Saturday, 30 September 2023
When it Comes to Compliance Requirements – Topology Matters!
Thursday, 28 September 2023
Cisco Contact Center Delivering Visibility to Improve the Banking Experience
Customer feedback
- Streamlining the agent desktop – fewer discrete apps and better app data integration
- Extracting intelligent insights from full visibility of cross-channel customer journeys
- Providing agents with the best guidance and options in real-time
- Utilizing best-in-class workforce management and automation
Cisco expertise
Webex by Cisco
Tuesday, 26 September 2023
Evolutio FinTech module on Cisco FSO Platform gives visibility to financial transactions
We’re all aware that user experience has become the most important KPI for today’s digital businesses. Applications are the engines that power these experiences, and if a digital interaction is sub-par, customers are unforgiving. Consider the situation of a prominent bank that recently suffered a series of downtimes on its mobile applications. Their users were not happy and rival credit unions were advertising, highlighting their level of service compared to the “mega-bank.” Churning customers due to digital blips is a NO-NO today. Organizations need visibility, context and control, so they can ensure that their customers are empowered with the best experiences possible. But true observability requires more than a “one size fits all” approach. Today’s application environments are highly specialized, built to support specific industries and business processes.
Observability tailored to fit specific use cases
Given the diversity and complexity of today’s modern apps, how can organizations fully align their technology to specific use case needs? Cisco FSO Platform brings data together from multiple domains including application, networking, infrastructure, security, cloud, sustainability, and business sources. It is an open and extensible, API-driven platform focused on OpenTelemetry and anchored on metrics, events, logs, and traces (MELT), providing AI/ML driven analytics.
The Cisco ecosystem of partners plays a key role in enabling this flexibility by creating custom observability solutions that help customers drive business outcomes with specific use cases. Let’s take a closer look at the Evolutio Fintech module, built by a key Cisco technology partner.
Evolutio Fintech gives holistic visibility to online financial transactions
Every moment matters in financial services, especially in online and point of sale transactions. Financial services organizations need to be able to see the full picture—and take action with insight.
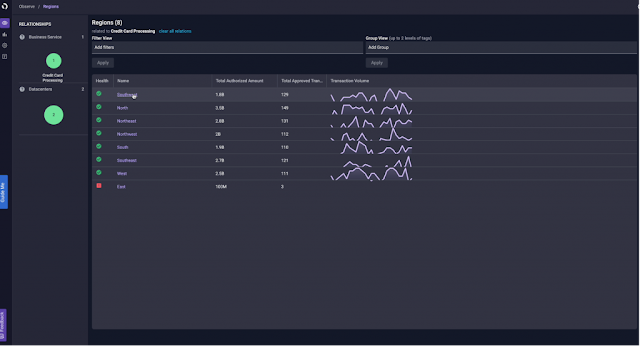
The Evolutio Fintech module correlates infrastructure health with credit card authorization data. It helps organizations reduce revenue losses resulting from credit card authorization failures by figuring out the impact of infrastructure health on the credit card authorization.
“We developed a Fintech solution for the banking sector, around credit card processing,” said, Laura Vetter, CTO and Co-Founder of Evolutio. “It looks at credit card processing, how much money is running through, and the number of transactions, split by customer region data centers, which is most relevant to the business. If someone calls in and has an issue with processing, it’s easy to look at that specific company’s data and determine whether the issue involves the whole company, or just one region.”
A powerful partnership for technology innovators
Wednesday, 20 September 2023
CCNP Enterprise 350-401 Certification: The Road to Success
Greetings, fellow networking enthusiasts! Prepare to embark on a journey that not only promises to unlock a world of exciting career opportunities but also validates your prowess in networking. This comprehensive guide is your trusted companion, offering insights into the coveted Cisco CCNP Enterprise 350-401 certification. We'll explore its advantages and provide invaluable study tips to ensure a pass and excellence in this prestigious examination.
Know the Cisco CCNP Enterprise 350-401 Certification
Let's begin by unraveling the essence of the Cisco 350-401 ENCOR certification. CCNP, or Cisco Certified Network Professional, Enterprise, is a prized accolade for networking professionals aspiring to showcase their mastery in enterprise networking solutions.
Cisco 350-401 Exam Details:
- Exam Name- Implementing and Operating Cisco Enterprise Network Core Technologies
- Exam Price- $400 USD
- Duration- 120 minutes
- Number of Questions- 90-110
- Passing Score- Variable (750-850 / 1000 Approx.)
