutions
- Exam Number- 300-435 ENAUTO
- Exam Price- $300 USD
- Duration- 90 minutes
- Number of Questions- 55-65
- Passing Score- Variable (750-850 / 1000 Approx.)
- Recommended Training- Implementing Automation for Cisco Enterprise Solutions (ENAUI)
- Exam Registration- PEARSON VUE
- Sample Question- Cisco 300-435 Sample Questions
- Practice Exam- Cisco Certified DevNet Specialist Enterprise Automation and Programmability Practice Test