Cisco 350-401 Exam Topics:
- Architecture- 15%
- Virtualization- 10%
- Infrastructure- 30%
- Network Assurance- 10%
- Security- 20%
- Automation-15%
Benefits of Cisco CCNP Enterprise 350-401 Certification
Expansive Career Horizons
Acquiring the Cisco CCNP Enterprise 350-401 certification opens various career opportunities. Organizations worldwide seek professionals capable of designing, implementing, managing, and troubleshooting advanced enterprise network solutions. You become an invaluable asset in the job market.
Industry Recognition
Cisco certifications, including CCNP Enterprise, are synonymous with excellence in the field. Employers and peers recognize them as symbols of top-tier networking expertise. This certification instantly bestows credibility and underscores your commitment to staying at the forefront of networking technology.
Elevated Earning Potential
CCNP Enterprise-certified professionals typically enjoy enhanced earning potential—the specialized skills and knowledge acquired through the certification process position you for higher-paying roles in the industry.
Skill Mastery
Cisco's CCNP Enterprise certification equips you with in-depth knowledge of critical networking topics. This mastery enhances your problem-solving abilities and bolsters your confidence in effectively managing enterprise networks.
Why Should You Pass Cisco 350-401 ENCOR Exam?
Preparing for Success: Study Tips for 350-401 ENCOR
Now that we've established the perks let's dive into the core aspect of attaining CCNP Enterprise certification: preparation. Follow these study tips to ensure you conquer the 350-401 ENCOR exam with flying colors.
#1. Grasp the 350-401 Exam Blueprint
Before you commence your preparation, familiarize yourself with the exam blueprint. Cisco provides a detailed breakdown of the topics and subtopics covered in the exam. Use this blueprint as your roadmap to guarantee comprehensive coverage.
#2. Source Quality 350-401 Study Materials
Invest in reputable study materials, such as Cisco's official certification guides and practice exams. Additionally, consider engaging with online forums and communities where you can collaborate with fellow candidates, share insights, and access valuable resources.
#3. Craft a Study Schedule
Effective time management is paramount. Create a study schedule tailored to your daily routine, allowing consistent, focused study sessions. Allocate specific time slots for different topics to ensure thorough preparation.
#4. Hands-On Practice
More than theoretical knowledge is required. Establish a lab environment using tools like Cisco's Packet Tracer or other network simulation tools. Hands-on practice solidifies your understanding of networking concepts and reinforces your practical skills.
#5. Join Study Groups
Consider joining or forming study groups with like-minded individuals pursuing the same certification. Collaborative learning can be remarkably effective, enabling discussions on complex topics, joint troubleshooting, and exposure to diverse perspectives.
#6. Regularly Take 350-401 ENCOR Practice Tests
#7. Annotate and Summarize
While studying, take notes, annotate textbooks, and create concise summaries of key concepts. This reinforces your understanding and provides quick references during the final stages of preparation.
#8. Stay Informed
Stay abreast of the latest networking trends and Cisco technologies. The field constantly evolves, and exam questions may reflect these changes. Subscribe to Cisco blogs, newsletters, and forums to stay informed.
#9. Seek Expert Guidance
When confronted with challenging topics or concepts, feel free to seek guidance from seasoned professionals or certified trainers. They can offer valuable insights and clarify any doubts that impede your progress.
The Final Push: Cisco 350-401 ENCOR Exam-Day Strategies
Prioritize Relaxation
The night before your exam, prioritize a restful night's sleep and relaxation. Avoid last-minute cramming, as it can heighten anxiety and hinder performance. Trust in your preparation and maintain confidence.
Read Carefully
During the exam, meticulously read each question to ensure a clear understanding of the requirements before answering. Cisco exams often feature scenario-based questions that demand a profound grasp of the subject matter.
Master Time Management
Effective time management is paramount. Allocate specific time limits to each question, and if you encounter a particularly challenging one, move on and return to it later. Don't let a single question consume excessive time.
Review Your Answers
Once you've completed the exam, revisit your answers if time permits. Check for errors or omissions and make necessary corrections.
Conclusion
The Cisco CCNP Enterprise 350-401 certification is your ticket to a flourishing networking career. Its manifold benefits, including expanded career opportunities, industry recognition, and higher earning potential, make it a wise investment in your professional journey.
By adhering to these comprehensive study tips, you can confidently approach the 350-401 ENCOR exam and emerge triumphant. Remember, preparation is the key, and steadfast commitment to your studies will lead you to success.
So, gear up, embark on your certification, and unlock the gateway to networking excellence. The Cisco CCNP Enterprise 350-401 certification is within your grasp, and with dedication and determination, you can attain it. Best of luck on your journey to becoming a certified networking professional!
Thursday, 14 September 2023
How to run Cisco Modeling Labs in the Cloud
Setting expectations
- Tooling is currently only supported on AWS. We’re working on making this also available on Azure in a subsequent release.
- It only supports an all-in-one deployment. Subsequent releases could include deployment of multiple instances to form a CML cluster.
- This approach needs a bare-metal flavor to support all node types. Metal flavors are more expensive than virtualized instances; however, AWS does not support virtualization extensions on their non-bare-metal flavors. This is different from Azure.
- You need to bring your own AWS instance AND your own CML license. No pay-as-you-go consumption model is available as of today.
- CML software and reference platform files from the “refplat ISO” need to be made available in a bucket.
- Automation must run locally on your computer, particularly a Linux machine with Terraform.
Meeting software requirements
- a Linux machine (should also work on a Mac with the same packages installed via Homebrew)
- a Bash shell (in case you use the upload tool, which is a Bash script)
- a Terraform installation
- the AWS CLI package (awscli with the aws command)
- the CML software package (.pkg) and the CML reference platform ISO from CCO/cisco.com
Getting up and running
Taking the next steps
Tuesday, 12 September 2023
Cisco Catalyst IE9300 Rugged Series switches: Enterprise-grade industrial-strength
A new class of industrial rackmount switches
One switch family, unlimited possibilities
Use cases for the Catalyst IE9300 Rugged Series Switches
- High density fiber access. Fiber ports offer several benefits over copper. Fiber cables are immune to electromagnetic radiation, offer safer transmission in hazardous conditions due to their electric isolation, and can transmit data over much longer distances without experiencing signal degradation or loss of quality. Use cases for fiber include industries such as utilities that are modernizing substations using native fiber devices, and traffic backhaul from field deployments.
- Clock input and precision timing. GPS and IRIG-B inputs that allow network synchronization ensure that different devices across the network are working with the same time reference, which is crucial for applications requiring coordinated actions. For example, in energy sectors, accurate time synchronization is crucial for monitoring power grid events, fault detection, and grid stability. Further, Precision Timing Protocol (PTP) Power Profile built into the IE9300 ensures 50ns per-hop accuracy that keeps the delay within 1µs over 16 switch hops.
- Aggregation and cost-efficiency. 10G uplink fiber aggregation switch makes it possible to connect Resilient Ethernet Protocol (REP) and Media Redundancy Protocol (MRP) rings in non-climate-controlled field points-of-presence. This use case has broad potential in field deployment such as in roadways, wind, and solar farms. The 10G uplinks help avoid oversubscription that could occur in Gigabit only switches.
- Distribution layer switching. Uplink ports open new opportunities for IE9300 to be used as distribution layer switches that you can deploy right in dusty and hot environments ensuring that critical data flows smoothly between access switches and the core network. Stacking capabilities of IE9300 ensure scale and redundancy.
- High-wattage and high-density PoE. Copper models of IE9300 offer a variety of PoE options and can provide power to connected devices with a total of up to 720W per switch. Note that the IE9300 delivers 720W of PoE power while still maintaining a 1RU form factor, a first in the industry. Moreover, you can configure the switch to deliver up to 90W on a single 2.5GE port. This combines high bandwidth with high-power on a single port enabling new use cases.
- Flexibility and scalability. Although the IE9300 switches have a fixed port count, and multiple units can be stacked to increase the number of available ports while still appearing virtually as a single switch, which reduces configuration complexity. Management by Cisco Catalyst Center makes onboarding and reconfigurations easy, increasing flexibility to keep pace with operations.
- Visibility and security. Granular visibility into connected assets and network traffic is the necessary first step in ensuring operations security. Compute capabilities within the IE9300 allow it to run Cisco Cyber Vision sensors that provides visibility, risk assessments, and helps form the basis for network segmentation for security.